Colonial Pipeline entering day 7 of the sophisticated cyber attack - restart in progress - updated 5/13/2021
Biden White House signs an Executive Order - Improving the Nation’s Cybersecurity
May 13, 2021 4:40PM update
Media Statement Update: Colonial Pipeline System Disruption
System Restart and Operational Update #2
Update: Thursday, May 13, 4:40 p.m.
“Colonial Pipeline has continued to make substantial progress in safely restarting our pipeline system….” Link to map, found here
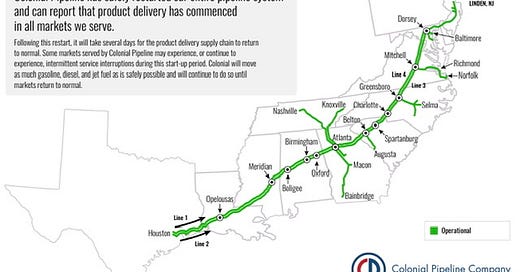
Colonial Pipeline has safely restarted our entire pipeline system and can report that product delivery has commenced in all markets we serve.
Following this restart, it will take several days for the product delivery supply chain to return to normal. Some markets served by Colonial Pipeline may experience, or continue to experience, intermittent service interruptions during this start-up period. Colonial will move as much gasoline, diesel, and jet fuel as is safely possible and will continue to do so until markets return to normal.
System Restart and Operational Update
Thursday, May 13, 9 a.m.
Link to blue/green map, found here
Colonial Pipeline has made substantial progress in safely restarting our pipeline system and can report that product delivery has commenced in a majority of the markets we service. By mid-day today, we project that each market we service will be receiving product from our system. The green segments on this map are operational, meaning product delivery has commenced. Blue lines will be operational later today.
This would not have been possible without the commitment and dedication of the many Colonial team members across the pipeline who worked safely and tirelessly through the night to get our lines up and running. We are grateful for their dedicated service and professionalism during these extraordinary times.
Colonial Pipeline May 12, 2021 Press Release
System Restart and Operational Update
Wednesday, May 12, 5:10 p.m.
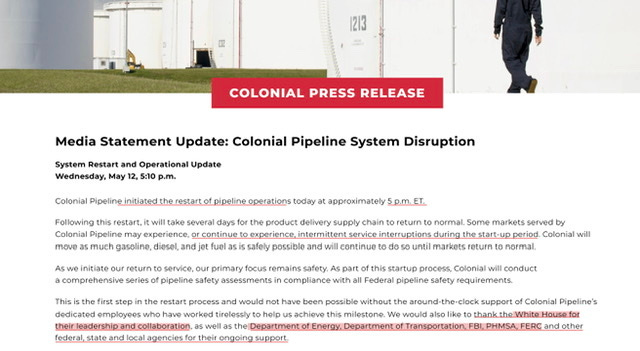
Colonial Pipeline initiated the restart of pipeline operations today at approximately 5 p.m. ET.
Following this restart, it will take several days for the product delivery supply chain to return to normal. Some markets served by Colonial Pipeline may experience, or continue to experience, intermittent service interruptions during the start-up period.As we initiate our return to service, our primary focus remains safety. As part of this startup process, Colonial will conduct a comprehensive series of pipeline safety assessments in compliance with all Federal pipeline safety requirements.
This is the first step in the restart process and would not have been possible without the around-the-clock support of Colonial Pipeline’s dedicated employees who have worked tirelessly to help us achieve this milestone. We would also like to thank the White House for their leadership and collaboration, as well as the Department of Energy, Department of Transportation, FBI, PHMSA, FERC and other federal, state and local agencies for their ongoing support.
Kind of weird not seeing TSA, DHS, CISA etc but I suppose one could argue that those agencies fall under the “and other federal…agencies”


Colonial Pipeline and third-party cybersecurity firm
In Colonial Pipeline’s Media Statement Update: Colonial Pipeline System Disruption - you’ll note the company cites “third-party cybersecurity firm” in their May 8th, 9th, and 10th -respectively.
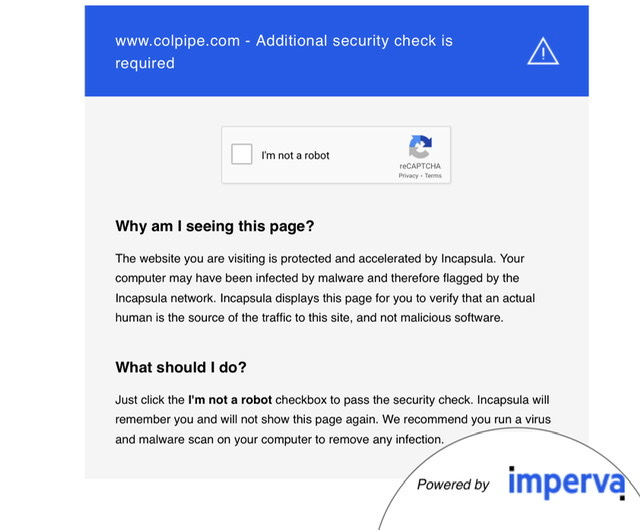
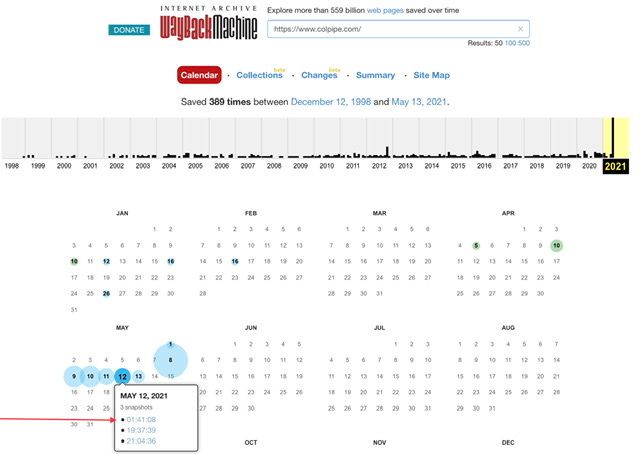
When reviewing Colonial Pipeline’s website - you’ll note that “Additional Security Check is required” - however a cursory view of the Internet Wayback Machine that wasn’t added to their website sometime between May 11, 2021 11:06PM to May 12, 2021 1:41AM
Which is pretty interesting- assuming Bloomberg’s reporting is accurate (and I have zero reason to believe that it’s not accurate:
Bloomberg Provided additional information about the DarkSide ransomware attack: noting that the attackers stole nearly 100GB of data from Colonial Pipeline and then began locking some of Colonial Pipeline’s computers and servers and ultimately demanding a ransom. Otherwise DarkSide stated they would publish the stolen data online if Colonial Pipeline refused to pay the ransom.
📍 Put a pin in this 📍 - DarkSide-Malware can run on both Windows and Linux platforms; Trojan-Ransom.Win32.Darkside1 and Trojan-Ransom.Linux.Darkside 2. DarkSide uses incredibly strong encryption algorithms, thus making data restoration sans the “correct” key almost impossible. And last month DataBreaches.net published what appears to be a lengthy interview with at least one of the DarkSide Hackers. I would highly recommend you read, found here
Imperva and Colonial Pipeline
For the record it’s unclear if Imperva and Colonial Pipeline had/have a contract that was executed before the May 8, 2021 major cyber breech. And that is something I would urge you to keep in mind. Notwithstanding based on preliminary research, it raises a lot of really uncomfortable questions. For Example;
August 2019 - Imperva blamed it on AWS - from Imperva’s CEO Blog - accidental exposures of internal systems on the internet.
“… identified an unauthorized use of an administrative API key in one of our production AWS accounts in October 2018, which led to an exposure of a database snapshot containing emails and hashed & salted passwords”
May 2021 Connectivity Issues - GRU (No that is NOT the Russian G. R. U. - it’s a data center) it took over 18 hours to resolve the connectivity issue
March 10, 2021 - Don’t be a victim of cyber extortion
Malicious hackers are exploiting zero-day vulnerabilities in new iterations of software, like the recent exploit of the popular File Transfer Appliance (FTA) from enterprise firewall company Accellion, to collect passwords and gain account access to company systems. The Accellion tool, which was vulnerable for an estimated 72 hours, continues to hit hundreds of high-profile targets from Harvard to Kroger and CSX to Flagstar Bank.
In 2020 the average ransomware demand rose by 33% (over the previous year) to $111,605 while the average cost of a data breach totaled US$3.86 million.
March 2021 - a DNS issue that took over 13.5 hours to resolve
And that’s what I found in under 2 minutes of researching. Again not to be repudiative - it’s not clear if Colonial Pipeline and Imperva had a service contract executed prior to this Month’s data breech or if Colonial Pipeline retained them after the breech. Oddly my questions and/or concerns cut both ways. As in I still have a lot of questions.
President Biden - Executive Order…Improving the Nation’s Cybersecurity
Which was released late in the evening of May 12, 2021 - the Executive Order, which reads in part
The Federal Government must bring to bear the full scope of its authorities and resources to protect and secure its computer systems, whether they are cloud-based, on-premises, or hybrid. The scope of protection and security must include systems that process data (information technology (IT)) and those that run the vital machinery that ensures our safety (operational technology (OT)).
It is the policy of my Administration that the prevention, detection, assessment, and remediation of cyber incidents is a top priority and essential to national and economic security. The Federal Government must lead by example. All Federal Information Systems should meet or exceed the standards and requirements for cybersecurity set forth in and issued pursuant to this order.
The reality is there are countless Cyber-Security Federal Contracts and many of them contain actual contract language that prohibits the “awardee” to disclose, alert and/or work with other Federal Agencies - unless expressly authorized to do so (F.A.R 3 and T.I.N.A. 4 )
Within 60 days of the date of this order, the Director of the Office of Management and Budget (OMB), in consultation with the Secretary of Defense, the Attorney General, the Secretary of Homeland Security, and theDirector of National Intelligence, shall review the Federal Acquisition Regulation (FAR) and the Defense Federal Acquisition Regulation Supplement contract requirements and language for contracting with IT and OT service providers and recommend updates to such requirements and language to the FAR Council and other appropriate agencies. The recommendations shall include descriptions of contractors to be covered by the proposed contract language.
Within 45 days of the date of this order, the Secretary of Homeland Security, in consultation with the Secretary of Defense acting through the Director of the National Security Agency (NSA), the Attorney General, and the Director of OMB, shall recommend to the FAR Council contract language that identifies:
…(D) the time periods within which contractors must report cyber incidents based on a graduated scale of severity, with reporting on the most severe cyber incidents not to exceed 3 days after initial detection…
The Federal Government must adopt security best practices; advance toward Zero Trust Architecture; accelerate movement to secure cloud services, including Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS); centralize and streamline access to cybersecurity data to drive analytics for identifying and managing cybersecurity risks; and invest in both technology and personnel to match these modernization goals.


And with that I think you have a decent amount of information and original documents. I’ll probably be offline for the remainder of the week since I still have a list, albeit a short list of projects that need to be completed. A side from the occasionally beach or sound videos…see ya in a few days.
Trojan-Ransom.Win32.Darkside - last visited May 12, 2021 - https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Ransom:Win32/DarkSide&ThreatID=2147768844
Trojan-Ransom.Linux.Darkside - last visited May 11, 2021 - https://www.fireeye.com/blog/threat-research/2021/05/shining-a-light-on-darkside-ransomware-operations.html
FAR, the Federal Acquisition Regulation governing executive agency procurement contracts – the main set of rules in the Federal Acquisition Regulations System for government procurement in the United States. FAR is codified at Chapter 1 of Title 48 of the Code of Federal Regulations, 48 C.F.R. 1.3
TINA, the Truth in Negotiations Act -codified under 10 U.S. Code § 2306a mandates that contractors performing government contracts for the U.S. Government to shall submit cost and pricing data that is truthful, accurate, and complete. The 2018 National Defense Authorization Act ( Section 811 ) increased the monetary TINA threshold from $750,000.00 to $2 million - applicable for all contracts entered into after July 1, 2018. Keep in mind that a contracting officer can still request cost or pricing data to support proposals under the TINA threshold, this cost/pricing data would not be certified, thus substantially reducing the offeror’s risk