BitCoinFog analysis of 10 years of transactions $335,809,383 Bitcoin tumbling
We need to talk about this because it’s kind of a big deal - Roman Sterlingov ran BitCoinFog - investigators noted >1.2M transactions dating back to 2011
…per the April 28, 2021 DOJ-OPA Press Release, which reads in part:
operated Bitcoin Fog since 2011. Bitcoin Fog was the longest-running cryptocurrency “mixer,” gaining notoriety as a go-to money laundering service for criminals seeking to hide their illicit proceeds from law enforcement.
Over the course of its decade-long operation, Bitcoin Fog moved over 1.2 million bitcoin – valued at approximately $335 million at the time of the transactions. The bulk of this cryptocurrency came from darknet marketplaces and was tied to illegal narcotics, computer fraud and abuse activities, and identity theft.
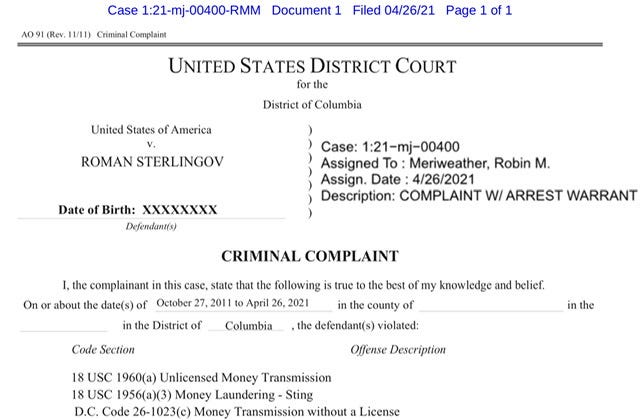
Prosecutors unsealed the Complaint1 and Affidavit2 as to Defendant Sterlingov. Who is charged with money laundering, operating an unlicensed money transmitting business, and money transmission without a license in the District of Columbia.
…support a finding of probable cause that ROMAN STERLINGOV, a citizen of Russia and Sweden, committed the following offenses:
18 U.S.C. § 1956(a)(3)(B) - Laundering of Monetary Instruments
18 U.S.C. § 1960(a) Operating an Unlicensed Money Transmitting Business, in
D.C. Code § 26-1023(c) - Money Transmission Without a License
Filey - research -archive-sidebar
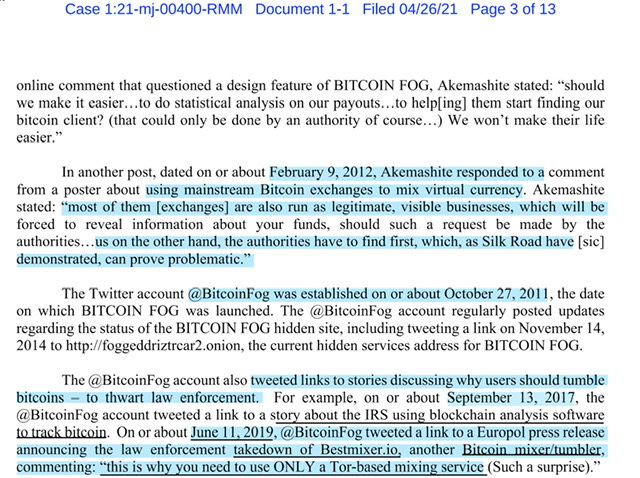
The Twitter account, which is repeatedly referenced in the Affidavit @BitCoinFog
There’s also this Twitter account @BitCoinFogg aka BitCoin Fog Support, which ironically is not mentioned in the Affidavit but based on information and belief I think it’s important. Again no one appears to have archived this Twitter account, so I did, archive found here
After a third data sweep - I was able to identify yet another Twitter account associated with BitCoin Fog (Twitter has a weird algorithm that users can create case sensitive accounts and it’s difficult to decisively conclude if they are linked) to explain how I was able to conclusively confirm @BltcoinFog (archived) is in fact linked:
Step 1 https://bitcoinfog.site
Step 2 clicked on the link in the red box
and like magic what’s interesting is that Twitter account was created in 2017, whereas the Support Account was ostensibly created in March of 2010 (approximately 14+ months before BitCoin Fog went live)
Keep this in mind when you read the Affidavit- specifically pages 9 et seq where the disclosure of “beta testing” is enumerated because I think that matters, a lot.
Based on preliminary research it appears no one had archived the aforementioned Twitter account. Therefore I took the liberty of archiving the account found here and here. Incidentally when researching I stumbled upon this Twitter account that appears to have a lot of direct knowledge of how BitCoinFog worked - also archived. I found their 2019 tweets rather interesting.
For example;


This 2019 thread also worth reading because the replies are intriguing, at least for me but then again I tend to get caught in the weeds

Affidavit - Defendant ROMAN STERLINGOV
been investigating an illicit
Bitcoin money transmitting and money laundering service called BITCOIN FOG. BITCOIN FOG is an Internet-based service accessible from the District of Columbia and U.S. states. It can be accessed through the Tor hidden website located at http://foggeddriztrcar2(.)onion
Dirty BitCoin you say?
To help you understand the totality of this DOJ takedown- Sterlingov started BitcoinFog on October 27, 2011 - and his service(s) remained operational until April 26, 2021, thusly over 1.2 unique Bitcoin transactions with an estimated worth of $335,809,383.00
On page 2 of the affidavit- I’d like to draw your attention to the previously mentioned Twitter Account - specifically the October 27, 2011 Tweet (also archived)
Additionally the Affidavit disclosed, Roman Sterlingov used a pseudonym Akemashite Omedetou3 (which is Japanese for “Happy New Year”)
Specifically I believe this is the BitCoinTalk.org Announcement that is referenced in the Affidavit https://bitcointalk.org/index.php?topic=50037.0 - also archived
When a new BitCoinFog customer created an account they used Tor via an onion address. Users required mandatory registration, and a minimum deposit of 0.01 BTC to open an account and to BitCoinFog’s platform. Interestingly thought the new user/customer registration was not tied to an email, rather it simply required a unique username and password.
Trust me - stay with me it’s about to get good
The notion that Bitcoin or other cryptocurrencies are completely anonymous is a misnomer. For better or worse because of this fallacy cyber criminals use cryptocurrency like you and I drink water. In short it’s not at all anonymous, perhaps one could argue that initially it was anonymous but cyber evolution (specifically software) can in fact track the in/out of cryptocurrency transactions.
“Analysis of bitcoin transactions, financial records, Internet service provider records, e-mail records, and additional investigative information, identifies Roman Sterlingov as the principal operator of Bitcoin Fog,”
IRS-CI cyber analysts reviewed all inputs and outputs from BITCOIN FOG to identify bitcoins sent directly to BITCOIN FOG from known darknet markets and bitcoins sent from BITCOIN FOG to known darknet markets.
IRS-CI’s analysis determined BITCOIN FOG received approximately 486,861.69 BTC (approximately $54,897,316.44 at the time of the transactions) directly from darknet markets.
BITCOIN FOG sent approximately 164,931.13 BTC (approximately $23,690,956.28 at the time of the transactions) directly to darknet markets.
BITCOIN FOG sent or received more than $78 million in transactions involving known darknet markets, counting only direct transactions.
Undercover Transactions on BITCOIN FOG
In September of 2019 an Internal Revenue Service -Criminal Investigation Special Agent (IRS-CI-SA), who was working in an “undercover capacity” created a BitcoinFog account using the registration page. Once the account was successfully created the IRS-CI-SA deposited the prerequisite (and nominal) amount. They were able to observe the following:
Through blockchain analysis, investigators traced bitcoin from the BITCOIN FOG deposit address to known BITCOIN FOG Bitcoin clusters identified through blockchain analysis. IRS-CI investigators also traced bitcoin sent to the UC Receiving Wallet and confirmed that the bitcoin was sourced from BITCOIN FOG clusters.
Investigators were unable to directly trace any direct link between the “UC Sending Wallet” and the “UC Receiving Wallet,” confirming that BITCOIN FOG successfully tumbled the transaction by breaking the link in the blockchain between the source and ultimate destination of the funds.
Look some will (speciously) argue that BitCoinFog’s Administrator never acknowledged the email from the undercover IRS-CI-SA. Which is not exactly a compelling argument because the “lack of email response” is actually superseded by BitCoinFog’s action. Meaning the action taken point to “acknowledgment”
There was no response to the above message posted by the SA on or about November 19, 2019. The SA then directed BITCOIN FOG to send 0.01146764 BTC from the undercover account on BITCOIN FOG to an IRS-CI controlled undercover wallet. BITCOIN FOG did so.
Well HELLO Liberty Reserve
This is just good old fashion solid law enforcement work. Investigators blended; Analysis of bitcoin transactions, financial records, Internet service provider records, e-mail records and additional investigative information, identifies ROMAN STERLINGOV as the principal operator of BITCOIN FOG.
But in the end it came down to “Akemashite Omedotou” and the Shormint@hotmail.com that linked Defendant Sterlingov. Tilts head towards the sky and laughs and laughs and snort laughs
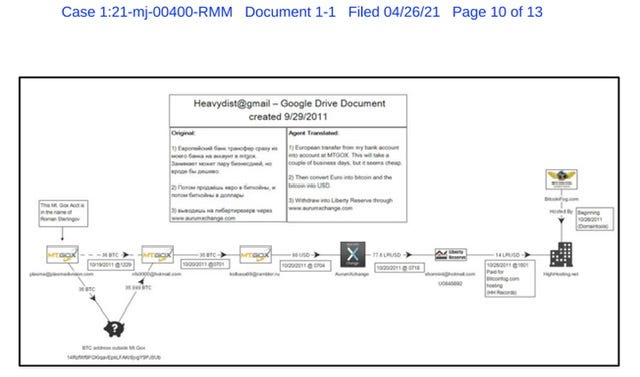
Layers upon layers upon - let’s play hide the cryptocurrency sausage. Note the linear flow of the flow chart. Defendant Sterligov —>Mt Gox —>Hotmail—> Mt Gox 2—> rambler.ru —> Mt Gox 3—>AurumXchange —>Liberty Reserve which was used to pay for hosting services
Oh but it gets more comical. Investigators were able to trace both Roman Sterlingov’s three Liberty Reserve accounts to his email back to his Mt Gox Account # 1, which used his “true name” and to tied it to his telephone number which he used his home address in Sweden.
But the Google Drive and documents (largely in Russian) also appears to be instrumental in investigators unmasking Sterlingov. That Google drive contained notes of the various steps Sterlingov took to mask his identity
Sloppy AF OpSec is what helped investigators to make numerous ties back to Roman Sterlingov -
-Filey
ECF - newly unsealed Criminal Complaint -last visited April 28, 2021 https://ecf.dcd.uscourts.gov/doc1/04518479164
ECF - newly unsealed Affidavit/Statement of Facts - last visited April 28, 2021 https://ecf.dcd.uscourts.gov/doc1/04518479165 or via my public drive
Akemashite Omedetou bitcointalk.org - user info -last visited April 29, 2021 - https://bitcointalk.org/index.php?action=profile;u=44692 also archived