I don’t WannaCry...said Kim Jong-un. I just need more crypto currency because the sanctions are killing my vibe and money flow.
DOJ-OPA on February 17, 2021 Government unsealed an indictment-charging 3 Korean Military Hackers Indicted in Wide-Ranging Scheme to Commit Cyberattacks and Financial Crimes Across the Globe
A long time ago I casually said… hey if you want to evade crippling sanctions - cryptocurrency is the way to go and here we are…With the recently unsealed indictment1regarding the Creation of WannaCry Ransomware 2.0 - which added two additional New Defendants and details the recent Schemes to Steal Money and Cryptocurrency from Banks and Businesses.
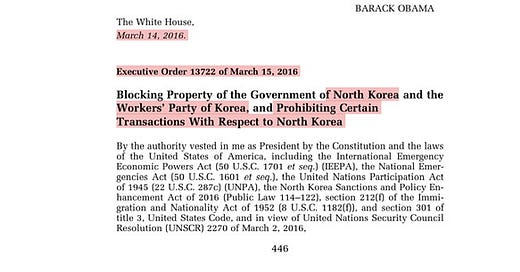
A bit of a historical and factual rewind, on September 13, 2019 - US Treasury which was a progeny of the March 2016 Executive Order, under then President Obama
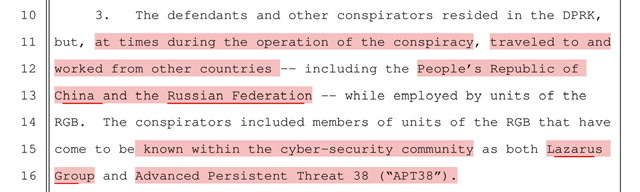
North Korean hacking groups commonly known within the global cyber security private industry
Executive Order 137222 “Lazarus Group,” “Bluenoroff,” and “Andariel” as agencies, instrumentalities, or controlled entities of the Government of based relationship to the Reconnaissance General Bureau (RGB). Lazarus Group, Bluenoroff, and Andariel are controlled by the U.S.- and United Nations (UN)-designated RGB, which is North Korea’s primary intelligence bureau.
this malicious cyber group is subordinate to the 110th Research Center, 3rd Bureau of the RGB. The 3rd Bureau is also known as the 3rd Technical Surveillance Bureau and is responsible for North Korea’s cyber operations. In addition to the RGB’s role as the main entity responsible for North Korea’s malicious cyber activities, the RGB is also the principal North Korean intelligence agency and is involved in the trade of North Korean arms.
The RGB was designated by OFAC on January 2, 2015 pursuant to Executive Order 136873 for being a controlled entity of the Government of North Korea
Targeting of and Cyberattacks on the Entertainment Industry:
Sony Pictures Entertainment was hit with a massive cyber attack in November 2014 in retaliation for “The Interview,” a movie that depicted a fictional assassination of the DPRK’s. In December of 2014 the cyber criminals then targeted AMC Theatres. In mid-2015 an intrusion of Mammoth Screen, which was producing a fictional series involving a British nuclear scientist taken prisoner in DPRK.
Wanna(cry) and evade crippling sanctions? Then get a gang of cyber criminals and unleash malware specifically targeting cryptocurrency
2015 throughout 2019, cyber criminals the big money heist: stealing more than $1.2 billion from banks in Vietnam, Bangladesh, Taiwan, Mexico, Malta and Africa. These cyber criminals hacked the various banks’ computer networks. Then sent fraudulent Society for Worldwide Interbank Financial Telecommunication (SWIFT) messages.
FAST CASH: ATM Cash-Out TheftsmThefts through ATM cash-out schemes – referred to by the United States Government as “FASTCash” – including the October 2018 theft of $6.1 million from BankIslami Pakistan Limited (BankIslami).
Ransomware and Cyber-Enabled Extortion. Pay us or we unleash cyber hell and own your network until you pay us…
WannaCry 2.0 was ransomware largely deployed in May 2017. The intent was extortion and attempted extortion of victim companies. This cyber attack occurred over a protracted period (from 2017 through 2020) hackers targeted the theft sensitive data and deployment of other ransomware. Which is stunning because stealing other ransom wear is a cruel twist of irony given the legacy of Wannacry… meaning once our NSA’s tool was made public -it was re-engineered and gave birth to WannaCry and dozens of other super pernicious and gnarly malware.
Creation and Deployment of Malicious Cryptocurrency Applications:
the development of numerous targeted malicious cryptocurrency applications ran far more recent than most of us knew. Today the DOJ announced timeframe from March 2018 through at least September 2020 and included the deployment of;
Celas Trade Pro4, WorldBit-Bot, iCryptoFx, Union Crypto Trader, Kupay Wallet, CoinGo Trade, Dorusio, CryptoNeuro Trader, and Ants2Whale
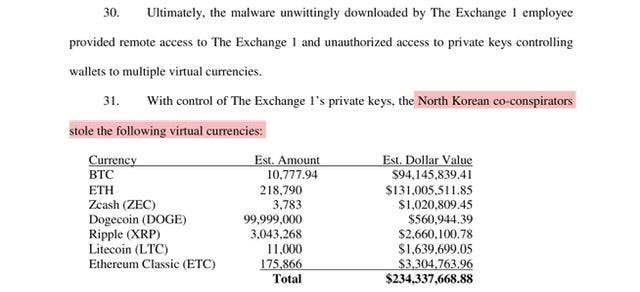
All of which would provide the North Korean hackers a backdoor into the victims’ computers.5 and if you followed me on Twitter then you know for years I’ve been monitoring and tracking this particular case -specifically due to the massive heist by North Korean Hackers, see page 8 of March 2020 FORFEITURE IN REM - 113 cryptocurrency wallets seized…
February 17, 2021 Indictment summary:
Defendants6 are as followed:
JON CHANG HYOK, aka “Quan Jiang,” aka “Alex Jiang,”
KIM IL, aka “Julien Kim,” aka “Tony Walker,” and
PARK JIN HYOK, aka “Jin Hyok Park,” aka “Pak Jin Hek,”aka “Pak Kwang Jin,”
During the operation of the “conspiracy” - prosecutors allege that the defendants traveled to and from North Korea to work in other countries -- including the People’s Republic of China and the Russian Federation. While simultaneously working for North Korea’s RGB7
There’s also another interesting tidbit, prosecutors allege that the hackers also sought to cause damage to victim computers via hacks in response to perceived reputational harm or to obtain information furthering strategic interests of the DPRK regime. Which is classic cyber-espionage and indicative of KJU’s feelings getting hurt so he sends his cyber-gang to rain terror on victims.
Hackers targeted; entertainment companies, financial institutions, cryptocurrency companies (including cryptocurrency exchanges, traders, and marketplaces), online casinos, cleared defense contractors, energy utilities.. Victims from; Bangladesh, Malta, Mexico, Indonesia, Pakistan, the Philippines, Poland, the Republic of Korea, Slovenia, Taiwan, the United Kingdom, Vietnam, Central America, and Africa -- as well as in the United States - did I mention how persistent this was?
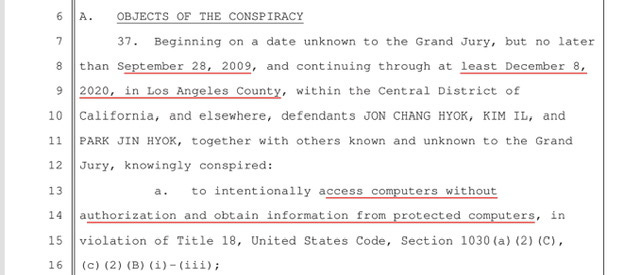
Astonishingly in Count one of the indictment - prosecutors are alleging the Conspiracy ran from “September 28, 2009, and continuing through at least December 8, 2020” - I could be wrong but I believe that is a lot longer than most of us previously knew.
Targeting of Cryptocurrency Companies and Theft of Cryptocurrency - in short evading sanctions (again);
While some might disagree, my opinion is North Korea’s cyberskills are consistently under appreciated. Throughout the years North Korean hackers have emerged as some of the most sophisticated, and I’m speaking globally. These cyber criminals targeted of hundreds of cryptocurrency companies and purloined tens of millions of dollars’ worth of cryptocurrency. For Example;
$75 million from a Slovenian cryptocurrency company in December 2017; (NiceHash), $24.9 million from an Indonesian cryptocurrency company in September 2018; and $11.8 million from a financial services company in New York in August 2020 in which the hackers used the malicious CryptoNeuro Trader application as a backdoor.
Spear-Phishing Campaigns but this time on steroids;
The hackers engaged in a nearly four year long multiple spear-phishing campaigns. Which specifically targeted employees of United States, such as; cleared defense contractors, energy companies, aerospace companies, technology companies, the United States Department of State, and the United States Department of Defense. At some point we should expect this to tie back to the OPM data breach. Think about the timeframe, North Korea was actively engaging in a four year long cyber attack all while Trump was “courting” Kim Jong-Un…. seriously talk about the biggest foreign policy failure.
NEW -Marine Chain Token and Initial Coin Offering:
North Korean hackers later developed (mid 2017 thru 2018) a Marine Chain Token. This allow “investors” the ability to purchase fractional ownership interests in various marine shipping vessels. Which were financially supported by a blockchain. In some respects DPRK “creation” allowed them to secretly tap into funds from investors, control interests in marine shipping vessels, and of course, the main objective, evade U.S. sanctions.
…I am curious why now? If you look at the date the Grand Jury handed down the indictment December 8, 2020 - so it remained sealed until today. Incidentally I suppose I should catch y’all up on the Virgil Griffith case too… because it has been a while. And I’m pretty sure there might be a link. Again the February 17, 2021 DOJ-OPA, found here. The indictment found here and highlighted/annotated indictment found here - and I think you’re caught up. Please feel free to comment or post a question, I’ll do my best to respond in a timely manner.
For the record Trump can’t take credit for Executive Order 13722 - nope this designation occurred under the Obama Administration
Technically speaking President Obama’s Executive Order 13722 was in fact a progeny of Executive Order 13687 of January 2, 2015
See USA v. 113 VIRTUAL CURRENCY ACCOUNTS https://ecf.dcd.uscourts.gov/doc1/04517692564 or via my public drive
Throughout the newly unsealed indictment prosecutors reference the 2019 United Nations Report: https://documents-dds-ny.un.org/doc/UNDOC/GEN/N19/028/82/PDF/N1902882.pdf?OpenElement
In other but absolutely related news - Feb 9, 2021 AP: UN experts: North Korea using cyber attacks to update nukes “North Korean hackers stole $316 million The panel recommended that the Security Council impose sanctions on four North Korean men: Choe Song Chol, Im Song Sun, Pak Hwa Song, and Hwang Kil Su.”





I don't understand how you keep all this straight, and up to date no less...