Paying a ransom is a very very bad idea. Nexus to OFAC, Sanctions,
Colonial Pipeline $4.4M but lesser known. CNA Financial Corporation paid $40,000,000.00 in ransom - OFAC Oct 2020 Nat Sec & Nexus CNA
May 12 - Our critical infrastructure is seriously at risk. Ask Colonial Pipeline what their MTTR is......we are now entering day 6+ of the Colonial Pipeline Ransomeware attack. For years cyber-sec experts have repeatedly sounded the alarms & the need to harden our Critical Infrastructure continues
May 13 - Colonial Pipeline entering day 7 of the sophisticated cyber attack - restart in progress - updated 5/13/2021 Biden White House signs an Executive Order - Improving the Nation’s Cybersecurity
CloP exfiltration extortion, pay or data gets leaked
According to CoveWare 1 recently published their quarterly report.
Q1 of 2021 average ransom payment of $220,298.00 versus Q4 of 2020 average ransom payment of $154,108.00 — which equates to a 43% increase
Q1 of 2021 median ransom payment $78,398.00 versus Q4 of 2020 median ransom payment $49,450.00 —which equates to a 58% increase.
CoveWare also highlights, in Q1 of 2021 the data hauls were higher but the threat actor group was significantly lower. One exception and possibly important link—CloP was “extremely active… during Q1 of 2021 —threat actors deploying CloP seemed to targeted and impact …large victims and the hallmark is a demand of high ransoms
CloP exploited two zero day vulnerabilities which made remote code execution within unpatched Accellion FTA instances possible. Arguably this is likely the most sophisticated and targeted exploitation of a single software appliance. The level of precision was used by a handful of enterprises. The CloP group may have purchased the exploit used in the initial stages of the attack, for the purpose of exclusive use.
October 2020 ransomware gang going by the name of "CloP" has breached the company's internal network on Saturday, October 3, encrypted files, and asked for more than $20 million to provide the decryption key.
February 2021 Accellion was made aware of a P0 vulnerability in its legacy File Transfer Appliance (FTA) software. Accellion FTA is a 20 year old product that specializes in large file transfers.
CISA’s February 2021 -Releases Joint Cybersecurity Advisory on Exploitation of Accellion File Transfer Appliance
Now that you have a decent, albeit an abbreviated and condensed primer —let’s discuss what occurred on June 3, 2021. As is my standard practice I will provide you with links to the original documents. But fair warning the article is granular in detail and I ping-pong between private sector findings, legislative oversight and enforcement…
Colonial Pipeline
paid $4,400,000.00 ransom… House Oversight Committee June 3, 2021 Letter to Colonial Pipeline Company, CEO - Joseph Blount - requesting documentation, communiques, cryptocurrency used to pay the $4.4M ransom and explanation of the “worthless” de-encryption key DarkSide sent upon receiving the ransom
….After the ransomware attack, the FBI identified the hacking group Darkside, believed to be based in Russia or Eastern Europe, as being responsible for the attack. On May13, news reports indicated that Colonial Pipeline had paid nearly $5 million in ransom to Darkside.
Intentionally withholding info from Congress
Here’s the thing lying —misleading but lying by omission to Congress, that is not a position any Company or CEO wants to be in. Colonial Pipeline met with Congress. And at no time did Colonial ever disclose that a ransom would be paid —more precisely had been paid. Lawmakers found out after Colonial Pipeline’s CEO provided an in-depth interview to the Wall Street Jounal…
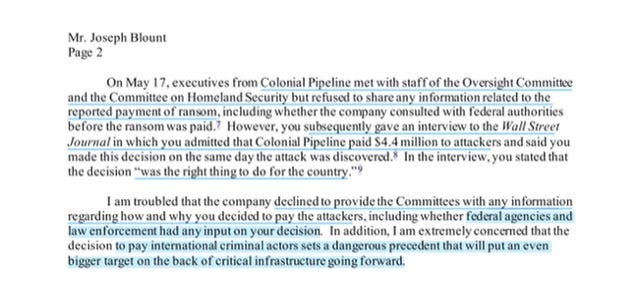
May 17, executives from Colonial Pipeline met with staff of the Oversight Committee and the Committee on Homeland Security but refused to share any information related to the reported payment of ransom, including whether the company consulted with federal authorities before the ransom was paid. However, you subsequently gave an interview to the Wall Street Journal in which you admitted that Colonial Pipeline paid $4.4 million to attackers and said you made this decision on the same day the attack was discovered. In the interview, you stated that the decision
“was the right thing to do for the country.”
Colonial Pipeline has until June 17th to produce
Spoiler Colonial Pipeline paid the ransom but the de-encryption key DarkSide provided them was absolutely worthless and it’s equivalent to Colonial Pipeline throwing bags of cash into the incinerator. Moreover this kind of duplicitous action sets a very and I mean very dangerous precedence.
Conversely it is possible (note I’m not saying that as a fact) that perhaps Fed Law Enforcement and Colonial Pipeline may have anticipated and “sniffers” on the Bitcoin, the wallet receiving the ransom. Again I do not have any documents to substantiate my assertion— so it’s reasonable to be skeptical or even disagree with me. But logic, commonsense and deductive reasoning makes me think there’s a high probability that my “educated guess” might be right.
All documents and communications relating to the discovery of the May 7, 2021, ransomware attack;
All documents and communications relating to the ransom, including but not limited to the following:
any communications with the attackers about the ransom payment or the receipt of the decryption key;
any consultation or communications with outside experts or federal agencies regarding the identity of the cybercriminals and whether to pay ransom;
the purchase and transfer of Bitcoin and other cryptocurrencies and any intermediaries used in such transactions;
any sanctions screening regarding the ransom payment; and
any internal communications among employees of Colonial Pipeline regarding the ransom payment; and
All documents and communications relating to the decryption tool provided by the attackers, including the performance of the decryption tool and the company’s decision to use its own tools to bring the pipelines back online.
I can tell you that I think the House Oversight Committee’s request seems overly broad and possibly unreasonable. I’m not sure what if any obligation Colonial Pipeline has to produce the records requested, short of a subpoena. I think that had the letter come from the chairs of;
House Permanent Select Committee on Intelligence, and/or
House Homeland Security, and/or
House Energy and Commerce Committee
It wouldn’t give Colonial Pipeline an “out” because I would expect Colonial Pipeline’s General Counsel will likely put up a pretty robust fight due to the inherent confidentiality baked into the documents, records and communiques the OverSight Committee —especially in the absence of any promises to keep that internal info “privilege” —if the other House Committees signed on to the letter than Colonial Pipeline would likely be more amenable to the request
CNA Financial Corporation
Hey remember that PITA Twitter account that would randomly do threads about various cyber attacks…and in early 2019 would be a total PITA about “cyberattack insurance policy” and then dared to asked the question; what if the insurance company ends up being a target?
At the time (pre-covid) this discussion and spirited debate came up at a Cyber & Law symposium that I attended. It was truly like looking into the “looking glass” and then creating a checklist simply to ensure you are prepared for an attack.
CNA Finical Corporation cyber attack was relatively low key, it wasn’t until early May 2021 did CNA share the totality of the attack. And yes CNA is one of the leading insurance companies that offer cyber-attack insurance policies. CNA publicly announced the totality of the massive cyberattack (like 5 weeks after the fact);
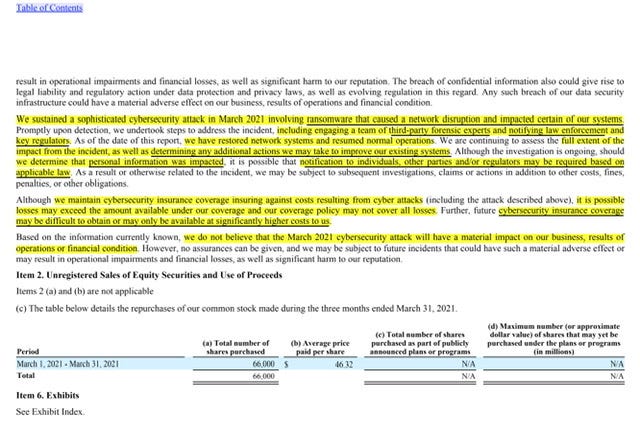
“On March 21, 2021, as previously shared, we detected the ransomware and took immediate action by proactively disconnecting our systems from our network to contain the threat and prevent additional systems from being affected," CNA published on Wednesday May 12, 2021 - this is the CNA 2 page press release and that’s when, nearly five weeks later -CNA came clean and shared the totality of the cyber attack - below are the various updates
PROGRESS UPDATE
May 12, 2021: Security Incident Update -scope of impacted data in the incident, as well as the servers on which the data resided. We are reviewing the impacted data to determine the contents using both technology and a manual review. We will continue to work quickly and diligently so that we may assess our legal obligations, including any notification obligations to policyholders and impacted individuals.
April 12, 2021: Security Incident Update - confirmed that the incident has been contained, there is no evidence that the Threat Actor has been active in the CNA environment since the ransomware event, and endpoint detection and monitoring tools have been deployed throughout the environment.
Deployed endpoint detection and monitoring tools throughout the environment and restored email connectivity for CNA employees through Microsoft Office 365;
Restored VPN access for CNA employees, which will provide additional connectivity to applications and other systems as they are safely restored; and
Brought our corporate website and CNAsurety.com back online.
April 1, 2021: Security Incident Update - following a phased approach – containment, remediation, restoration, a forensic examination, and a thorough data review process. We have also activated our business continuity plans to ensure our stakeholders are supported throughout our ongoing investigation
March 23, 2021: Security Incident Update - CNA determined that it sustained a sophisticated cybersecurity attack. The attack caused a network disruption and impacted certain CNA systems.
CNA 2 months to fully restore systems
To date I do not believe the cyber-actors that launched a crippling cyber attack on CNA have been identified and CNA hasn’t been fully forthcoming but as you know if you know where/what/when to go look for facts you can actually find them but first let’s briefly dissect the House OverSight Committee June 3, 2021 Letter to CNA Financial Corporation, CEO Dino Robusto
...one of the largest insurance companies in the United States and a major cyber insurance provider— encrypted 15,000 company devices and led to widespread network disruption. The attackers reportedly accessed and stole company data, though the extent of the theft and the identity of the attackers have not been reported in detail. CNA’s systems were not fully restored until May12, nearly two months after the initial attack.
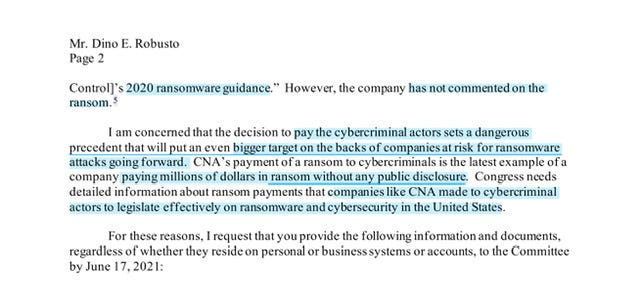
Oh wait did CNA’s spokesperson really lay down the OFAC 2020 Guidelines…why yes, yes they did and it’s a non sequitur remark because if that were even remotely true that CNA would have never paid the $40,000,000.00 ransom
I’m calling BS on your OFAC 2020 GUIDELINES
Because those of us who are actually in DC and actually know how DC works - it means we can predict what’s going to happen next (not random theories) —Congress will investigate, CNA will capitulate and equivocate, and then Congress will reach out to OFAC, FINCEN, DOJ, FBI, FDIC, SEC, DHS
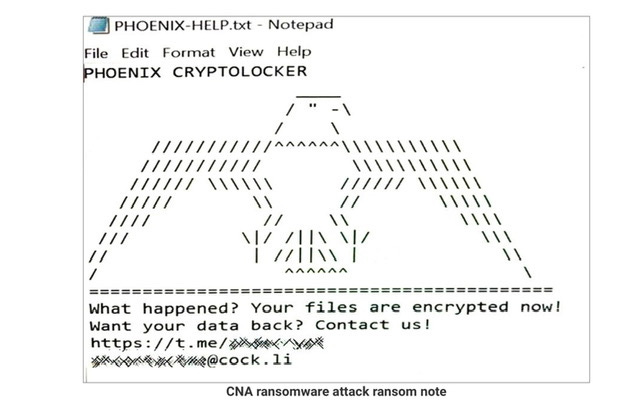
And then I’m pretty sure we are going to find out that CNA Cowboy’d the ransom payment. Failed to consult with Treasury or DOJ. My educated guess is in 20 to 33 months the $40,000,000.00 ransom CNA paid will likely be linked to a “nexus” of cyber criminals operating at the behest of Russia but likely based in Romania or Ukraine —cough “Phoenix CryptoLocker,' see March report from Bleeping Computer. But speaking off the cuff researchers tend to agree that Phoenix is likely a progeny of WastedLocke, cough —> EvilCorp —Cough—>Dridex Malware
FinCEN Guidance, FIN-2020-A00X, “Advisory on Ransomware and the Use of the Financial System to Facilitate Ransom Payments,” October 1, 2020, for applicable anti-money laundering obligations related to financial institutions in the ransomware context.
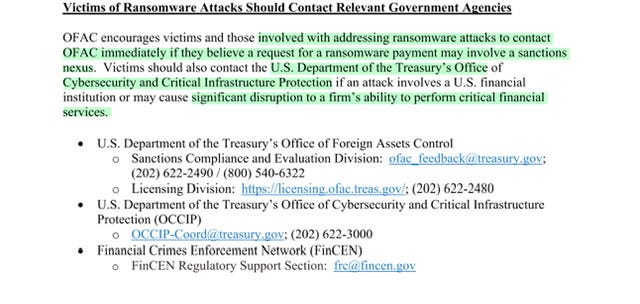
U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) is issuing an advisory to alert companies that engage with victims of ransomware attacks of the potential sanctions risks for facilitating ransomware payments.
Companies that facilitate ransomware payments to cyber actors on behalf of victims, including financial institutions, cyber insurance firms, and companies involved in digital forensics and incident response, not only encourage future ransomware payment demands but also may risk violating OFAC regulations
….could be used to fund activities adverse to the national security and foreign policy objectives of the United States. Ransomware payments may also embolden cyber actors to engage in future attacks. In addition, paying a ransom to cyber actors does not guarantee that the victim will regain access to its stolen data.
If my preliminary (and amateur) research is correct than “book it” because the probability that CNA’s $40,000,000.00 ransom might have violated the International Emergency Economic Powers Act and/or the Trading with the EnemyAct
I mean CNA Financial Corporation if you want Congress to believe your (demonstrably false) statement
“followed all laws, regulations, and published guidance, including [Office of Foreign Asset Control]’s 2020 ransomware guidance.”
then why pray tell is U.S. Department of the Treasury’s Office of Cybersecurity and Critical Infrastructure Protection learning about your $40,000,000.00 ransom payment when the rest of the world found out?
CNA I have questions about your recent SEC filing too
Because I’m a stickler for providing my readers with original documents
CNA-SEC-Investor-Relations because even though I embedded CNA’s cyber updates, you’ll note it took over five weeks for CNA to fully (I genuinely do not believe they’ve disclosed everything) be transparent— I tend to like reading SEC filings. For Example CNA’s recent quarterly report -which was filed in early May 2021, which is important
…which may be enhanced following completion of work relating to the sophisticated cyber incident sustained by the Company in March 2021 as discussed in Risk Factors, Part II, Item 1A of this report…
Potential exposures resulting from the March 2021 cybersecurity attack, described in the following risk factor, as well as any future incidents may include substantially increased compliance costs and required computer system upgrades and security-related investments. If our business continuity plans or system security do not sufficiently address these risks, they could have a material adverse effect onour business, results of operations and financial condition.
A significant breach of our data security infrastructure may result from actions by our employees, vendors, third-party administrators, or unknown third parties or through cyber attacks. The risk of a breach can exist whether software services are in our data centers or we use cloud-based software services.
Such a breach could affect our data framework or cause a failure to protect the personal information of our customers, claimants or employees, or sensitive and confidential information regarding our business and may
The thing is CNA is a public company and statutorily they are required to disclose
“attacks” that might have an adverse impact of the fiduciary health of the company. This isn’t optional and the SEC has enforcement authority2 and failure to comply with the Securities Exchange Act - could result in significant fines - just ask ALTABA INC., f/d/b/a YAHOO! INC. about their 2018 shellacking 3
…we have restored network systems and resumed normal operations. We are continuing to assess the full extent of the impact from the incident, as well as determining any additional actions we may take to improve our existing systems.
Although the investigation is ongoing, should we determine that personal information was impacted, it is possible that notification to individuals, other parties and/or regulators may be required based on applicable law
So the rather circuitous route to arrive at the sum total; cyber security is not a set it and forget it endeavor - if you’re “reacting” to an intrusion/attack then your cyber security has more holes than Swiss cheese. But if you as a researcher or otherwise curious individual want to know how much a public company is down playing the attack, go read their SEC filings…4 because that’s where the factual “good stuff” can be found.
In short paying the ransom is about the dumbest thing a company can do …there I said it in plain language and I’m not at all sorry. -Filey
Covewave Q1 of 2021 Ransomware Attack Vectors Shift as New Software Vulnerability Exploits Abound - pay attention the change in vectors - that’s pretty important https://www.coveware.com/blog/ransomware-attack-vectors-shift-as-new-software-vulnerability-exploits-abound#exfil — “The most common software vulnerabilities exploited during Q1 involved VPN appliances, such at Fortinet and Pulse Secure. Several RaaS services leveraged these VPN vulnerabilities during Q1. Again, it is likely that the actual RaaS operators and affiliates were NOT the party that achieved network access via these vulnerabilities, but rather specialist actors that harvest network credentials and are specifically trained to mass scan for vulnerable IP addresses”
In 2011 SEC’s Division of Corporation Finance issued guidance companies’ disclosure obligations relating to cybersecurity risks and cyber incidents. Failure to disclose -Disclosure by Public Companies Regarding Cybersecurity Risks and Cyber Incidents..
…designed to elicit disclosure of timely, comprehensive, and accurate information about risks and events that a reasonable investor would consider important to an investment decision..
May 2011 letter from Sen Rockefeller to the SEC;
asking the Commission to clarify corporate disclosure requirements for cybersecurity-related incidents, quoting statistics from a 2009 survey concluding that 38 percent of Fortune 500 companies had made a significant oversight in their public filings by not discussing privacy and data security events
https://www.commerce.senate.gov/services/files/4ceb6c11-b613-4e21-92c7-a8e1dd5a707e - last visited June 3, 2021
April 2018 - SEC first ever enforcement of a company failing to disclose a cyber intrusion/attack;
This matter concerns material misstatements and omissions by Yahoo, one of the world’s largest Internet media companies, regarding a 2014 data breach affecting more than 500 million of its user accounts
https://www.sec.gov/litigation/admin/2018/33-10485.pdf - last visited June 3, 2021
SEC 2018 “report” - Report of Investigation Pursuant to Section 21(a) of the Securities Exchange Act of 1934 - SEC.gov - also see Jan 2020 Securities and Exchange Commission Commission's Office of Compliance Inspections and Examinations (OCIE) today issued examination observationsrelated to cybersecurity and operational resiliency practices taken by market participants.











JFC... all the crimes committed under Trump’s administration.. great piece. Shared. Xxoo