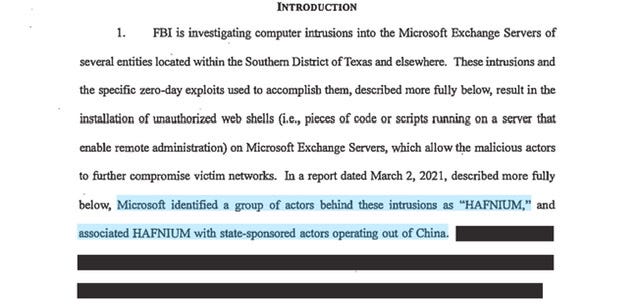
DOJ Announces Court-Authorized Effort to Disrupt Exploitation of Microsoft Exchange Server Vulnerabilities —> HAFNIUM <—
You naughty little web shell doing reconnaissance, playing hide and seek, and then infecting other networks with additional malware. China and their AI advancement a BIGLY PROBLEM. Command & Control
In order to fully understand the recent Department of Justice’s Press Release, it is important for you to understand HAFNIUM - in early March 2021 Microsoft Posted (on their technology blog):
HAFNIUM targeting Exchange Servers with 0-day exploits…
New nation-state cyberattacks - HAFNIUM
On March 2, 2021 Microsoft formally announced what they deemed to be “new nation-state-cyberattacks” —this announcement was extraordinary because it was the vert first time Microsoft publicly spoke about HAFNIUM and the first time they officially linked it to China.
HAFNIUM primarily targets entities in the United States across a number of industry sectors;
infectious disease researchers
law firms
higher education institutions
defense contractors
policy think tanks, and NGOs.
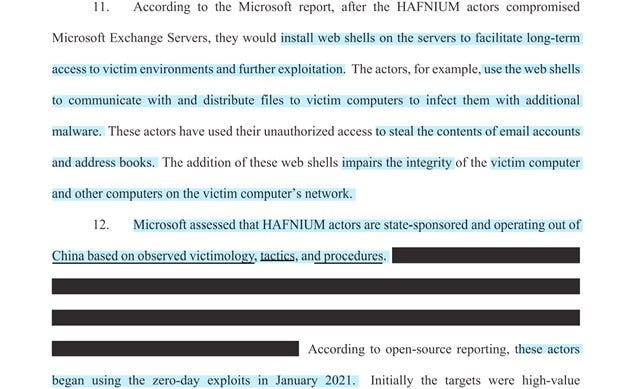
HAFNIUM previously compromised victims by exploiting vulnerabilities in internet-facing servers, and has used legitimate open-source frameworks, like Covenant, for command and control. Once they’ve gained access to a victim network, HAFNIUM typically exfiltrates data to file sharing sites like MEGA
Microsoft has observed HAFNIUM interacting with victim Office 365 tenants…this reconnaissance activity helps the adversary identify more details about their targets’ environments.
HAFNIUM operates primarily from leased virtual private servers (VPS) in the United States.
Over the course of the proceeding days Microsoft timely provided numerous updates, for example:
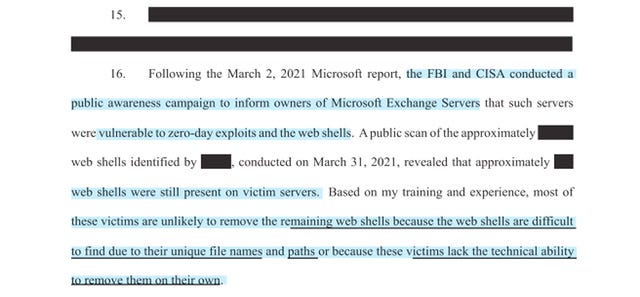
Update [03/04/2021]: The Exchange Server team released a script for checking HAFNIUM indicators of compromise (IOCs). See Scan Exchange log files for indicators of compromise.
Update [03/05/2021]: Microsoft sees increased use of these vulnerabilities in attacks targeting unpatched systems by multiple malicious actors beyond HAFNIUM. To aid customers in investigating these attacks, Microsoft Security Response Center (MSRC) has provided additional resources, including new mitigation guidance: Microsoft Exchange Server Vulnerabilities Mitigations – March 2021
Update [03/08/2021]: Microsoft continues to see multiple actors taking advantage of unpatched systems to attack organizations with on-premises Exchange Server. To aid defenders in investigating these attacks where Microsoft security products and tooling may not be deployed, we are releasing a feed of observed indicators of compromise (IOCs). The feed of malware hashes and known malicious file paths observed in related attacks is available in both JSON and CSV formats at the below GitHub links. This information is being shared as TLP:WHITE: CSV format | JSON format
Update [03/15/2021]: Microsoft released a new one-click mitigation tool, the Microsoft Exchange On-Premises Mitigation Tool, to help customers who do not have dedicated security or IT teams to apply security updates for Microsoft Exchange Server.
Update [03/16/2021]: Microsoft released updated tools and investigation guidance to help IT Pros and incident response teams identify, remediate, defend against associated attacks: Guidance for responders: Investigating and remediating on-premises Exchange Server vulnerabilities.
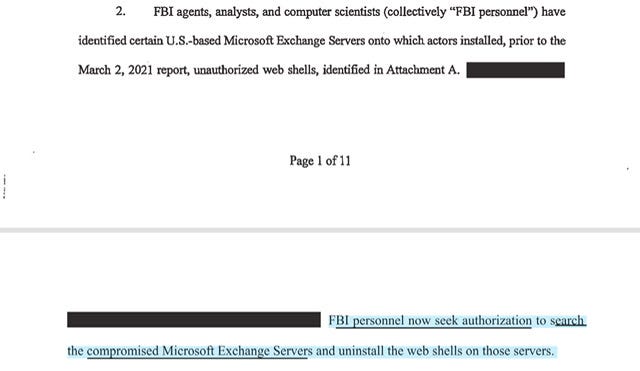
As alleged in the Affidavit from January thru February 2021, hackers exploited zero-day vulnerabilities in Microsoft Exchange Server software to access e-mail accounts and place web shells (which are pieces of code or scripts that enable remote administration) for continued access.
While other hacking groups appear to have waited until after Microsoft announced the vulnerabilities and releasing of patches to mitigate the “web shells” -they launched a second and more pernicious attack in March 2021. To Microsoft’s credit their constant updates allowed their customers and users to remove the “web shell” —other end users were unable to remove the “web shell—thusly resulting in hundreds web shells allowed to persist and unmitigated. Especially problematic under the “command and control” functionality.
Today’s operation1 2removed one early hacking group’s remaining web shells, which could have been used to maintain and escalate persistent, unauthorized access to U.S. networks. The FBI conducted the removal by issuing a command through the web shell to the server, which was designed to cause the server to delete only the web shell (identified by its unique file path).
FBI personnel now seek authorization to search the compromised Microsoft Exchange Servers and uninstall the web shells on those servers.
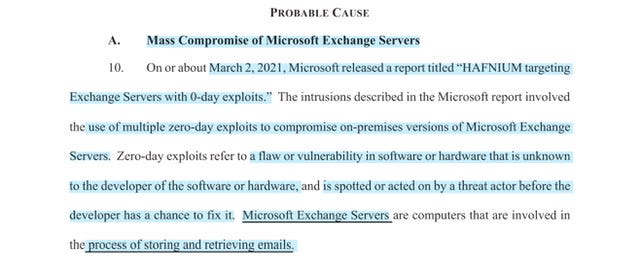
That is one helluva title for the subsection: “Mass Compromise of Microsoft Exchange Servers” as previously explained Microsoft’s March 2, 2021 Blog announcement of; “HAFNIUM targeting Exchange Servers with 0-day exploits.”
Once HAFNIUM is installed it had a reconnaissance function but more importantly, HAFNIUM’s web shells had a clever way of by-passing detection but it also had the ability to “communicate with and distribute files to victim computers to infect them with additional malware” and the Command and Control functionality is - kind of unnerving
Intriguingly HAFNIUM initially targeted (what China viewed) as “high value intelligence targets” and only later morphed into a much larger scope of targets. In my industry we refer to this kind of tactic as “release chaos” meaning by (what appears to be) indiscriminate “targeting of victims” this is how you unleash hell and you don’t even know where to start to mitigate the intrusion(s)
As the Affidavit explains one researcher stated; “…’mass exploitation’ and ‘indiscriminate’…seemingly targeting every Microsoft Exchange Server that could be identified..” - researchers and open source public reporting estimated some “60,000 Microsoft customers worldwide whose Microsoft Exchange Servers were compromised through the use of the zero-day exploits described by Microsoft” and while the IP addresses are redacted in the Affidavit - incidentally at some point I expect we will learn that IPv4 was utilized more than IPv6 <—because generally speaking 4 is easier to crack than 6 . Old School
I’m going with a few of the following IPs - (just to point out the obvious reasons) that were purportedly leveraged by HAFNIUM actors -because these were included in some of Microsoft’s Blog post. So it’s not like I’m pulling these out of thin air.
103.77.192.219 - 104.140.114.110 - 104.250.191.110 - 108.61.246.56 - 149.28.14.163
157.230.221.198 - 167.99.168.251 - 185.250.151.72 - 192.81.208.169 - 203.160.69.66
211.56.98.146 - 5.254.43.18 - 80.92.205.81
As noted in the Affidavit - on March 10, 20213 - the FBI-CISA Joint Advisory on Compromise of Microsoft Exchange Server;
In case you think that my nerd flag is flying high, um well YES it is. I genuinely enjoy this kind of reporting and how it marries the two things in my work life that I like the most —technology & law—INJECT THIS STRAIGHT INTO MY VEINS
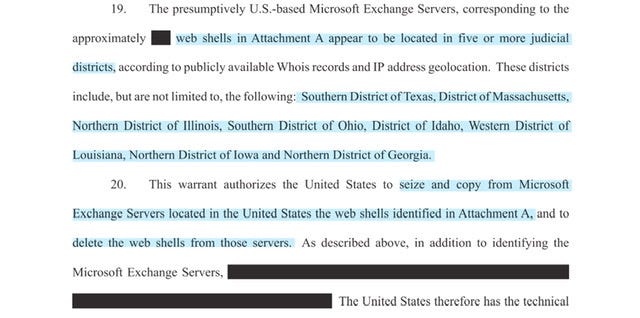
FBI personnel seek authorization to search the compromised Microsoft Exchange Servers and, through interactions with the web shells…uninstall…the web shells on those servers, which are identified in Attachment A. By deleting the web shells…FBI personnel will prevent malicious cyber actors from using the web shells to access the servers and install additional malware on them.
There are still hundreds of web shells that remain on U.S.-based computers running Microsoft Exchange Server software. This warrant is incredibly targeted and the scope is limited to tango-down the web shells - the Affidavit also disclosed were some of the servers are -
…the districts include, but are not limited to, the following: “Southern District of Texas, District of Massachusetts, Northern District of Illinois, Southern District of Ohio, District of Idaho, Western District of Louisiana, Northern District of Iowa and Northern District of Georgia.”
Hey remember that time in 2017, 2018 and 20194 and I was like “well done Microsoft” after they filed in the EDVA to essentially take back domains hackers purloined? Only to be relentlessly trolled for saying “um you may want to pay attention to what Microsoft is doing because it’s a novel and effective concept” -Yes those were super fun times.
And no I’m still not on Twitter nor do I have any plans to return to that cesspool of a platform. But I’ll admit it’s fun watching people beclown themselves trying to say XYZ account is me… bless their liddl’ hearts <snort>
DOJ-OPA Release No 21-319 April 14, 2021 https://www.justice.gov/opa/pr/justice-department-announces-court-authorized-effort-disrupt-exploitation-microsoft-exchange
Copy of Redacted Search and Seizure Warrant (note the appendices) -last visited April 14, 2021 https://www.justice.gov/opa/press-release/file/1386631/download
See March 10, 2021 Joint PSA concerning Microsoft Exchange Server Vulnerabilities https://us-cert.cisa.gov/ncas/current-activity/2021/03/10/fbi-cisa-joint-advisory-compromise-microsoft-exchange-server







holy shit balls... This is huge! Like you, tech and law are most interesting to me. I'm a geek too, though not as big as you I suspect. Wish we knew each other in person. I think we'd get along wonderfully!! Thanks for the details, as alway...
Perhaps we should just go back to paper pushing and throw all the servers out the window. (I’m being factious) Thank goodness for cyber security.