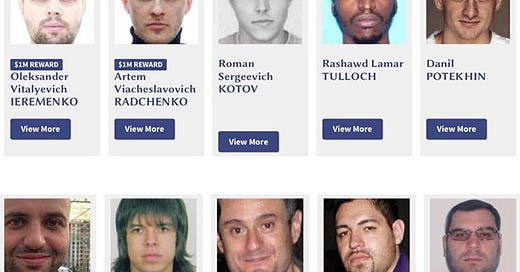
US Secret Service Releases 'Most Wanted' Cyber Fugitive List
USSS now Offering $1 Million Rewards for Information on 2 Ukrainian Suspects/Fugitives Ieremenko and Radchenko
Oleksandr Vitalyevich Ieremenko aka Александр Витальевич Еременко, “Zl0m,” “Lamarez”
USSS Fugitive Ieremenko Profile
In February 2010, Oleksandr Ieremenko and other co-conspirators engaged in an international computer hacking and fraudulent securities trading scheme whereby they:
a) hacked into the computer networks of Marketwired, PR Newswire, and Business Wire;
b) stole confidential press releases containing material non-public information from the victim companies’ internal computer networks prior to their public release; and
c) traded ahead of the material non-public information contained in the stolen releases before its distribution.
During the course of the scheme, Ieremenko and his co-conspirators accessed more than 150,000 stolen releases and executed profitable trades based on the material non-public information contained in the stolen releases. In total, the scheme generated more than $30 million in illicit trading profits. I tweeted a lot about this fugitive, see Twitter thread archive
Artem Viacheslavovich Radchenko aka Артем Вячеславович Радченко
…,2016 through on or about March 2017, Artem Viacheslavovich Radchenko recruited Oleksandr Vitalyevich Ieremenko and other hackers in Ukraine and managed their criminal efforts to enrich themselves through a sophisticated securities fraud scheme. Ieremenko successfully hacked into the computer networks of the U.S. Securities and Exchange Commission (SEC) and extracted valuable data regarding the financial earnings of publicly traded companies. Again on Twitter I followed the Iremenko & SEC case kind of obsessively because it linked to Nikulin’s case
Roman Sergeevich Kotov aka Роман Сергеевич Котов, “zSeven,” “7even”
From August 2005 through on or about July 2012, Roman Kotov and other co-conspirators operated a prolific hacking organization that was responsible for several of the largest known data breaches.
penetrated the secure computer networks of several of the largest payment processing companies, retailers, and financial institutions in the world, and stole the personal identifying information of others.
unlawfully acquired over 160 million credit card numbers as a result of their hacking activities.
defendants referred to as "dumps" – hacker shorthand for card numbers and associated data, Kotov and his co-conspirators sold the dumps to "dumps resellers" around the world, who, in turn, sold them either through online forums or directly to other individuals and organizations.
Raswd Lamar Tulloch aka “Userplaygame00,” “Uxsr,” “Uxsrfone”
July 5, 2018 a Federal Grand Jury returned a 24-count indictment charging 15 foreign nationals with; Racketeer Influenced and Corrupt Organizations Act (RICO) conspiracy, wire fraud conspiracy money laundering conspiracy, and aggravated identity theft.
The charges stemmed from the defendants' roles in an international organized crime group based primarily in Alexandria, Romania, that defrauded American victims through online auction fraud, causing millions of dollars in losses.
February 6, 2019, a federal grand jury in Lexington returned an 11-count indictment charging an additional foreign national and four Americans, including Rashawd Lamar Tulloch, for their roles in the same criminal enterprise. Tulloch served as a third-party money launderer and managed an operation designed to receive, redeem, and convert victim payments, obtained as result of the Romania-based fraud network, into bitcoin or cash.
the. SUPERSEDING INDICTMENT (or via my public drive) returned in open court as to Beniamin-Filip Ologeanu (1) counts 1s-3s; Austin Edward Nedved (2) counts 1, 4-5; Dimitrious Antoine Brown (3) counts 1, 6-8; Rashawd Lamar Tulloch (4) counts 1 & 9; Andrew Gilbert Ybarra, II (5) counts 10-11. Forfeiture allegations not included on the docket sheet as not statistically counted. (KM) (Additional attachment(s) added on 2/7/2019: # 1 Sealed Unredacted Superseding Indictment
Danil Potekhin aka Данил Потехин, “cronuswar”
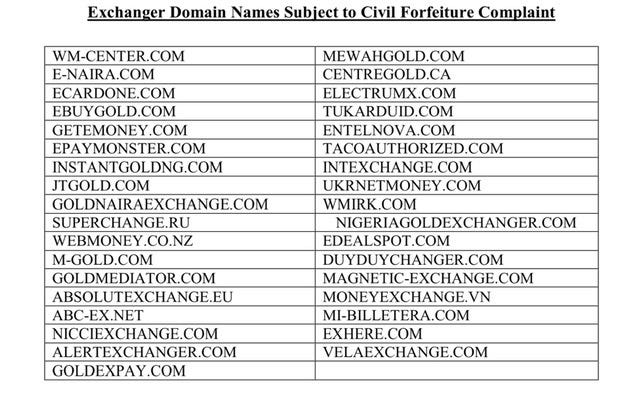
June 2017 through on or about April 2018, Danil Potekhin and Dmitrii Vadimovich Karasavidi launched a sophisticated phishing campaign targeting users of multiple digital currency exchanges. Potekhin and Karasavidi purchased and deployed multiple web domains that appeared to be websites belonging to legitimate digital currency exchanges.
October 29, 2017, the defendants took control of the three victim customer accounts and used the digital currency contained in those accounts, with a value of over $5 million at that time, to purchased GAS at the same time, which increased demand and price.
The defendants and their co-conspirators then quickly converted the digital currency in their fictitious accounts from GAS to Bitcoin and other digital currencies, causing the value of GAS to plummet and leaving the value of GAS that remained in the victim customer accounts worthless, causing a loss to these three victims of approximately $5 million.
Superseding indictment also alleges similar fraud schemes that took place between October 2017 and March 2018, and which resulted in theft attacks targeting victim customers of another U.S.-based digital currency exchange and one based abroad. The value of the stolen digital currency at the time of the thefts was over $11 million.
And lastly the Superseding Indictment alleges the defendants laundered the proceeds of the attacks and attempted to conceal the nature and source of the digital currency by transferring them in a layered and sophisticated manner through multiple accounts. Ultimately, a significant amount of the stolen digital currency was deposited into Karasavidi’s account.
Dmitrii Vadimovich Karasavidi aka Дмитрий Вадимович Карасавиди
(as noted above) Potekhin and Karasavidi were able to steal the users’ credentials, enabling the defendants to control the actual digital currency exchange accounts, withdraw some or all of the victims’ digital currency, and manipulate the market for digital currency. This tactic used a combination of phishing and spoofing to exploit users’ trust in known companies and organizations, with the ultimate purpose of fraudulently obtaining victim login credentials. The scheme resulted in losses of digital currencies valued at approximately $17 million.
Farkhad Rauf Ogly Manokhin aka Фархаду Рауфу Оглы Манохину, Fedor Raufovich, “fr.usa”
On March 26, 2015, a federal grand jury in the Southern District of Florida returned an indictment charging Farkhad Rauf Ogly Manokhin with operating a money laundering network that facilitated cash transfers on behalf of a Russia-based malware development organization (GozNym - I didn’t have any luck finding the SDFL indictment but I linked to the 20!9 indictments via WDPA)
Manokhin recruited and maintained a network of money mules…Manokhin then used the network of mule accounts (he helped recruit and establish) to offer cash-out services for illicitly obtained funds from bank account takeovers, enabling the perpetrators to wire the illicit funds into the mule accounts. Manokhin notified the mules and their handlers of the timing and amounts of wire transfers of money from victim bank accounts into the mule bank accounts, directed them to make cash withdrawals from the mule bank accounts, and provided the dollar amounts, names, and locations of persons to whom the illicit funds should be sent.
Ahmed Yassine Abdelghani aka Ahmed Mekovar, “Alex”
SUPERSEDING INDICTMENT FILED (ECF) as to Arthur Budovsky (4) count(s) 1s, 2s, 3s.
May 28, 2013, the Southern District of New York unsealed charges against Liberty Reserve, a company that operated one of the world’s most widely used digital currency services, and seven of its principals and employees with money laundering and operating an unlicensed money transmitting business.
Back in 2019 thru my 2021 Twitter suspension I had a lot to say about Liberty Reserve, see archived Twitter thread
Liberty Reserve operated as a criminal bank payment processor designed to help users conduct illegal transactions anonymously and launder the proceeds of their crimes. It emerged as one of the principal money transfer agents used by cyber criminals around the world to distribute, store, and launder illicit proceeds — Ahmed Yassine Abdelghani managed the daily operations of Liberty Reserve between approximately 2006 and 2009. He is charged with one count of conspiracy to commit money laundering,
Allan Esteban Hidalgo Jimenez aka Allan Garcia
May 28, 2013, the Southern District of New York unsealed charges against Liberty Reserve, a company that operated one of the world’s most widely used digital currency services, and seven of its principals and employees with money laundering and operating an unlicensed money transmitting business. Liberty Reserve is alleged to have had more than one million users worldwide, including more than 200,000 users in the United States, who conducted approximately 55 million transactions, virtually all of which were illegal, and laundered more than $6 billion in suspected proceeds of crimes. (See above Abdelghani for various Court documents) -Allan Esteban Hidalgo Jimenez managed the daily operations of Liberty Reserve starting in approximately 2010
May 2016 Liberty Reserve Founder Arthur Budovsky Sentenced In Manhattan Federal Court To 20 Years For Laundering Hundreds Of Millions Of Dollars Through His Global Digital Currency Business - DOJ-OPA
JUDGMENT In A Criminal Case (S1-13-Cr-368-04). Date of Imposition of Judgment: 5/6/2016. Defendant Arthur Budovsky (4) pleaded guilty to Count(s) 1s. Count(s) all counts in 13cr368 & S1 are dismissed on the motion of the United States. IMPRISONMENT: 240 months. SDNY-ECF
May 2018 ORDER (see SDNY-ECF) as to Arthur Budovsky. In a letter dated February 27, 2018, attorney Marshall Mintz, counsel for the defendant, requests..
Aug 22, 2019 - OPINION AND ORDER......Budovskys August 17, 2018 petition for a writ of habeas corpus is denied. Because Budovsky has not made a substantial showing of a denial of a constitutional right, a certificate of appealability will not issue. (SDNY-ECF or via my public drive)
Pavel Pavlovich Dubovoy aka Павло Павлович Дубовий
Also see Ieremenko and Radchenko as Dubovoy was part of the hacking group.
February 2010 and August 2015, Turchynov and Ieremenko, computer hackers based in Ukraine, gained unauthorized access into the computer networks of Marketwired L.P., PR Newswire Association LLC (PRN), and Business Wire. They used a series of sophisticated cyber attacks to gain access to the computer networks. The hackers moved through the computer networks and stole press releases about upcoming announcements by public companies concerning earnings, gross margins, revenues, and other confidential and material financial information.
In General I think a lot of Americans believe the US Secret Service just protects the President of the United States and Foreign dignitaries - that’s only a fraction of the USSS mission.
Secret Service agents, professionals, and specialists work in field offices around the world to fight the 21st century’s financial crimes, which are increasingly conducted through cyberspace. These investigations continue to address counterfeit, which still undermines confidence in the U.S. dollar, but it is credit card fraud, wire and bank fraud, computer network breaches, ransomware, and other cyber-enabled financial crimes, that have become the focus of much of the Secret Service investigative work.
OFFICE OF INVESTIGATIONS
I recommend you take a moment and review the USSS
The Office of Investigations operates as a global network of multi-functional teams, conducting high-impact criminal investigations that safeguard the integrity of financial and payment systems, while fully supporting all protective requirements.
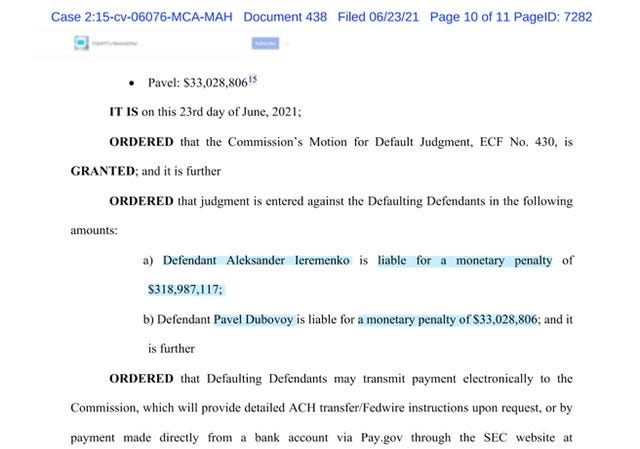
Aloha Default Judgement re Fugitives Ieremenko et al


see latest update in yesterday’s default judgement as to fugitives Aleksander Ieremenko and trader Pavel Dubovoy, who was fined $33 million,
Case 2:15-cv-06076-MCA-MAH via ECF link or via my public drive
And with that I think you have a sufficient amount of documents and facts as to the USSS “re-launch” of their 10 most wanted cyber -criminal fugitives.
-Filey