FINALLY - yes- Alla Witte, aka “Max” banking trojan known as Trickbot
Latvian National Charged for Alleged Role in Transnational Cybercrime Organization - it’s the weekend so what happens on the weekend? Red Bull Chugged. Glasses on. Keyboard engaged. Let’s do this
Malware is a National Security Threat
Paying a ransom is a very very bad idea. Nexus to OFAC, Sanctions, Colonial Pipeline $4.4M but lesser known. CNA Financial Corporation paid $40,000,000.00 in ransom - OFAC Oct 2020 Nat Sec & Nexus CNA
Biden White House National Security Study Memorandum -Fight Against Corruption- ahead of G7 & NATO summits (next week) timing matters - enhancing criminal and civil enforcement under the Global Magnitsky Act, TOP Priority. Also enforcement of the Justice Department’s Kleptocracy Asset Recovery Initiative.
,
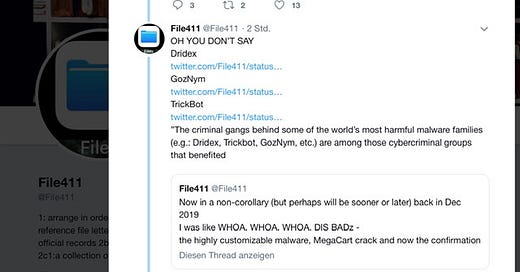
During my tenuous time on Twitter - I had a certain soft spot for hackers, malware and transnational organize crime. And if you followed what ever iteration of my Twitter account - then you’ll recall my unusual fascination with specific malware and various groups. For Example;
March 2020 - combo thread of threads (archived) where I drilled down on the emergent malware and what folks should keep an eye on.
or this Twitter thread within a thread archive - Latvia Georgia Bulgaria Romania Belgium QQAAZZ network opened and maintained hundreds of corporate and personal bank accounts at financial institutions throughout the world to receive money from cybercriminals who stole it from bank accounts
May 2020 Twitter Thread - archived
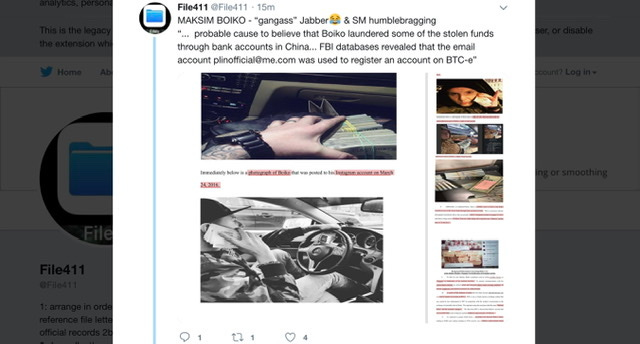
May 2020 Twitter Thread - archived -Maksim Boiko MAKSIM BOIKO a/k/a Maxim Boyko a/k/a “gangass”
What is TrickBot and why you should be concerned
You should watch this video - trust me it’s worth the six minutes to watch. Rosenquist makes a lot of salient data points and explains the complexity in an easy to understand oral presentation…
TrickBot -Defendant Alla Witte, aka Max
It is a pretty long indictment and Defendant Witte was only charge with 19 counts of a 47-count indictment. But a couple of things that I’d like to point out before we get into the details of the indictment. Defendant Witte has been in Federal Custody since her February 6, 2021 arrest in Miami, FL (SDFL) February 8, 2021 SDFL MJ Case No: 1:21-mj-02236-AOR-1
Magistrate Removal of Indictment from USDC for the Northern District of Ohio Case number in the other District 1:20-cr-440 as to Alla Witte
Minute Order for proceedings held before Magistrate Judge Alicia M. Otazo-Reyes: Initial Appearance as to Alla Witte held on 2/8/2021.
Date of Location Custody (Arrest or Surrender): 2/6/2021.
Waived personal appearance. Detention Hearing set for 2/11/2021 10:00 AM in Miami Division before MIA Duty Magistrate. Removal Hearing set for 2/11/2021 10:00 AM in Miami Division before MIA Duty Magistrate. Russian Interpreter present. Attorney added: Noticing FPD-MIA for Alla Witte
Now let’s look at page 1 of the newly unsealed indictment - see the redacted boxes? Based in part formatting (font and size), pursuant to local rules, I can make an educated guess as to how many co-defendants. I’m pretty confident that there are anywhere between 5 to 8 co-defendants who’s identity is presently redacted. But if you’re followed the TrickBot Gang then you’d know there could be up to 17 total defendants +/- 1.
April 20, 2021 DOJ Ransomware Task Force
As previously reported, back in April of 2021- the Department of Justice established a ransomware task force. As you’ll note, the scope of the Task Force is pretty broad and at times narrowly specific. Yes I understand how paradoxical that sentence is. As set-forth in the DOJ April 20, 2021 Memorandum —if you read the DOJ Memorandum in concert with the May 12, 2021 President Biden Executive Order Improving the Nation’s Cybersecurity —I think one could make a pretty convincing argument that the newly (partially) unsealed indictment.
For the week of May 31, 2021 - reports of two new ransomware infections.
Cox Media Group according to The Record Cox’s livestreaming for TV stations and other internal networks went tango down. Intermittent livestreaming & other services. It appears to have taken several hours for Cox to repair the cyberattack - MTTR is no joke -
UF Health Central Florida -access to email and most other system platforms went down for several hours.. UF Healt Staff at hospitals and physician clinics restored to using pen and paper to document patient records.
June 3, 2021 DOJ Memo Ransomware Task Force
The upside of the DOJ Ransomware Task Force is it oddly centralizes cases. Meaning the task force can gather intelligence across the intelligence community, track investigations and then coordinate all criminal cases that center around ransomware or related types of cybercrime - for example botnets, money laundering, cryptocurrency to pay ransom and bulletproof hosting.
Late on the evening of June 3, 2021 —a friend tipped me off saying that I might want to check the DOJ website. Indicating that there was a second memo from the Deputy Attorney General to ALL USAO which sets forth a bunch of new policies and guidance…
Effective immediately (on June 3, 2021) all Federal Prosecutors must abided by the “new” Department of Justice “ransomware task force” policy. The new policy subtext is driving home the urgency and “time is of the essence” while attempting to better streamline information flow, specifically the investigatory and prosecutorial developments. The June 3, 2021 Memo can be pulled down from my public drive
TrickBot Indeed unsealed June 3, 2021
Like I said TrickBot is a pernicious banking Trojan malware but it was also a product of cyber-Dwanism. Because Trickbot is a progeny of Dyre. Which was discovered in the wild in 2014. At the time researcher concluded that Dyre targeted computers running Windows. In addition it was also discovered that Dyre targeted web browsers, Chrome, Firefox, and Explorer. But what’s kind of important is researcher have hypothesized Dyre is a progeny of Zeus
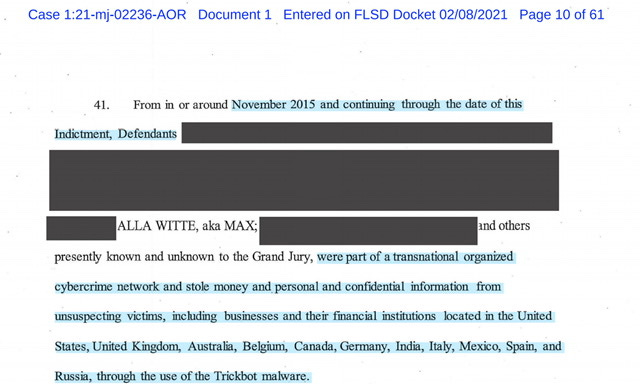
Which is important when you read paragraph 41 of the newly unsealed (partially redacted) indictment, which is dated February 2021 - which is also important, given many thought TrickBot went tango down in 2019…turns out that assumption was entirely incorrect.
November 2015 and continuing through the date of this Indictment…Defendants [heavily redacted]…were part of a transnational organized cybercrime network and stole money and personal and confidential information from unsuspecting victims, including businesses and their fmancial institutions located in the United States, United Kingdom, Australia, Belgiuni, Canada, Germany, India, Italy, Mexico, Spain, and Russia, through the use of the Trickbot malware.
Russia, Belarus, Ukraine and Suriname…
The harvesting of personal identifiable information is ominous and onerous because talk about identity theft on a global scale. The expertise required to calibrate a malware with this much precision is something that should send a shiver up your spine.
Transnational Organized Cybercrime Network
Look in late 2018 thru Jan 2021 I took a lot of shit for saying that the various cybercrimes were being committed by “gangs” and that it was “probably an organized collective of highly skilled hackers and programmers” at the time the incoming circular firing squad telling me I was wrong and completely off the mark. It didn’t really phase me because I had spent months reading and researching and I made my statement based on the preponderance of facts in hundreds of pages in various Court filings. But to my critics, stalkers and haters
Suck it. You were wrong (yet again)
I am done with some on Twitter who speciously attack the Justice Department just so they can monetize their uninformed musings via books, paid tweets and podcasts. You worthless dirty duplicitous pieces of fake disinformation shit. Your attacks on both the Department of Justice, the FBI and particularly Attorney General Garland are unpatriotic, uninformed and you deserve to be known as the QANON-FOR-THE-LEFT
You need to shut your filthy stupid megalomaniac pie holes and start reading the fucking court filings before you open your mouths. Capire? Just Omertà because the more you talk the more insane you sound. Good lord I’ve been holding that in since early 2018 - stop believing the QANON-for-the-Left they are only making you “mo’ stupider”…
now where was I…oh yes paragraphs 44 and 45…
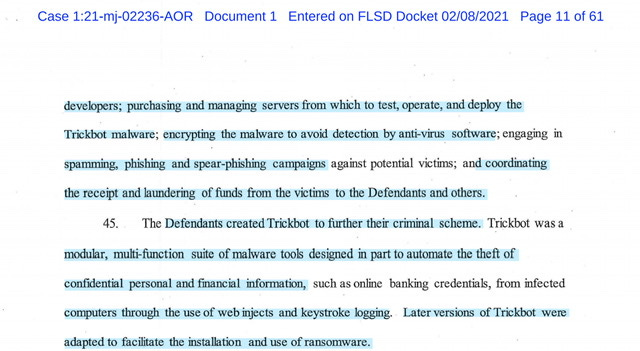
…specialized skills and services included soliciting and recruiting malware developers; purchasing and managing servers from which to test, operate, and deploy the Trickbot malware…encrypting the malware to avoid detection by anti-virus software; engaging in spamming, phishing and spear-phishing campaigns against potential victims; and coordinating the receipt and laundering of funds from the victims to the Defendants and others.
….computers through the use of web injects and keystroke logging.
Later versions of Trickbot were adapted to facilitate the installation and use of ransomware.
If you take the time to read pages 8 thru 12 of the Indictment —then you’ll note; Russia. Russia. Russia.
Defendant Alla Witte aka Max’s Role
Whoa the developer for the TrickBot Group… to say this operation was sophisticated might be a gross understatement because they operated this as a actual “enterprise”
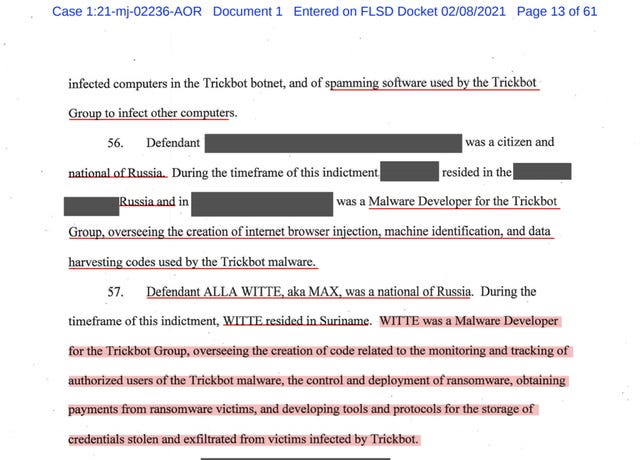
…Defendant ALLA WITTE, aka MAX, was a national of Russia. During the timeframe of this indictment, WITTE resided in Suriname. WITTE was a Malware Developer for the Trickbot Group…
This paragraph alone tells you the level of detail, organization and self discipline to carry on this campaign for years…largely undetected hence my phrase (imma gonna copyright or trademark it) CYBER-Darwinism - they kept breaking the malware to re-write code to make it largely undetectable. In some respects you kind of have to “respect” the TrickBot Group for their ingenuity, pushing to the Max and then out the otherside a perfectly calibrated malware.
…overseeing the creation of code related to the monitoring and tracking of authorized users of the Trickbot malware, the control and deployment of ransomware, obtaining payments from ransomware victims, and developing tools and protocols for the storage of credentials stolen and exfiltrated from victims infected by Trickbot.
And listen you don’t have to agree with my point of view but intellectually what the TrickBot Group did I kind of respect —to be clear I do not respect the crimes committed by the TrickBot Group —I respect their ingenuity and self discipline. I’d like to draw your attention to paragraphs 67 thru 69 of the indictment
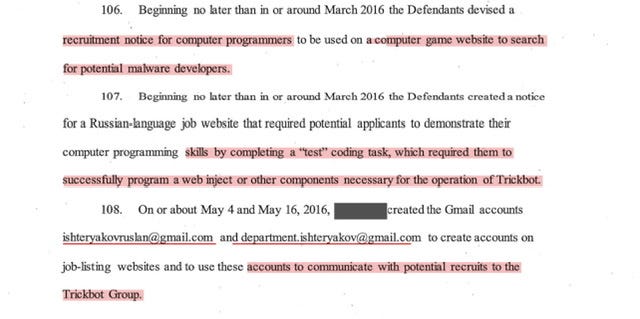
Setting aside the recruitment and posting of “jobs” mainly on a “Russian-based freelancing employment websites” it’s paragraph 68 and 69 that impress me. The Operators of the TrickBot Group actually “tested” potential employees before granting them access to the internal servers.
In paragraphs 70 thru 74 - the disclosure that TrickBot was designed to receive commands (remotely executed),and send information back to TrickBot Group’s HQ is kind of impressive - but paragraphs 71 thru 74 remind me of what the IRA1 did in 2016 and then again in 2018 and 2020 via Project Lakhta 23
As enumerated in Paragraph 74 & 75 - the Trickbot Group:
Defendants crafted the phishing emails to fraudulently entice a victim to open an attachment, such as a business invoice, or click on a hyperlink that falsely represented itself to be legitimate.
When the victim clicked on the attachment or hyperlink, the victim's computer was typically infected by Trickbot malware either embedded in the attachment or on a malicious domain connected to the hyperlink, without the victim's consent, knowledge or authorization.
Between the Keystroke monitoring/mirroring, Web Injections and TrickBot’s ability to sit (largely undetected) - the malware developers also found a viable work around to the “multi-factor authentication… by fmancial institutions to protect their clients”. Trickbot also allowed for monitoring of internet activity of infected computers. This allowed the defendants to capture “confidential information” but the following
“…and contacted the victims, posing as bank security personneL to interact with victims and employees of victim businesses to deceive them into providing the Defendants with their multi-factor authentication codes”
Did someone say Money Mules?
Again the TrickBot Group used incredibly sophisticated tools to evade detection for years.
used stolen credit cards to pay for servers, domains, VPNs
communicated via proxies for example C2 server, infected computers, commercial VPNs, and commercial proxies;
encrypted messaging server
regularly moving infrastructure and changing communication channels to avoid detection;
using U.S.-based and foreign money mules.
June 2015 through in or around April 2019, used a PayPalaccount under his control to purchase VPS and VPN services from numerous hosting and anonymization companies in the United States, United Kingdom, Lithuania, Canada, Italy, Russia, the Nether lands and elsewhere, initially for the Dyre group and then later for the Trickbot Group.
…need to acquire "fullz” …Medal of Valor
The level of deception and arrogance is astounding - the TrickBot Group [redacted] co-defendant stated;
'They should say thank-you to us that we are stealing money from the Americans we should get the Medal of Valor,"
As the indictment discloses: ishteryakovruslan@gmail(.)com and department.ishteryakov@gmail(.)com both emails used to post “job opportunities” and guess what? I was able to locate several of the jobs posted
March-June 2016 job posting https://programmersforum.ru/showthread.php?t=295565 also archived -also that job listing has two random YouTube videos but those videos are not “random” —in the indictment it details how the TrickBot Group migrated to a gaming channel and used YouTube to send messages
July 2019 second TrickBot Job posting https://forum.reverse4you.org/t/c/814 -also archived <—he listed his Jabber account and I am on the floor howling .
department.ishteryakov@gmail(.)com <—no dice but I really didn’t do a deep search.
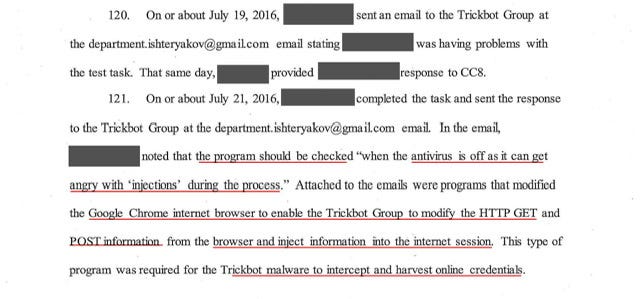
Read what I redlined —setting aside that the TrickBot Group used the proper capitalization and grammar and punctuation the notion that at every pace in development TrickBot Group essentially broke each code and then took steps to improve the code for the malware.
The sheer volume of modifications to the injection is mind blowing
“…updated the browser engine injection code for Google Chrome browser approximately 700 times, each update and modification consisting of a separate overt act.”
…Trickbot Group members modified and updated the above-described password harvesting module code approximately 150 times, each update and modification consisting of a separate overt act.
I mean this is just mind blowing because theorizing what TrickBot Group did is completely different than actually reading the details in the Indictment - for example;
They bought access to anti-virus software to find its weaknesses and then reworked the TrickBot code to evade numerous anti-virus software but the amount of data TrickBot scraped (some of which was automated) —but take a look at the number of files they uploaded…it’s just staggering
Between in or around March and October 2018, the Trickbot Group uploaded approximately over 43,000 ftles to VCM. Some of the ftles had names such as "HSBC_ deposit_ Confrrmation-0", "paypal", and ''Bankline _ Secure _Message."
Alla Witte’s over acts and BitCoin Wallets
October 2, 2018, WITTE gained access to the Trickbot development server.
On or about October 11, 2018, WITTE provided code used to manage and track authorized users of the Trickbot malware to the Trickbot Group. '
On or about December 17, 2018, WITTE created and provided to the Trickbot Group a video demonstrating how to use the Trickbot user tracking software.
"laravel faker bitcoin address,"
Defendant Witte also created a web page used to inform victims that their computer was encrypted with ransomware and to provide a Bitcoin address used by Trickbot Group to obtain a ransom payment. The web page included the following language:
''Your computer has been infected! Your documents, photos, databases and other important filed encrypted. To decrypt your ftled you need to buy our special software."
Moreover Witte also created “fake Bitcoin wallets” to test TrickBot’s functionality
WITTE provided code to this repository that showed an infected computer or 'bot' status in different colors based on the colors of a traffic light and allowed other Trickbot Group members to know when their co-conspirators were working on a particular infected machine
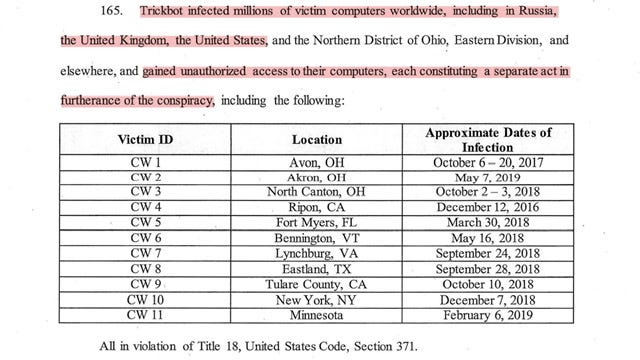
The Indictment also disclosed the geographical location of some victims and an approximate date of infection - see paragraph 165 of the indictment
Also see pages 38 thru 45 of the indictment for acts in furtherance of the conspiracy - its a partial list of transactions;
…purposes of executing th~ above-descnbed scheme and artifice, which scheme affected a fmancial institution, caused to be transmitted by means of wire communications in interstate and foreign commerce the writings, signs, signals, pictures and sounds
See pages 45 thru 48 of the indicted which proffers some of the Bank Fraud Acts committed…
“…knowing at the time that the pretenses, representations and promises would be and were false and fraudulent when made, did knowingly execute and attempt to execute the foregoing scheme and artifice by gaining access to online bank accounts and causing, and attempting to cause, the transfer of funds, with each access, transfer and attempted transfer being a separate count…
And if you’ve made it thus far into the article here’s your reward - copy of a highlighted and annotated (newly) unsealed indictment can be found on my public drive or you can pull down a copy from the DOJ-OPA link
And your extra gift for reading this really long article - is this video - I pulled down both of her YouTube videos in case they magically disappear and you can access those videos and the indictment Alla Witte-TrickBot-Public-Folder
So I think you are now sufficiently debrief on Alla Witte’ s indictment and have a better understanding why some of us were like TrickBot is gnarly AF.
-Filey
February 2018 - DOJ-OPA Grand Jury Indicts Thirteen Russian Individuals and Three Russian Companies for Scheme to Interfere in the United States Political System - indictment https://www.justice.gov/opa/press-release/file/1035562/download
October 2018 - DOJ-OPA Russian national Elena Alekseevna Khusyaynova
Khusyaynova, 44, of St. Petersburg, Russia, served as the chief accountant of “Project Lakhta,” a Russian umbrella effort funded by Russian oligarch Yevgeniy Viktorovich Prigozhin and two companies he controls, Concord Management and Consulting LLC, and Concord Catering. Project Lakhta includes multiple components, some involving domestic audiences within the Russian Federation and others targeting foreign audiences in the United States, members of the European Union, and Ukraine, among others.
Khusyaynova Criminal Complaint https://www.justice.gov/opa/press-release/file/1102316/download
September 2020 - DOJ-OPA Russian Project Lakhta Member Charged with Wire Fraud Conspiracy; https://www.justice.gov/opa/press-release/file/1315491/download
Artem Mikhaylovich Lifshits, 27, of St. Petersburg, Russia, serves as a manager in “Project Lakhta,” a Russia-based effort to engage in political and electoral interference operations. Since at least May 2014, Project Lakhta’s stated goal in the United States has been to disrupt the democratic process and spread distrust towards candidates for political office and the political system in genera



















Thank you Filey. Your attention to detail blows my mind and I only understand half of what I’m reading. These are sophisticated operators and DOJ is doing a bang up job because we’re being attacked on so many fronts.
Your research never ceases to amaze me, especially with the hysterical commentary. Qanon for the left🤣
PS your YouTube video is fabulous. The look on LB's face is priceless as she listens to crazy town. Thank you ☺️