FIN7 aka Carbanak Group fourth defendant expected to plead guilty on November 22, 2021
If you know how to read a criminal docket pointing to; ladies and gentlemen we have a 4th plea agreement then you’d note that the parties apparently reached a plea agreement for Defendant Denys Iarmak
Good Morning -
If I did this correctly — this article should publish while I’m on the road back down to the State Capitol to continue my marathon client advocacy. I need to look a few lawmakers in the eyes as they try to screw over a client. Plus I’ve been ordered to give them a chance to ameliorate their follies. If they don’t I’ve been given the order to go full nuclear pitbull. I mean come on. Did you really think you could slip in those 3 pages and I wouldn’t notice? I have alerts setup for the legislative portal and I saw the proposed -not agreed upon- language within a minute of the filing in the LIS system.
Lastly with any luck and proper time management I’ll be done with lobbying and I can make my way back to the DC area for my late afternoon orthopedic appointment. Walking in high heels with an air cast is really growing old and I can’t chase down lawmakers as fast as I would normally do because -stupid-car-accident. -stupid broken foot- “nobody got time for that” -Sweet Brown
Before we dive into this case update, I should warn you that this is an extremely long and intensive article. Given my history and keen interest of FIN-7 and SEC and Botnets —it seemed like the right time to address FIN-7 in a wholistic manner versus bifurcating the four defendants. I would strongly recommend that you take breaks or understand that this is a much larger picture than I had previously tweeted/threaded or blogged about. That said and as standard practice I’ve made every effort to provide my readers with copious original documents and various industry reports. As you can imagine, this article has a decent amount of solid research. And perhaps chugging two 24oz Red Bulls before I put my eyeglasses on, cracked my knuckles and engaged my keyboard… so let’s just go ahead and dive head first into this …
Your Prerequisite FIN7 -Background-
In the summer of 2018 the Department of Justice announced the indictment of “Three Members of Notorious International Cybercrime Group “Fin7” in Custody for Role in Attacking Over 100 U.S. Companies”
Unless otherwise noted the embedded links in this article are almost exclusively from the Department of Justice -OPA —the embedded links as it relates to Defendant Denys Iarmak recent docket activity will be derived from WDWA-ECF and naturally I will provide a link to my Scribd Account for any ECF fling.
FIN-7 “…one of the most prolific financial threat groups of this decade..”
…FIN7 targeted and attacked hundreds of U.S. businesses… stole tens of millions of payment cards, and – by some estimates – caused over a billion dollars of damage.
April 2017 FireEye/Mandiant -FIN7 Evolution and the Phishing LNK report
August 2018 FireEye Report FIN-7
As noted by the Original August 2018 DOJ-OPA Press Release, which reads in part:
Ukrainian nationals Dmytro Fedorov, Fedir Hladyr, and Andrii Kolpakov, are members of a prolific hacking group widely known as FIN7 (also referred to as the Carbanak Group and the Navigator Group, among other names). Since at least 2015, FIN7 members engaged in a highly sophisticated malware campaign to attack more than 100 U.S. companies, predominantly in the restaurant, gaming, and hospitality industries. As set forth in the indictments, FIN7 hacked into thousands of computer systems and stole millions of customer credit and debit card numbers which were used or sold for profit.
…FIN7 would accompany the phishing emails with a telephone call to the victim company employee about the same topic, which was intended to legitimize the phishing email. The caller often directed the employee to the recently sent phishing email to further entice the employee to open the attached file and activate the malware.
To be clear, collectively FIN7 breached computer networks of companies in 49 states and the District of Columbia -below is a brief summary of just how pernicious this cyber-criminal group was:
stealing over 15 million customer card records from over 6,500 individual point-of-sale terminals at more than 3,600 separate business locations.
Companies that have publicly disclosed hacks attributable to FIN7 include such familiar chains as Chipotle Mexican Grill, Chili’s, Arby’s, and Jason’s Deli.
Case in chief - USA vs. Fedir Oleksiyovych Hladyr
If you followed me on Twitter then you already know that I’ve followed the FIN-7 indictments and plea agreements for a very long time. Side note, it never made any sense to me how this pernicious hacking group some how managed to infect thousands of computers and created thousands of victims. Yet somehow they skipped right past South Dakota but I digress… meaning FIN7 victims in 49 of our 50 states and the District of Columbia.
Defendant Feir Oleksiyovych Hladyr aka Fedor Gladyr, Fedir Oleksiyovych Gladyr, Glayr Fedir Oleksiyovych, Gladyr Fedor Oleksiyovich, Fedor, das, Fyodor, AronaXus -was known as a system administrator for FIN-7
Also see previously archived twitter thread -like I said this case has fascinated me for years. And after nearly three years, two plea agreements -recently a third plea agreement appears to have ironed out. Further in to this article, I’ll explain why I’m making that declarative statement -whispers- if you know how to read a docket then you know November 22, 2021 is a date long time coming for the fourth defendant Denys Iarmak. True story I wish I still had access to my Spicy Twitter account because I’m pretty sure Iarmak or one of his surrogates slid into my DMs. — Superseding Indictment in U.S. v. Hladyr
HLDADYR Plea Agreement - Defendant Hlydayr
April 18, 2021 -JUDGMENT as to Fedir Oleksiyovych Hladyr by Judge Ricardo S. Martinez —via WDWA-ECF
Defendant Hlydayr was sentenced to 120 months for Count 1 and 60 months for Count 16, to be served concurrently. Defendant shall be given credit for time served since January 10, 2018.
April 27, 2021 -AMENDED JUDGMENT for Fedir Oleksiyovych Hladyr (1) signed by Judge Ricardo S. Martinez -correction at page 6 re restitution- via WDWA-ECF
May 24, 2021 -SECOND AMENDED JUDGMENT for Fedir Oleksiyovych Hladyr (1)signed by Judge Ricardo S. Martinez. via WDWA-ECF -
Restitution in the amount of $2,500,000 is due immediately. Any unpaid amount is to be paid during the period of supervision in monthly installments of not less than 10% of his or her gross monthly household income. Interest on the restitution shall be waived.
Previous case update as to Hladyr
United States vs. Dmytro Valerievich Fedorov
If you want the accurate chronological order, then technically Defendant Fedorov was the first defendant that not only hammered out a plea agree but he was scheduled for sentencing months before his co-conspirator/co-defendant Hladyr. What is somewhat notable is Dmytro Valerievich Fedorov aka hotdima sentencing has been delayed to 2022 --that fun fact will come into play when we go over Defendant Iarmak’s recent docket updates. So for now please put a pin in that. Also of note Fedorov’s plea agreement has yet to be uploaded to the public docket.
Additionally as you’ll note the DOJ-OPA main landing page for FIN-7, Fedorov Indictment is a broken link. A casual observer might not understand what WDWA-ECF USA v Fedorov Document #20-2 which is Fedorov’s (redacted) superseding indictment. But I’d like to show you something -see the page count for Document No 20-2 —that tells you it’s far more exhaustive.
Document # 20-2 ←Defendant Fedorov Redacted Superseding Indictment
However -most overlooked the following adjunct case -so it’s time to take a quick detour from Fedorov and examine Defendant Kolpaov’s case…
United States vs. Andrii Kolpakov
Defendant -Andrii Kolpakov aka Andrey Kolpakov, Andriy Kolpakov, Andre Kolpakov, Andrew Kolpakov, santisimo, santisimoz, AndreyKS.
U.S. v. Kolpakov Indictment
November 16, 2020 KOLPAOV Plea Agreement
…No hacking group epitomizes the industrialization of cybercrime better than the FIN7 criminal enterprise. FIN7 has had over 70 members who were organized into discrete departments and teams…
June 27, 2021 -SENTENCING MEMORANDUM by USA as to Andrii Kolpako. See WDWA-ECF
Note the footnotes which includes the various DOJ-OPA Press Releases…because as noted in Kolpaov’s Sentencing Memo filed by the USA. Also October 8, 2017 Footprints of FIN7: Pushing New Techniques to Evade Detection
…What was once the province of lone wolf hackers, became a crowded space filled with financially motivated hacking crews led by charismatic hackers such as Roman Seleznev 1 2 3 4 5 and David Schrooten 6 7, who were sentenced in this district to 27 and 14 years, respectively. At the peak of their exploits, Seleznev and Schrooten were viewed as pioneers in their field, with Seleznev’s crew gaining particular notoriety for selling information for millions of stolen payment cards.
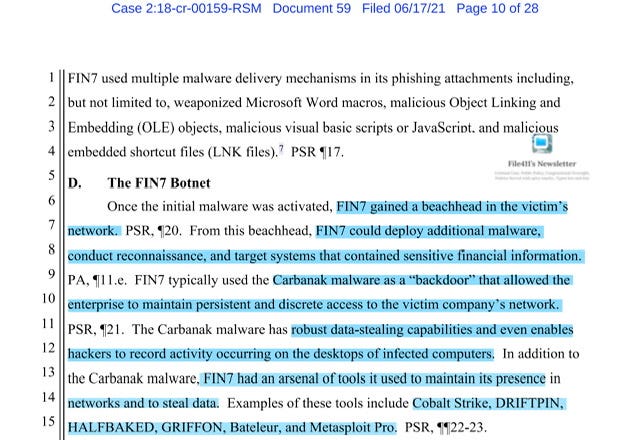
To those who previously said I was wrong that FIN7 didn’t have a botnet, I regret to inform you that one of us was wrong and one was correct -I now refer you to pages 10 & 11 of the USA Sentencing Memo regarding Defendant Kolpaov. Wait am I reading that correctly? Why yes -yes I am The FIN7-Botnet -also FIN7 created numerous “fake” IT Security Companies -see TechCrunch October 2021 article
…add an unlimited number bots to the botnet…
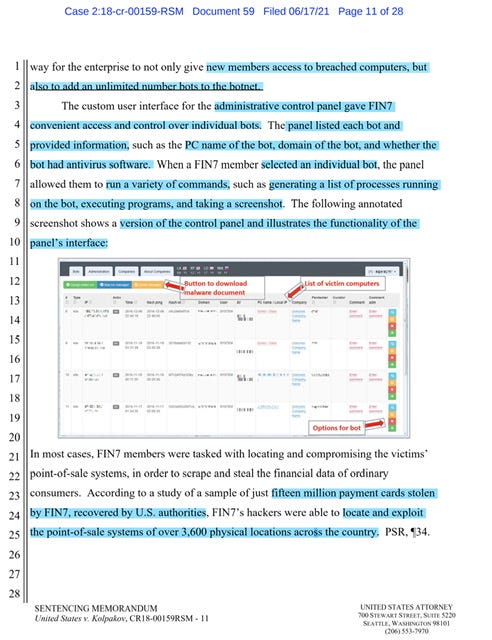
…custom user interface for the administrative control panel gave FIN7 convenient access and control over individual bots. The panel listed each bot and provided information, such as the PC name of the bot, domain of the bot, and whether the bot had antivirus software. When a FIN7 member selected an individual bot, the panel allowed them to run a variety of commands, such as generating a list of processes running on the bot, executing programs, and taking a screenshot. The following annotated screenshots shows a version of the control panel and illustrates the functionality of the panel’s interface…
Let’s not overlook page 7 of the Sentencing Memo filed by USA - why yes S.E.C. if only I could retweet those SEC data breach threads -but nope I can’t. La sigh. In June of 2018 Spanish Authorities arrested Defendant Kolpaov (MLAT baby MLAT) who was vacationing in Lepe, Spain at the request of our Government. Spanish Authorities discovered the Defendant was in possession of various electronic devices, including an Asus laptop computer (with hard drives), storage devices, and a mobile phone which were used to further facilitate the scheme.
Asus laptop, model no. X510U (serial no. HANOCX24R525436);
Toshiba 128 GB SSD (serial no. 671510BATMXT);
SATA hard drive (serial no. 87VEC1G9T SWF HDKCB8888E0A01T);
Gold colored Samsung SM J500H Galaxy J5 cell phone (serial no. RV1H40M03WV, IMEI 357950071755024/01 and 35800071755027/0); and
Various SIM cards.
Upon Kolpaov’s arrest his “travel companion” altered other FIN-7 members that Kolpaov was in custody. As further elucidated in the Sentencing Memo -the enhancement was/is kind of a really big deal…as this signals Kolpaov’s level of involvement. Spoiler he was pretty high on the FIN-7 leadership food chain.
June 14, 2021 - JUDGMENT as to Andrii Kolpakov by Judge Ricardo S. Martinez. See WDWA-ECF
June 21, 2021 -ORDER granting 57 Motion to Seal Document as to Andrii Kolpakov (1) signed by Judge Ricardo S. Martinez. See WDWA-ECF
The Motion filed by Defendant Kolpaov to submit his sentencing memo under-seal is actually pretty notable. The inference is there has to be some information that the prosecutors do not want publicly released (yet)…and the “yet” is important because that ties Defendant Iarmak’s plea agreement.
United States vs. Denys Iarmak (4th Defendant)
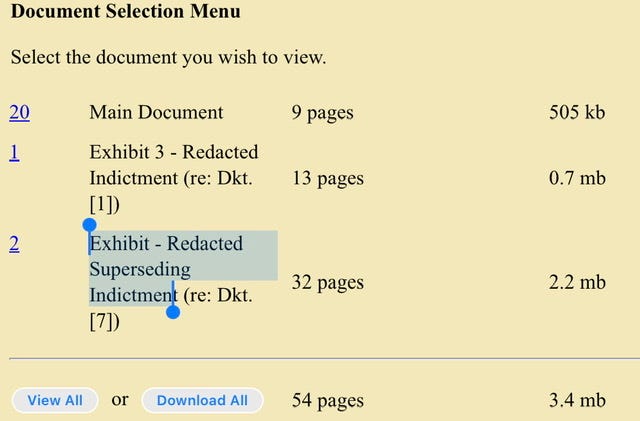
United States v. Iarmak (2:19-cr-00257-RSM) Indictment here’s how you know that Defendant Iarmak has hammered out a plea agreement - you simply need to pay attention to the filings/docket entries and what I’ve put in bold font
July 20, 2020 -AMENDED ORDER CONTINUING TRIAL DATE by Judge Ricardo S. Martinez as to Denys Iarmak. This Amended Order supersedes 31 Order on Motion to Continue Trial. (cc: PTS/USPO, USMO) Jury Trial is set for 9/13/2021 at 09:00 AM before Judge Ricardo S. Martinez. Motions due by 5/7/2021. WDWA-ECF
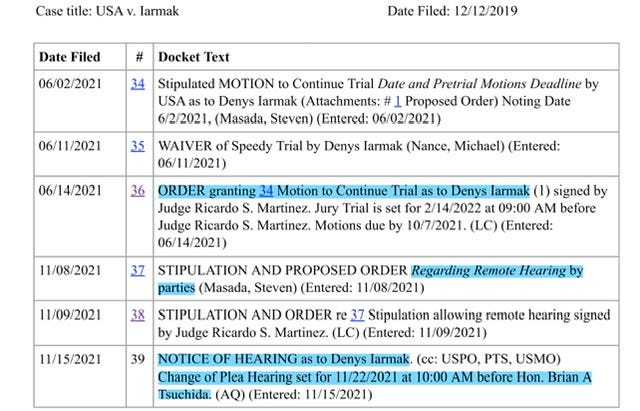
June 24, 2021 - ORDER granting 34 Motion to Continue Trial as to Denys Iarmak (1) signed by Judge Ricardo S. Martinez. Jury Trial is set for 2/14/2022 at 09:00 AM before Judge Ricardo S. Martinez. Motions due by 10/7/2021. WDWA-ECF
November 9, 2021 - STIPULATION AND ORDER re 37 Stipulation allowing remote hearing signed by Judge Ricardo S. Martinez. WDWA-ECF
For the record if you take the time to actually read every page on a docket then you’ll note a very interesting rationale proffered in paragraph 12:
…Based on the foregoing, the parties therefore stipulate and agree that the change in plea hearing cannot be further delayed without serious harm to the interests of justice and should be conducted via videoconference…
November 15, 2021 NOTICE OF HEARING as to Denys Iarmak. (cc: USPO, PTS, USMO) Change of Plea Hearing set for 11/22/2021 at 10:00 AM before Hon. Brian A Tsuchida. (AQ) (Entered: 11/15/2021) WDWA-ECF Docket Report
What happens next?
As it related to Defendant Denys Iarmak -it is a lock that a plea agreement will be uploaded to the docket just prior to his November 22, 2021 “change in plea hearing” so I would absolutely keep your eyes peeled for a Plea Agreement. If I were to take an educated guess —I’ll bet you a cheeseburger that Iarmak’s plea agreement will appear on the docket either in the late evening of the 21st or in the early morning of November 22, 2021. And yes of course once that plea agreement is on the public docket I will do my level best to update my readers in a timely manner.
Important Fedorov sidebar:
United States vs. Dmytro Valerievich Fedorov case if you drill down in the superseding/redacted indictment -you’ll note an individual known as “F.H.” and an educated guess would be “Individual F.H.” is Fedir Oleksiyovych Hladyr
Hence Dmytro Valerievich Fedorov has become an enigma, wrapped in a riddle, and shrouded in mystery (yes I know that’s not the accurate Sir Winston Churchill quote) When you factor in the Government’s sentencing memorandum as to Defendant Iarmak —the urgency in which the Government & Defendant want to proceeding with sentencing it does make me wonder if previous public reporting got it wrong and Fedorov is the actual ring leader.
Which would be really bad news for him. Why? Well I will remind you that on November 22, 2021 co-conspirator Iarmak’s plea agreement will hit the docket. My parting words and necessary pretext: I am hedging my bets that Defendant Fedorov at the top of the food chain if not the apex but I do not feel comfortable stating *factually speaking” that to be the case. Eventually we will know if my speculation (educated guess is correct or I’m batting out of my league. Whispers I don’t think I am and that will only be confirmed when various sealed filings are unsealed. Patience isn’t my strong suit but I do need to be clear, my Fedorov assertion is speculative, for now.
Open Source Link to (recent) Court Filings
USA v Fedorov Superseding Indictment (redacted)
USA v FEDIR HLADYR -2nd Amend Judgement May 2021
USA v Iarmak -ORDER Nov 2021 -Change in Plea Hearing
The main Department of Justice - Complex Litigation page for these four defendants can be found here and not to belabor the point —keep an eye out for Iarmak’s Plea Agreement (these are usually uploaded the night before or the morning of said Change in Plea Hearing).
Lastly sincere apologies for the length of this article, and the numerous court filings and other supporting documents/reports. I do like to be extremely thorough. Consider it a work hazard. If you haven’t figured out why I consistently obsessed over this case. Setting aside that the FBI Agents incontrovertible “pursuit of justice” —at the time these indictments were unsealed —this was a significant cyber-criminal roll up and it was a years long investigation.
But the underlying reason is I’m pretty sure this ties to at least two other cases. One of which involves my pet “Yevgeniy Alexandrovich Nikulin” And my educated guess is there might be a portion of the investigation might (operative word) still be very much ongoing;
Electronic Data Gathering, Analysis, and Retrieval (EDGAR)
September 27, 2017 the S.E.C. chairman issued the following statement (also see this SEC link) and this disclosure was done in a rather peculiar way -at time I believe I believe I tweeted something to the effect:
Review of 2016 Cyber Intrusion Involving EDGAR System -
…the 2016 intrusion has now determined that an EDGAR test filing accessed by third parties as a result of that intrusion contained the names, dates of birth and social security numbers of two individuals. This determination is based on forensic data analysis conducted since the agency's Sept. 20th disclosure of the intrusion which relied on the latest information available at that time.
And then on October 2, 2017 The S.E.C. Chairman Clayton Provides Update on Review of 2016 Cyber Intrusion Involving EDGAR System as noted by the S.E.C. Chair -this was a multistage cybercrime-ing. The first phase hackers (and/or hacker groups) targeted numerous news-wire agency and the second phase was to compromise the S.E.C. EDGAR system. Ultimately in January 2019 this resulted in the SEC filing charges against 13 individuals/entities 8 —again I’m not 100% positive these are FIN-7 and EDGAR cyber-criminals are interconnected…
And with that I am fairly confident that you now have the same amount of factual information that I have.
-Filey
See DOJ-OPA Thursday, October 9, 2014 Alleged Russian Cyber-Criminal Now Charged in 40-Count Superseding Indictment -40-count superseding indictment alleges that Roman Valerevich Seleznev, aka “Track2,”
See DOJ-OPA August 25, 2016 - Russian Cyber-Criminal, Roman Valerevich Seleznev -Convicted of 38 Counts Related to Hacking Businesses and Stealing More Than Two Million Credit Card Numbers - Hacking Scheme Defrauded Banks of More Than $169 Million
See DOJ-OPA Thursday, November 30, 2017 -Russian Cyber-Criminal Sentenced to 14 Years in Prison for Role in Organized Cybercrime Ring Responsible for $50 Million in Online Identity Theft and $9 Million Bank Fraud Conspiracy
See DOJ-OPA Friday, May 19, 2017 Convicted Russian Cyber Criminal Roman Seleznev faces charges in Atlanta
See DOJ-OPA Friday, September 8, 2017 - Russian cybcercriminal Roman Seleznev pleads guilty in Atlanta
See DOJ-OPA June 11, 2012 - Dutch Citizen Arrested And Extradited From Romania For Computer Hacking Conspiracy That Victimized Thousands Of Credit Card Customers -Seattle Area Businesses had their Point of Sale Computers Hacked, Information Stolen
See DOJ-OPA Friday, February 1, 2013 -Dutch Citizen Sentenced to 12 Years in Prison for Computer Hacking Scheme that Stole and Sold Credit Card Info - Local Businesses And Customers Victimized By Hacking Scheme
See Securities and Exchanging Commission -Press Release January 2019 (see footnote # 7 for the S.E.C court filings) SEC Brings Charges in EDGAR Hacking Case











Wow! That's a great article my dear. I don't understand it all, but you're really good at your work. I don't know how you do it. You're going through so much. I hope you're healing and taking care of yourself. Kudos my dear. You are quite impressive. I wish I had your energy.😉💗
Thx! Well ... at least you're not trying to navigate icy sidewalks in heels and an airboot! At least not yet! Hang in there :)