Pegasus you thought I was off the mark - I wasn’t -absolutely stunning reporting by Washington Post
NSO Group Pegasus
First I recommend you read today’s Washington Post Article
The numbers on the list are unattributed, but reporters were able to identify more than 1,000 people spanning more than 50 countries through research and interviews on four continents: several Arab royal family members, at least 65 business executives, 85 human rights activists, 189 journalists, and more than 600 politicians and government officials — including cabinet ministers, diplomats, and military and security officers. The numbers of several heads of state and prime ministers also appeared on the list.
If you understand how the Internet Wayback works, then you know to give the link a few moments to fully populate an archived Twitter thread. It takes a few moments for the Wayback to pull up the whole thread.
November 2019 this tweet caused a five day suspension - Guess Twitter was mad that I might haven been one of the 1st accounts that said: WTFINGF you hired 2 infiltrators from the Kingdom and gave them the Administrative Keys to .your user database and dashboard - yea that got me locked down for five days.
In December of 2019 - I specifically pointed to TikTok and PAX-AI - because I noticed there was a shared source code. Archive found here
In January of 2020 - I then pointed to the UNHCR’s report and how MbS (likely) deployed Pegasus on Jeff Bezos’ personal phone. It was detailed in the UNHCR Report, Twitter thread archived (give it a few minutes to populate the entire thread) or here
2016 - 2018 Pegasus had proliferated into 45 countries.. several that had either “previously been linked to abusive use of spyware to target civil society” or had “dubious human rights records & histories of abusive behaviour by state security services“
Did it occur to folks that I wasn’t being hyperbolic with this thread? That maybe I was screaming into the abyss that NSO & Pegasus & QTech not exactly the trifecta of goodness? January 23, 2020 Twitter Archive - this twtext unroll of one of my many threads kind of gives you a better understanding of the arch of the research
Washington Post Article NSO Group Q-Technologies
See the following excepts from today’s Washington Post Article
Among the journalists whose numbers appear on the list, which dates to 2016, are reporters working overseas for several leading news organizations, including a small number from CNN, the Associated Press, Voice of America, the New York Times, the Wall Street Journal, Bloomberg News, Le Monde in France, the Financial Times in London and Al Jazeera in Qatar.
The targeting of the 37 smartphones would appear to conflict with the stated purpose of NSO’s licensing of the Pegasus spyware, which the company says is intended only for use in surveilling terrorists and major criminals. The evidence extracted from these smartphones, revealed here for the first time, calls into question pledges by the Israeli company to police its clients for human rights abuses.
Amnesty International Forensic Methodology Report:
How to catch NSO Group’s Pegasus - REPORT
If you want the technically aspects of what the Washington Post used in their published article - I highly recommend you read today’s Amnesty International Report (AIR) which was published contemporaneously to the Post Article. To say AIR’s report is stunning - that might be an understatement but my followers knew on 2019 thru 2020 that NSO and their (now rebranded) Pegasus spyware was far more pernicious than most thought —because for months (mainly in 2019 I was told I was wrong about Pegasus, MbS and Putin)
The Pegasus attacks detailed in this report and accompanying appendices are from 2014 up to as recently as July 2021. These also include so-called “zero-click” attacks which do not require any interaction from the target. Zero-click attacks have been observed since May 2018 and continue until now. Most recently, a successful “zero-click” attack has been observed exploiting multiple zero-days to attack a fully patched iPhone 12 running iOS 14.6 in July 2021.
Sections 1 to 8 of this report outline the forensic traces left on mobile devices following a Pegasus infection. This evidence has been collected from the phones of HRDs and journalists in multiple countries.
Finally, in section 9 the report documents the evolution of the Pegasus network infrastructure since 2016. NSO Group has redesigned their attack infrastructure by employing multiple layers of domains and servers. Repeated operational security mistakes have allowed the Amnesty International Security Lab to maintain continued visibility into this infrastructure. We are publishing a set of 700 Pegasus-related domains.
Discovering Pegasus network injection attacks and Pegasus’ BridgeHead and other malicious processes appear
Hey remember that time when people laughed about my tweets concerning injection and how this spyware essentially self unloaded on a target device —meaning the target didn’t need to click a link, picture or document…Pegasus once deployed acted with autonomy… to wit I was jeered - yes super fun times. You ding dongs I read the various UNHCR, Amnesty International Reports and then cross referenced with the Public Court Docket…
However, on further analysis we also noticed suspicious redirects recorded in Safari’s browsing history. For example, in one case we noticed a redirect to an odd-looking URL after Maati Monjib attempted to visit Yahoo…
As explained in the Technical Appendix of our 2020 report on Pegasus attacks in Morocco, these redirects do not only happen when the target is navigating the Internet with the browser app, but also when using other apps. For example, in one case Amnesty International identified a network injection while Omar Radi was using the Twitter app. When previewing a link shared in his timeline, the service com.apple.SafariViewService was invoked to load a Safari WebView, and a redirect occurred.
Pegasus’ Bridgehead
…based on the domain names and other network infrastructure used to deliver the attacks. However, forensic evidence left behind by the Pegasus spyware provides another independent way to attribute these attacks to NSO Group’s technology.
…iOS maintains records of process executions and their respective network usage in two SQLite database files called “DataUsage.sqlite” and “netusage.sqlite” which are stored on the device. It is worth noting that while the former is available in iTunes backup, the latter is not. Additionally, it should be noted that only processes that performed network activity will appear in these databases.
Both Maati Monjib’s and Omar Radi’s network usage databases contained records of a suspicious process called “bh”. This “bh” process was observed on multiple occasions immediately following visits to Pegasus Installation domains.
Note the Dates and iOS sample size
The last recorded execution of “bh” occurred a few seconds after a successful network injection (as seen in the favicon records listed earlier at 2019-09-13 17:01:56).
Crucially, we find references to “bh” in the Pegasus iOS sample recovered from the 2016 attacks against UAE human rights defender Ahmed Mansoor, discovered by Citizen Lab and analysed in depth by cybersecurity firm Lookout.
As described in Lookout’s analysis, in 2016 NSO Group leveraged a vulnerability in the iOS JavaScriptCore Binary (jsc) to achieve code execution on the device. This same vulnerability was also used to maintain persistence on the device after reboot. We find references to “bh” throughout the exploit code…
The data forensic here are incredible and meticulously cataloged - back tracing to the Pegasus Installation Server and noting the favicon entry was key because that’s what’s colloquially known as a digital breadcrumb trail. Because the disablement of the targets phone to no longer send crash reports to Apple…
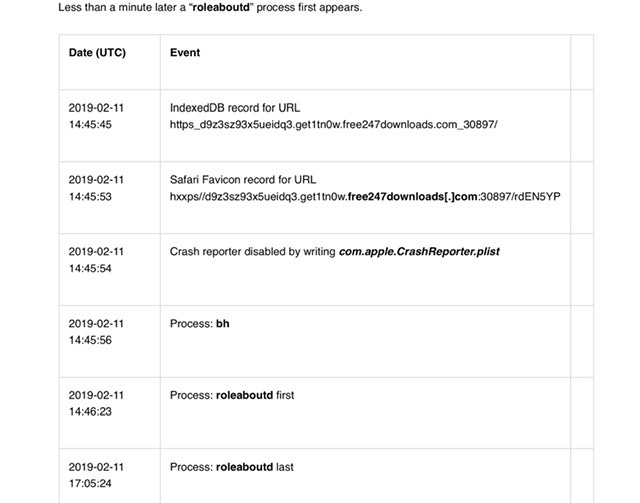
Additional suspicious processes following BridgeHead…bh process first appeared on Omar Radi’s phone on 11 February 2019. This occurred 10 seconds after an IndexedDB file was created by the Pegasus Installation Server and a favicon entry was recorded by Safari. At around the same time the file com.apple.CrashReporter.plist file was written in /private/var/root/Library/Preferences/, likely to disable reporting of crash logs back to Apple. The exploit chain had obtained root permission at this stage.
Less than a minute later a “roleaboutd” process first appears.
Based on the timing and context of exploitation, Amnesty International believes the roleaboutd and msgacntd processes are a later stage of the Pegasus spyware which was loaded after a successful exploitation and privilege escalation with the BridgeHead payload.
Similarly, the forensic analysis of Maati Monjib’s phone revealed the execution of more suspicious processes in addition to bh. A process named pcsd and one named fmld appeared in 2018:
Pegasus Cyber Darwinism
Trust me on this - read section 4 of the Amnesty International Report carefully because I had to reread it 3 times just to ensure I was reading it correctly
The discovery of network injection attacks in Morocco signalled that the attackers’ tactics were indeed changing. Network injection is an effective and cost-efficient attack vector for domestic use especially in countries with leverage over mobile operators. However, while it is only effective on domestic networks, the targeting of foreign targets or of individuals in diaspora communities also changed.
Amnesty International extended its forensic methodology to collect any relevant traces by iMessage and FaceTime. iOS keeps a record of Apple IDs seen by each installed application in a plist file located at /private/var/mobile/Library/Preferences/com.apple.identityservices.idstatuscache.plist. This file is also typically available in a regular iTunes backup, so it can be easily extracted without the need of a jailbreak.m
…the first suspicious processes performing some network activity were recorded 5 minutes after the first lookup. The com.apple.CrashReporter.plist file was already present on this device after a previous successful infection and was not written again.
The insidious nature of Pegasus and exploits in Apple products is unnerving—not only can this spyware self unload but turning off crash reporting is a way for Pegasus to continue running and exfiltrating a targets data on their iPhone/iPad and they don’t even know they are being spied upon.
SMS to iMessage to FaceTime -Pegasus migrates to Apple Music to leveraged to deliver spyware
This is not only bad —it is breathtaking both in terms of shifting on the fly but NSO’s brazenness and the targeting of hundreds of journalists and activist. Can we stop pretending now and agree that NSO & QTech and their customers are likely breaking international laws concerning privacy and undermining of the free press - but on a global scale?
In mid-2021 Amnesty International identified yet another case of a prominent investigative journalist from Azerbaijan (CODE AZJRN1) who was repeatedly targeted using Pegasus zero-click attacks from 2019 until mid-2021.
Amnesty International cannot determine from forensics if Apple Music was itself exploited to deliver the initial infection or if instead, the app was abused as part of a sandbox escape and privilege escalation chain. Recent research has shown that built-in apps such as the iTunes Store app can be abused to run a browser exploit while escaping the restrictive Safari application sandbox.
Someone needs to put Pegasus Down like Old Yeller clip Pegasus’ wings and tango down their …
Below is a truncated listed of the various servers Amnesty International and their research partners discovered NSO Group’s DNS servers hosted with each hosting provider:
Digital Ocean has142,
AMAZON-02 has 73
LineCode LLC has 114
According to additional analysts by Amnesty International:
NSO Group made critical operational security mistakes when setting up their Version 3 infrastructure. Two domains of the previous Version 2 network were reused in their Version 3 network. These two Version 2 domains, pine-sales[.]com and ecommerce-ads[.]org had previously been identified by Citizen Lab. These mistakes allowed Amnesty International to link the attempted attack on our colleague to NSO Group’s Pegasus product. These links were independently confirmed by Citizen Lab in a 2018 report.
Appendices:
Appendix A: Peer review of Methodology Report by Citizen Lab: has independently peer-reviewed a draft of the forensic methodology outlined in this report. Their review can be found here.
Appendix B: Suspicious iCloud Account Lookups
Appendix C: Detailed Traces per Target - This Appendix contains detailed breakdowns of forensic traces recovered for each target. This Appendix will be progressively update…This Appendix shows the overlap of iCloud accounts found looked-up on the mobile devices of different targets. This list will be progressively updated.
Appendix D GitHub Repository 1407 Domains Affiliated with Pegasus:NSO Group Pegasus Indicator of Compromise indicators include:
domains.txt: list of all Pegasus-related domains, with sub-files:v2_domains.txt: list of Pegasus Version 2 infrastructure. These domains were identifed and published previously by Citizen Labv3_domains.txt: list of Pegasus Version 3 infrastructurev4_domains.txt: list of Pegasus Version 4 infrastructurev4_validation_domains.txt: list of Pegasus Version 4 validation/URL shortener domainsemails.txt: list of iCloud accounts used for exploiting zero-click vulnerabilities in iMessage and other Apple appsfiles.txt: list of suspicious filespegasus.stix2: STIX v2 file containing IOCs that can be used with MVTprocesses.txt: list of Pegasus-related process names identified on compromised phones
NSO Group’s Annual Report
I say this with zero respect intended -NSO Group can go fuck themselves with a rusty gate spike -their audacity and temerity is without equal - June 30, 2021 NSO-Bullshit-Report - so Spying on hundreds of reporters, human rights advocates and other governments didn’t make it in your June 2021 Report. Gee I wonder why…also I probably would NOT Click the NSO Group’s Annual report - setting aside its on a Wordpress platform - for obvious reasons —unless you’re okay with NSO having unrestricted access to your smartphone or tablet or laptop
The entirety of NSO Group’s range of products have been conceived, researched, developed and taken to market with only one simple end-result in mind: the preservation of safety, and the notion that all people should be afforded security and safety in their homes, at work, or out amongst their fellow citizens. We often explain publicly that our products are designed for use by legitimate, vetted, state-administered intelligence and law enforcement organizations. While this remains as true as ever, we must also be assured that all of our sales, and all of the customers who make use of their NSO Group product licenses, are exactly aligned with our ultimate goal: public safety and security.
I will probably return to this subject but felt a sense of responsibility to my longtime followers/readers - it’s amazing how some of us in 2019 said watch this space and here we are…
















Imma gonna leave this Khashoggi archive thread right here too
https://web.archive.org/web/20201021180123/https://twitter.com/File411/status/1318975557917396994
And this twunroll thread right here too
https://twunroll.com/article/1318975557917396994#
I didn’t connect dots because I was pushing a narrative - I connected the dots because that’s where the facts landed me. At the time it was kind of obviously that Jared Kushner likely (unwittingly) brought Pegasus right into the inner sanctum of our White House - so chew on that fun nugget of awful
God, I remember these threads, especially the shared code. You broke it down so long ago and finally here it is.