Apple v NSO Group aka Pegasus. Biden Admin adds additional entities to MEU list -Sanctions baby Sanctions-
11/24/21 -Commerce Dept quietly placed dozens Involved in the Support of PRC Military Quantum Computing Applications, Pakistani Nuclear & Missile Proliferation, & Russia’s Military on MEU list
…Fair warning this is an exhaustive and in-depth article…
The topics covered; deeper dive into NSO-QCyber-Pegasus, the former and current Administration’s actions, the ever complicated USA & China relationship, Sanctions MEU, Foreign Services Immunity Act, a quick nostalgic trip down Mike-QANON-Sedition Flynn memory lane, NSO’s FARA filings, recent 9th CCOAs ruling regarding Facebook/WhatsApp v NSO.
I attempted to connect as many dots as possible and I think my spelling errors might be uncharacteristically low <snort> in short I’m telling you there’s a whole lotta “facts” -but hey if you decide TL:DR ←that’s entirety your decision. Conversely if you take the time to read this article and the dozens upon dozens of original source documents —I am pretty sure that you’ll walk away with a far greater understanding of just how damaging the NSO-Q-Cyber-Pegasus’ tentacles really are…
The truncate background — you’ll need it because there’s a lot to unpack and it would be best to reread this previous article. I still remember being on the unrelenting end of the twitter-hate circa 2018 when I was like;
“…hmmm maybe we should actually talk about Pegasus…because it’s way worse…”
Pegasus wasn’t a “phantom” it was a highly calibrated weaponization of malware…
Or the fact that the Facebook/WhatsApp v NSO Group lawsuit unearthed a lot of facts. Or in January of 2020 I was like -whoa there - how on earth did MbS unload malware without Jeff Bezos opening an email or picture because at the time I was told that Pegasus wasn’t real and I was spreading disinformation. Weird how it turns out that if you read the UN HCR report(s) concerning Mr Bezos’ compromised mobile phone how the dots connected, back to KSA and had Twitter pitstop


By now the vast majority of my readers know that I read every page, every footnote and every Annex —that’s why shortly after the January 2020 UN HCR Report I was like always read the whole report . Did you really think that I was being facetious when I tweeted this “Putin to MbS” — I can assure you that I was being stone-cold serious. Rhetorical questions be damned. If I have/had enough of a factual basis (like literally Court filings) it becomes second nature to make an educated prediction. In my industry anticipating what the opposing party will do is a prerequisite and it shouldn’t be under estimated. No really if you lack the ability to properly forecast an action then you are doing your clients a major dissservice.
Additionally while the Facebook/WhatsApp v NSO Group litigation played out, like a train wreck telenovela on serious steroids headed to dysfunction junction aka the hot mess express. Ultimately things did not go well for the NSO Group. - Oh Hey remember that time when someone was like well B-I-N-G-O → Q-Technologies and then Flynn and then Wray and then Rosenstein.
In May of 2020 the aforementioned lawsuit hit a bit of a judicial speed-bump. And to date we, the general public still has zero idea what exactly the DOJ matter was/is underseal. Presumably that matter is still under seal.
As you’ll undoubtedly note, my 2020 assessment concerning Flynn and NSO/QTech wasn’t a far fetched conspiracy theory. I don’t make it a habit of blindly trusting conspiracy theories or individuals who are infamously known as conspiracy theories-crack-pots. And when possible I generally produce original documents. See Flynn’s Feb 2017 — OGE filings OSY Tech shareholder of Q Cyber Tech
Flynn signed his OGE Financial Disclosure on 2/11/17, a few days before he was fired.. Moreover it was curious that this late in the FB v NSO litigation NSO suddenly opened their kimono, thereby disclosing OSY Tech shareholder of Q Cyber Tech See Flynn’s OGE Filing
May 20, 2020 NSO Filing
Archived (and very long) Twitter Thread concerning the other litigation
“..around April 2019 and May 2019, Defendants used WhatsApp servers..to send their Spyware to approximately 1,400 mobile phones and devices belonging to attorneys, journalists, human rights activists, government officials, and others”
Its easy to say XYZ is “bad” absent any documentation. Irrespective of how many times a lie is told, in the end it’s still a lie.
October 8, 2021 - Six Devices of Palestinian Human Rights Defenders Hacked with NSO Group’s Pegasus Spyware -Front Line Defenders…
On November 8, 2021 Front Line Defenders (FLD) issued a Press Release -which includes a pretty detailed “after action” Report. In addition FLD also proffered a detailed timeline for the injection/infection of malware 1and thereafter a subsequent timeline/chain of events…
The following is relatively important: One of the six targeted individuals, is an American citizen. On October 16, 2021 Front Line Defenders received a call from by-Al Haq, a human rights organization—as noted by-Al-Haq voiced concern that one of their Jerusalem-based staff member and a possible infection with spyware.
Almost immediately FLF launched an investigation, specifically a technical investigation. An assumption can be made that during the course of FLD’s investigation Hacked-Phone(s) discovered an additional five phones which brings us to the number 6. FLD’s investigation uncovered some interesting facts.
For Example the following datapoints;
The primary device, which in question & purportedly had been infected in July 2020, with spyware sold by Israel-based NSO Group.
FLD’s investigating started with a phone call, below is an abbreviated timeline;
October 16, 2021 FLD receives a phone call -stating that a mobile phone might have been infected with malware.
FLD’s Digital Protection Coordinator (DPC), Mohammad Al-Maskati
starts his forensic investigation of the original device and then discovers indications of Pegasus spyware.
Also on October 16, 2021 - FLD then shares the data from logs and other key evidence was then provided to Citizen Lab. Which Citizen Lab latter confirm FLD’s initial findings.
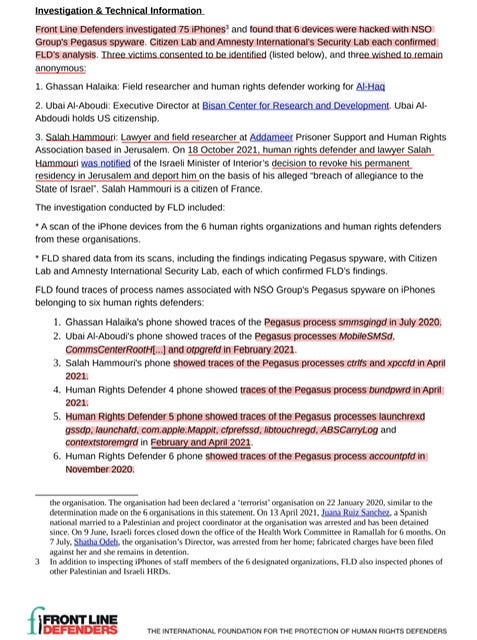
The six victims —FLD prefaced their recent report that they proactively sought out peer to peer reviews of their findings. Both Citizen Lab and Amnesty International and later affirmed FLD’s assessment. shared the data it gathered from the phones with Citizen Lab and Amnesty International’s Security Lab for independent peer review. Both organizations confirmed, with a degree of high confidence, that Front Line Defenders conclusion that the phones were hacked via Pegasus. Below is an itemized list of the six phones examined by FLD’s and peer reviewed by two separate entities. Also notice the “traces of the Pegasus process” and who ever Human Rights Defender #5 and #6 —cleverly #5 shows a secondary infection
Ghassan Halaika's phone showed traces of the Pegasus process smmsgingd in July 2020.
Ubai Al-Aboudi's phone showed traces of the Pegasus processes MobileSMSd, CommsCenterRootH[...] and otpgrefd in February 2021.
Salah Hammouri's phone showed traces of the Pegasus processes ctrlfs and xpccfd in April 2021.
Human Rights Defender 4 phone showed traces of the Pegasus process bundpwrd in April 2021.
Human Rights Defender 5 phone showed traces of the Pegasus processes launchrexd, gssdp, launchafd, com.apple.Mappit, cfprefssd, libtouchregd, ABSCarryLog and contextstoremgrd in February and April 2021.
Human Rights Defender 6 phone showed traces of the Pegasus process accountpfd in November 2020.
Biden Administration, NSO Group, Sanctions & China…USA’s relationship with China officially “it’s complicated” Status
I’d like to point out a few items that a lot of individuals appear to have (unintentionally) overlooked. And of course, your prerequisite grifter playbook. If your shtick can be boil down to the following narrative;
…Mob + Russia + Trump + more mob + Russian Oligarchs installed Trump + even more mob + Money Laundering + Drugs = Trump’s going down. Fun Fact: When an incoherent conspiracy theory can be boiled down to this kind of trite and bombastic prognostication —ultimately those trafficking in these theories rarely if ever proffering zero (or any) evidence to support the following. Again the following paragraph is hyperbole and it should not be taken as fact
…it is totally an Op, …[insert names] are being paid — obviously Trump used laundered money to help fund the illegal trafficking of hundreds of thousands of foster children. They used the same airline that Pompoe used during “Operation AirBridge” He and his co-conspirators used a private/chartered plane..snorted a lot of nose snow off numerous strippers bare-bottoms…
Again please note my extreme sarcasm. Obviously there’s nothing factual in the previous paragraph. All kidding aside that is the fantastical pitstop in conspiracy-landia. Which are consistently devoid of any facts to support said theory. Conversely the following facts surround NSO:
Pegasus was created and widely deployed during the Trump Administration
Pegasus was/is a cyber information weapon and KSA can’t claw it back because the toothpaste is out of the tube.
Deploying self/remote deployable malware and to use that information to essentially rendition vocal opponents of authoritarian regimes, is incompatible with any civilized society, much less a Democratic and/or Republic…
Under both the Trump and Biden Administration the following enforcement actions occurred. Under the Department of Commerce the Bureau of Industry and Security (BIS) -on April 28, 2020, the Department of Commerce’s BIS) published two (new) final rules. The BIS also proposed rule in the Federal Register amending the Export Administration Regulations (“EAR”) with the goal of tighten targeted restrictions on exports of technology to China, Russia, and Venezuela. With the intent to also protect America’s Intellectual Property - of which China has consistently engaged in Economic Espionage -China doesn’t create new technologies — for the most part they steal it costing Countries like America millions and possibly billions in Economic Loss by way of China’s prolific economic espionage 2
Federal Register/Vol. 85, No. 82/Tuesday, April 28, 2020/Rules and Regulations 23459 -amend the EAR to expand license requirements on exports, reexports, and transfers (in-country) of items intended for military end-use or military end-users in China, Russia, or Venezuela;
BIS also proposed modification to: License Exception Additional Permissive Reexports (“APR”) to remove provisions authorizing certain reexports of national security-controlled items; and
And lastly sought the removal License Exception Civil End Users (“C) for national security-controlled items on the Commerce Control List (“CCL”) to countries of national security concern.
FAQ re Department of Commerce -BIS Division: Expansion of Export, Reexport, and Transfer (in-Country) Controls for Military End Use or Military End Users in the People’s Republic of China, Russia, or Venezuela. Final Rule. (85 FR 23459) (April 28, 2020) —Updated January 19, 2021
Important Enforcement Action re NSO Group
On November 3, 2021 BIS issued a final rule which added twenty-seven foreign entities and individuals to the Entity List for engaging in activities that are ‘contrary to the national security or foreign policy interests of the United States” —The twenty-seven entities and individuals are located in the People’s Republic of China, Japan, Pakistan and Singapore. One entity based in Russia was added to the Military End-User (MEU) list.
On November 24, 2021 BIS issued a final rule which added twenty-seven foreign entities and individuals to the Entity List for engaging in activities that are contrary to the national security or foreign policy interests of the United States.
PRC Military Quantum Computing Applications, Pakistani Nuclear and Missile Proliferation, and Russia’s Military —
The twenty-seven entities and individuals are located in the People’s Republic of China (PRC), Japan, Pakistan and Singapore. One entity based in Russia was added to the Military End-User (MEU) list. In addition the BIS noted that this enforcement effort is
…aimed at improving citizens’ digital security, combatting cyber threats, and mitigating unlawful surveillance and follows a recent interim final rule released by the Commerce Department establishing controls on the export, reexport, or in-country transfer of certain items that can be used for malicious cyber activities.
…Such practices threaten the rules-based international order….
NSO Group and Candiru (Israel) were added to the Entity List based on evidence that these entities developed and supplied spyware to foreign governments that used these tools to maliciously target government officials, journalists, businesspeople, activists, academics, and embassy workers. These tools have also enabled foreign governments to conduct transnational repression, which is the practice of authoritarian governments targeting dissidents, journalists and activists outside of their sovereign borders to silence dissent. Such practices threaten the rules-based international order.
More broadly the BIS Final Rule -which is scheduled to be published in the November 26, 2021 Federal Register - Addition of Entities and Revision of Entries on the Entity List; and Addition of Entity to the Military End-User List… if you understand the purpose of the Federal Register then you’d know once it’s published then it becomes “gospel”…
An unpublished Rule by the Industry and Security Bureau on 11/26/2021 -also see Official Federal Register Publication of BIS’s Final Rule 3 which effectuates said additions to the MEU list to November 26, 2021 -also did you wonder why the recent war of words between President Biden and President Xi Jinping especially related to Taiwan? Well part of that answer can be found in the additional Chinese Entities/Individuals added to the MEU..
…This rule also revises one existing entry on the Entity List under the destination of China, adds addresses under the destination of Taiwan for a listed entity, and corrects an entry under the destination of China..
And sure while some might espouse the rhetoric that President Biden is weak on China - perhaps those individuals are not fully aware about the wide scope of actions taken by the current Administration has taken as it relates to China.
For Example:
These three affiliates of Corad Technology Limited have been involved in sales of technology from the United States and other Western nations to Iran’s military and space programs, Democratic People’s Republic of Korea (North Korea) front companies, and Chinese government and defense industry subordinate entities. BIS is also adding a reference under Taiwan to one of Corad Technology Limited’s offices, the Corad Taiwan Representative Office, which has also been involved in such technology sale…
Shaanxi Zhi En Electromechanical Technology Co., Ltd. located in China; and Q&N Traders, U.H.L. Company, Jiuding Refrigeration & Air-conditioning Equipment Co (Pvt) Ltd, K-SOFT Enterprises, Seljuk Traders (SMC-Private) Limited, Global Tech Engineers, Asay Trade & Supplies, and Jade Machinery Pvt. Ltd., all located in Pakistan, to the Entity List based on their contributions to Pakistan’s unsafeguarded nuclear activities…
…ERC also decided to add Al-Qertas, located in Pakistan, to the Entity List based on their contributions to Pakistan’s unsafeguarded nuclear activities.
The point is Joe Biden was a duly elected President of the United States, he brings decades of Senate and Diplomatic Experience with him. President Biden has surrounded himself with extraordinarily smart individuals who offer him sage counsel. But provided you know where and what to look for you too can see the Biden Administration isn’t going soft on China. Maybe that narrative should be closely scrutinized. Because the facts -like the facts in the public record (Federal Register) tend to annihilate that “specious narrative” that Biden is soft on China. And lastly before we dive into the recent Apple v NSO Lawsuit —I wanted to give my readers a sufficient predicate to understand what actions our Administration has taken to essentially make NSO Group-Pegasus-Phantom the pariah that it is…
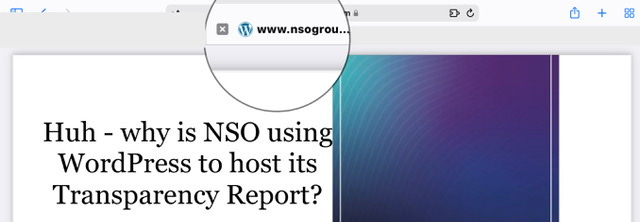
Also see NSO’s June 2021 Transparency Report
As you’ll note on page 2 of the cover letter I noticed something that is oddly pretty important
..to save lives through the prevention of serious crime and acts of terror, as well as through search-and-rescue, data analytics, and other related missions and applications.…
…This is also a great opportunity to thank our investors from Novalpina Capital…
Because less than 30 days after the June 30, 2021 NSO NSO Group Transparency and Responsibility Report —also not that this actually matters but I do think it’s rather odd that NSO is using a WordPress link to publish their report. Because the list of questions I have has actually increased given Word Press’ various vulnerabilities —see the tiny W logo? Yes that’s Word Press and it just strikes me as odd but then again I’m a fan on tiny details.
On July 27, 2021 SkyNews was first to report, that not all was well in Novalpina Capital. Which resulted in the board voting;
Private equity owner of spyware group NSO stripped of control of €1bn fund
….Novalpina Capital investors’ vote follows months of turmoil amid disagreements between co-founders which was a private equity owner of spyware group NSO stripped of control of €1bn fund
9th Circuit Court of Appeals Nov 8th Ruling -bad news for NSO-QCyber-Pegasus
Previously discussed the Facebook/WhatsApp v NSO & Q Cyber Tech lawsuit. From the start some of us, at least those of us who actually understand FSIA, the law NSO claimed offered them immunity - well on November 8, 2021 the 9th Circuit Court of Appeals held:
…the Foreign Sovereign Immunity Act occupies the field of foreign sovereign immunity and categorically forecloses extending immunity to any entity that falls outside the Act’s broad definition of “foreign state.” The panel rejected defendant’s argument that it could claim foreign sovereign immunity under common-law immunity doctrines that apply to foreign officials.
The panel stated that there was no indication that the Supreme Court in Samantar v. Yousuf, 560 U.S. 305 (2010), intended to extend foreign official immunity to entities. Moreover, the FSIA’s text, purpose, and history demonstrate that Congress displaced common-law sovereign immunity as it relates to entities.
The panel therefore affirmed the district court’s order.
Apple to NSO Group et al -see you in Court-
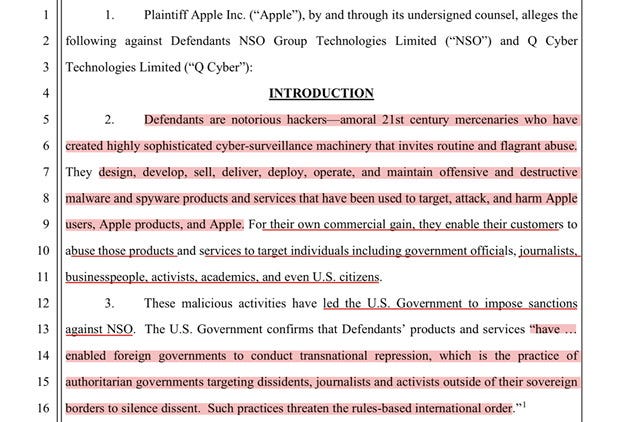
Let’s just go ahead and dive head deep into the newly filed lawsuit 4 - because the opening paragraph is a thing of extraordinary savagery…
…Defendants are notorious hackers—amoral 21st century mercenaries who have created highly sophisticated cyber-surveillance machinery that invites routine and flagrant abuse. They design, develop, sell, deliver, deploy, operate, and maintain offensive and destructive malware and spyware products and services that have been used to target, attack, and harm Apple-users, Apple products, and Apple…
…enable their customers to abuse those products and services to target individuals including government officials, journalists, businesspeople, activists, academics, and even U.S. citizens.
Apple provides new details on NSO Group’s FORCEDENTRY Exploit..
For what it’s worth -I would highly recommend that you read this Washington Post, July 18, 2021 in-depth investigative report: Response from NSO Group to the Pegasus Project.. to be clear Apple has spent innumerable hours and funds in research and development.
On a whole Apple products are some of the most secure —especially when you compare to Android products. At the same time Apple might (operative word) been slow addressing various security risks aka exploits, but in the end Apple takes the privacy of their users and data generated rather seriously. Whereas NSO Group-Q Cyber Tech are the exact opposite of Apple. I would highly recommend you read the September 2021 Citzen Lab Report on;
FORCEDENTRY and CASCADEFAIL NSO Group iMessage Zero-Click Exploit captured in the Wild
Because Citizen Lab Report did an exemplary job reporting the facts, exploits, Apple’s various security patches and the soup & nuts of how Pegasus was unleashed. Having the basis of fact will help you to fully understand Apple’s recently filed federal lawsuit against NSO-Pegasus.
As you’ll note in paragraphs 7 thru 9 -Here Apple is establishing a fact based predicate that Apple = Security —with over one Billion IPhones in use that makes up the lion’s share of the estimated 1.65 Billion “active Apple Devices- worldwide”
And to be clear I’m a sucker for low key jurisprudence shade and by shade I mean the utterly casual yet overt inference made:
…Ninth Circuit recently held, NSO and Q Cyber are not sovereigns and are not entitled to sovereign immunity…
Defendants seek to operate with impunity by hiding behind their unnamed customers. Indeed, in response to another lawsuit brought against NSO and Q Cyber by other victims of their attacks, NSO and Q Cyber argued that they should enjoy some form of “sovereign immunity” based on the status of the governments to whom they claim they sell their products and services….the Ninth Circuit recently held, NSO and Q Cyber are not sovereigns and are not entitled to sovereign immunity.
…Defendants’ malicious and harmful activities have brought them well within the long arm of the law and the jurisdiction of this Court, which has the authority to hold them to account for their violations of U.S. federal and state laws and for the damage they have inflicted on Apple and its users.
For the record this is really important because until this Court filing there was “talk” and spirited speculation that NSO had created numerous iCloud Accounts. And clearly Apple’s lawsuit notes that NSO did not hack any of its servers but importantly though Apple asserts that numerous Apple Users Data was unlawfully exfiltrated by NSO’s Pegasus. I now refer you to paragraphs 22, thru 28 but in-particular paragraph 25
To deliver FORCEDENTRY to Apple devices, attackers created Apple IDs to send malicious data to a victim’s device — allowing NSO Group or its clients to deliver and install Pegasus spyware without a victim’s knowledge. Though misused to deliver FORCEDENTRY, Apple servers were not hacked or compromised in the attacks.
NSO deploys its malware and spyware primarily through servers hosted at data centerslocated in the United States and Europe. NSO has hired and consulted with various U.S.-based firms to help market its products and services, expand its business, and improve its public relations in the United States.Q Cyber has also hired a U.S.-based public relations firm to provide strategic and regulatory counsel
What’s really interesting about Apple’s newly filed federal complaint is Apple argues that NSO-Q Cyber-Pegasus created hundreds of iCloud accounts, which were later used, albeit covertly & surreptitiously exfiltrated incredibly personal data of the “targets” NSO customers identified but most importantly Apple argues that NSO et al violated the standard terms of service for iCloud accounts and services. Apple also argues that it sustained injuries mainly to the “Apple Brand” and ongoing security issues. These are not phantom (apologies for the pun) injuries, these are clear and concrete and particularized injuries of fact.
Defendants force Apple to engage in a continual arms race: Even as Apple develops solutions and enhances the security of its devices, Defendants are constantly updating their malware and exploits to overcome Apple’s own security upgrades.
Apple Support’s November 25, 2021 Announcement
In addition to the federal lawsuit, Apple also announced a $10 million contribution to support cybersurveillance researchers and advocates. To me that’s money well spent and I hope this leads to a better private/public partnership.
And lastly on November 25, 2021 Apple 5made the following (and rather low key) announcement -and this is also important because this ups the ante and it puts rogue organizations like NSO on full notice. But it also solidifies Apple’s commitment to its customers, by proactively notifying Apple Customers:
…Apple threat notifications and protecting against state-sponsored attacks -will proactively notify users…
Apple threat notifications are designed to inform and assist users who may have been targeted by state-sponsored attackers.
If Apple discovers activity consistent with a state-sponsored attack, we will notify the targeted users in two ways:
A Threat Notification will be displayed at the top of the page after the user signs in to appleid.apple.com.
Apple will send an email and iMessage notification to the email addresses and phone numbers associated with the user’s Apple ID.
So for now we wait and see how NSO responds —especially in light of the recent 9thCCOAs ruling which affirmed the District Court’s Ruling that NSO has zero immunity protections under the FOREIGN SOVEREIGN IMMUNITIES ACT it is very unlikely they’d regurgitate their proven flawed argument. But then again it’s just best to wait and read NSO’s response. From a Public Relations standpoint there’s zero amount of “transparency reports” that could ever absolve NSO and their unnamed clients from the flagrant abuse of International Law, Domestic Law and once public trust is gone — it is almost impossible to ever regain that trust. Irrespective of how many lobbying firms or law firms NSO retains the damage of Pegasus will be NSO’s everlasting legacy.
I hope this article helped you see the broader picture and provided you with an more in-depth conversation with the prerequisite original documents.
Extra deep dive into DOJ and China
As recently noted by the Department of Justice (last updated on November 19, 2021) nearly 80% of all economic espionage prosecutions brought by the U.S. Department of Justice (DOJ) allege conduct that would benefit the Chinese state. The DOJ’s official position is there are least some nexus to China in around 60% of all trade secret theft cases.
Since President Biden has been in office the DOJ has prosecuted more than thirteen cases. Unless otherwise specified -the embedded links are exclusively DOJ-OPA Press Announcements.
From Jan 2021 to Present -thirteen criminal prosecutions
From January 2020 to Jan 20, 2021 -the DOJ Prosecuted 24 unique cases
From December 2019 thru January 2020 -the DOJ has prosecuted some 15 unique criminal cases
From January 2018 to December 2018 -the DOJ only prosecuted one, yes ONE case December 20, 2018 Two Chinese Hackers Associated with the Ministry of State Security Charged with Global Computer Intrusion Campaigns Targeting Intellectual Property and Confidential Business Information
The Southern District of New York unsealed an indictment charging Chinese nationals Zhu Hua and Zhang Shilong with conspiracy to commit computer intrusions, conspiracy to commit wire fraud, and aggravated identity theft. As alleged, the defendants, through their involvement in a hacking group associated with the Chinese Ministry of State Security, from 2006 to in or about 2018, conducted global campaigns of computer intrusions targeting, among other data, intellectual property and confidential business and technological information at managed service providers, which are companies that remotely manage the information technology infrastructure of businesses and governments around the world, including in the United States
List of China related criminal cases under the Biden Administration:
Look like it or not there are a lot of influential individuals who continue to propagate a false narrative that somehow President Biden is weak on China. When you tune out the white noise aka screaming goats and you focus on the actual facts in the public record —one could make a decent argument that Biden isn’t weak on China. Insofar as to initially relying on Diplomacy and a “soft approach” to tell China to stop stealing our Country’s (and our Allies) intellectual property —the facts actually demonstrate that Biden is on par if not more aggressive than the previous administration. Moreover if you know about the DOJ’s China Initiative then you’d know that the DOJ China Initiative was established in 2018. Yes that’s one decent public policy initiative made by the former Administration that I actually agree with.
November 5, 2021
Jury Convicts Chinese Intelligence Officer of Espionage Crimes, Attempting to Steal Trade Secrets
A federal jury today convicted Yanjun Xu, a Chinese national and Deputy Division Director of the Sixth Bureau of the Jiangsu Province Ministry of State Security, of conspiring to and attempting to commit economic espionage and theft of trade secrets. The defendant is the first Chinese intelligence officer to be extradited to the United States to stand trial.
September 24, 2021
Huawei CFO Wanzhou Meng Admits to Misleading Global Financial Institution
The Chief Financial Officer of Huawei Technologies Co. Ltd., Wanzhou Meng, 49, of the People’s Republic of China (PRC), appeared in federal district court in Brooklyn, to enter into a deferred prosecution agreement (DPA) and was arraigned on charges of conspiracy to commit bank fraud and conspiracy to commit wire fraud, bank fraud and wire fraud.
Should you be inclined in September 2021 I published this follow up article about Meng —at the time of the original indictment I have a friend who works for an upper echelon law firm in Toronto —they pointed me to the indictment -at the time it was still under seal in PACER but my friend pointed me to an open source Canadian Judicial database that had the Indictment as part of the extradition process.
July 19, 2021
The Department unsealed an indictment which charged four PRC nationals, three of whom were officers in the PRC’s Ministry of State Security (MSS), with participating in a wide-ranging global computer intrusion campaign targeting infectious disease research, among other things. The unsealing was followed by a global condemnation of malicious PRC cyber activities by the European Union and other countries.
May 14, 2021
Following his November 2020 guilty plea, an Ohio man and rheumatology professor and researcher with strong ties to China was sentenced to 37 months in prison for making false statements to federal authorities as part of an immunology research fraud scheme. As part of his sentence, Zheng was also ordered to pay more than $3.4 million in restitution to the National Institute of Health (NIH) and approximately $413,000 to The Ohio State University.
April 28, 2021
Chinese National Pleads Guilty to Illegal Exports to Northwestern Polytechnical University
A Chinese national pleaded guilty to charges in connection with causing the illegal export of $100,000 worth of U.S. origin goods to Northwestern Polytechnical University (NWPU), a Chinese military university that is heavily involved in military research. He was sentenced on Sept. 9 to two years in prison.
April 22, 2021
Following her February 2019 indictment and a twelve-day trial, Dr. Xiaorong You, aka Shannon You, 59, of Lansing, Michigan, was convicted of conspiracy to commit trade secret theft, conspiracy to commit economic espionage, possession of stolen trade secrets, economic espionage, and wire fraud. She is scheduled to be sentenced in April 2022.
April 21, 2021
Mathematics Professor and University Researcher Indicted for Grant Fraud
A federal grand jury in Carbondale, Ill. returned an indictment charging a mathematics professor and researcher at Southern Illinois University – Carbondale (SIUC) with two counts of wire fraud and one count of making a false statement. A status report is due to the court by March 29, 2022.
April 20, 2021
Hospital Researcher Sentenced to Prison for Conspiring to Steal Trade Secrets and Sell to China
Following his December 2020 guilty plea, an Ohio man was sentenced to 33 months in prison for conspiring to steal exosome-related trade secrets concerning the research, identification and treatment of a range of pediatric medical conditions.
April 13, 2021
The Department announced it had conducted a court-authorized operation to remove malicious web shells from hundreds of vulnerable computers in the United States running on-premises versions of MS Exchange software. These web shells had been placed on victim servers by cyber actors employed by or associated with the PRC government, which could have used the web shells to maintain and escalate persistent, unauthorized access to U.S. networks.
March 5, 2021
California Man Sentenced for Illegally Exporting Cesium Atomic Clocks to Hong Kong
A California man was sentenced in federal court for illegally exporting cesium atomic clocks to Hong Kong. A U.S. District Court Judge sentenced the individual to time served and three years of supervised release.
February 26, 2021
Chinese Businessman Charged With Conspiring To Steal Trade Secrets
A Chinese businessman was indicted for conspiring to steal General Electric’s (GE) trade secrets involving the company’s silicon carbide MOSFET technology worth millions of dollars.
February 3, 2021
A former University of Florida (UF) professor, researcher and resident of China has been indicted for fraudulently obtaining $1.75 million in federal grant money from the National Institutes of Health (NIH). The former UF professor is accused of concealing support he received from the Chinese government and a company that he founded in China to profit from that research. Yang traveled to China in August of 2019 and has yet to return to the United States.
February 1, 2021
Hospital Researcher Sentenced to Prison for Conspiring to Steal Trade Secrets, Sell Them in China
A former hospital researcher, Li Chen, was sentenced to 30 months in prison following her July 2020 guilty plea, for conspiring to steal American research concerning the identification and treatment of a range of pediatric medical conditions. The convicted received benefits from the Chinese government in exchange for trade secrets, and will forfeit approximately $1.25 million in punitive fees, 500,000 shares of stock, and $2.6 million in restitution as part of her sentence.
Co-defendant and husband Yu Zhou pleaded guilty in December 2020 and was sentenced in April 2021 to 33 months' imprisonment, $10,000 fine, and restitution in the amount of $2,616,087.00 to be paid jointly with co-defendant, Li Chen.
January 29, 2021
Chinese National Charged with Criminal Conspiracy to Export U.S. Power Amplifiers to China
An indictment was unsealed against a 45-year-old national of the People’s Republic of China, charging the man with participating in a criminal conspiracy to violate U.S. export laws by shipping U.S. power amplifiers to China.
Bottom Line regarding China & our National Security
Which is an incredibly complicated and nuanced subject matter. To make a very long & complicated story short, one of the best resources who has been incredibly generous with his time and answering a multitude of multipart questions from Moi has been @burgessct —when I was on Twitter Chris became my go to resource and he always made time for my incessant questions. Chris Burgess writes for Clearance Jobs and I definitely enjoyed collaborating with him on the various DOJ v China criminal cases. One thing I truly enjoy about my education from Chris is he isn’t afraid to say “kid you are flat out wrong and here’s why” -I personally value constructive criticism and his patience gave me a master class in fully understand the totality of Economic Espionage.
I tend to view criminal cases in the context of the various statutes and I didn’t look at the whole picture. Nor did I fully understand the (actual) Intelligence Community’s various “missions” and how China’s Thousand Talents will go down in history as the most damaging espionage campaign. And unfortunately Universities and Colleges either chose not to do their due diligence or they were in autopilot mode and thus didn’t vet the various Chinese Academics. For example here’s an instance where collaborative reporting worked:


Apologies for the divergence of NSO to the Biden Administration’s enforcement actions against China and Russia and Venezuela. While not wholly interconnected, one could infer that there is definitely some connective tissue of NSO-Pegasus, China and Russia because there actually is, once you read the facts in various original sourced documents. At any rate I hope you had a wonderful holiday with Friends and Family. The 2021 Thanksgiving was so much better than 2020 -because I was finally able to see my niece who’s now over a year old. FaceTime wasn’t cutting it anymore and I’m kind of a sucker for babies. Lastly should you have any questions please feel free to leave a comment and I’ll do my best to respond in a timely and factual manner. But I feel comfortable in saying that my readers now have an (albeit wordy) explanation to the recent events concerning NSO. Thoughts & Prayers NSO -thoughts and prayers. Eventually justice will come for you…
How does one lose a replacement car?
On a personal note -how does one actually lose a 2022 Hybrid? My replacement car was originally scheduled to be delivered to my home about 10 days ago. The last notification I received was my car was picked up at a Walnut Grove, CA Dealership and was on the way to Texas. My sales rep sent me pictures of the replacement car & the transit itinerary. Two days later I got an update that my replacement car was in Waco Texas and was being taken off the transport trailer. My sales rep said “hey don’t be mad but I think they lost your car” —I saw her text message and I literally laughed out loud during a meeting. During this time of year my work days start before 5AM and it’s my known busy season -hence I’m on I95 North/South a lot. So after my 16+ hour work day I called my sales rep back.
At some point between Waco & Dallas Fort Worth my car got lost. Or more precisely it appears that someone accidentally loaded my car on to the incorrect trailer. That trailer was headed to dealership in Cleveland OH. By the time the issue was discovered my car was just hours away from being delivered to the local Dealer, in freaking Cleveland OH.
On the flip side the unexpected delay gave me a few extra days I needed to work with the DMV. My State’s (newly amended) Window Tint & Reflection Law -required that I prove the tinting was factory installed. The newly amended & codified Visible Light Transmission; allows tinting up to 50% for driver’s window and 35% for the rear windows. The Factory installed window tint sits at 45% and 30% respectively. I just needed to provide the DMV with the factory specifications so they can send me a certified letter should I ever be pulled over and/or ticketed for “impermissible dark window tinting” applicable to both primary and secondary traffic offenses.
I told my sales rep, that driving to Cleveland really isn’t an option. Since USAA worked on my behalf to have AllState extended my rental car to mid December 2021. Once my replacement car is headed to the DC area I’ll avail myself or if I’m busy with work, I will have my husband take delivery. The revised ETA is now December 6 at 3PM at my home versus the dealership. The transaction of buying a replacement car virtually was oddly sans incident —minus the shipping snafu.
All said and done, it’s not that bad. Meaning my 2019 car was replaced by a 2022 model and fully paid for. So there’s an upside to the October accident, silver linings, right? However the dental reconstruction to fix the damage caused by the accident has been the most unenjoyable experience, thus far in my short life. Mainly because my jaw still aches from drilling in 4 metal post but my Dentist thinks by the New Year I’ll have a decent smile -thank goodness for facial masks <snort>
And your reward for slogging through this incredibly long and complex article - nearly two minutes of Sunset on the Point with a lot of Dolphins
Be Well. Be Happy and Be informed -Filey
See Front Line Defenders November 8, 2021 Press Release -last accessed on November 26, 2021: https://www.frontlinedefenders.org/press-release-front-line-defenders-investigation-finds-pegasus-spyware-6-palestinian-hrd-phones and the Front Line Defenders supplemental Timeline contains a plethora of fact nuggets https://www.frontlinedefenders.org/sites/default/files/fld_pal_statement_-_final_-_5_nov_2021.pdf
In 2014 under Attorney General Holder the Department of Justice -for the first time ever brought charges against five prolific hackers and charged each with “Economic Espionage” - Monday, May 19, 2014 the DOP-OPA Press Release announced that the U.S. Charges Five Chinese Military Hackers For Cyber Espionage Against U.S. Corporations And A Labor Organization For Commercial Advantage -“indicted five Chinese military hackers for computer hacking, economic espionage and other offenses directed at six American victims in the U.S. nuclear power, metals and solar products industries” at the time Westinghouse had inked a lucrative contract with Ukraine —Defendants; Wang Dong, Sun Kailiang, Wen Xinyu, Huang Zhenyu, and Gu Chunhui, who were officers in Unit 61398 of the Third Department of the Chinese People’s Liberation Army. For the record Chopstick was the precursor to X-Agent & X-Tunnel which was later used by Russia in the 2016 General Election.
“First Time Criminal Charges are Filed Against Known State Actors for Hacking”
added entities/individuals to MUE list -FR Doc. 2021-25808 Filed 11-24-21; 8:45 am -yes because that’s how “new” this news is and it should be more widely reported because it’s important - https://www.federalregister.gov/documents/2021/11/26/2021-25808/addition-of-entities-and-revision-of-entries-on-the-entity-list-and-addition-of-entity-to-the -last accessed November 24, 2021
See November 23, 2021 Apple News Release which explains their lawsuit -to ease any concern about the provenance of the lawsuit -I took the liberty of finding you an Opem Source Link https://www.apple.com/newsroom/pdfs/Apple_v_NSO_Complaint_112321.pdf
See Apple Support November 25, 2021 Press Release - last visited November 25, 2021 https://support.apple.com/en-gb/HT212960



















I am glad you had a happy Thanksgiving with your baby niece and that your replacement car is on its way, still and despite a detour.
This report is mind blowing. How so many academics were not vetted properly is pretty scary. At least a bunch have been caught.
Thank you. Car looks like it’ll be a fine ride.