House Committee Hearing - Stopping Digital Thieves: The Growing Threat of Ransomware
Hearing will begin live streaming at 10:30AM on July 20, 2021 - video link embedded with the witness panel written testimony
Committee on Energy and Commerce - Subcommittee on Oversight and Investigations
“Stopping Digital Thieves: The Growing Threat of Ransomware.”
Cyber Security - Biden Administration Background
Last week I walked you through the NEW single source website StopRansomware.gov and I’ve previously written extensively on how the Biden Administration.
On May 12th then (whilst at our beach home getting it prepped for high season) walked you through the paces of what constitutes critical infrastructure and what the Administration and what Congress would do. I then further expounded on May 13, where again I walked you through the Biden Administration’s May 12th Executive Order (yes it buried deep in that long article but nonetheless it’s there) -honestly I’m not going to regurgitate the dozens of previous articles, found here, here (my Hladyr -FIN-7 reach back to September 2019 might have been me at the top of my I said what I said - I don’t know why that April article was overlooked) and here - and lastly let’s not forget yesterday’s major cyber announcement (with the White House Statement and actions embedded) where America stood with our NATO partners and other Allies to speak globally to China that you’re malicious cybercrime needs to stop or there will be a pretty steep price to pay.
July 20, 2021 House Subcommittee - witness panel;
Kemba Walden, Assistant General Counsel Microsoft Corporation, written testimony - check out pages 3 thru 8
Robert M. Lee, Chief Executive Officer Dragos - written testimony I personally found pages 3 thru 5 highly interesting… and yes ICYMI Binance Announcement was/is a BFD, don’t know why this article was overlooked because the take down of an entire cryptocurrency eco system is a huge deal. But again it’s not my job to force you to read what I write.
Christian Dameff, M.D., M.S. Assistant Professor of Emergency Medicine, Biomedical Informatics, and Computer Science (Affiliate) University of California San Diego Medical Director of Cybersecurity and UC San Diego Health - written testimony - I found pages 2-3 intriguing - this is pretty important testimony because the focus is on the impact within the Healthcare Industry. If you’ll recall back in early June 2021 I walked you through Vikas Singla & the insider threat he posed - if I told you how printers are used as a way to breach a network - you probably wouldn’t believe me, until you read the indictment…
Charles Carmakal Senior Vice President and Chief Technical Officer, FireEye-Mandiant - written testimony- I highly recommend you read pages 2 thru 4 - full disclosure I’m genuinely a fan of FireEye so it’s okay if you are skeptical of my adulation. For years the “theory” that cyber criminal gangs would use task assignments tended to make people laugh at my questions - as it turns out maybe instead of laughing the crew should maybe think about the substance of the question…
Philip Reiner, Chief Executive Officer Institute for Security and Technology - written testimony- if you want to fully understand the various complexities I would highly recommend you read his written testimony - especially page 3…
And pages 4-5 which reads in part (the RTF report cited in the written testimony is embedded below under the additional resource material)
Ransomware Task Force process resulted in 48 recommended actions within four focus areas. We debated the most effective framework and determined those four focus areas to be the most salient as part of a comprehensive approach
And as always below are a few Resources that I culled for your future reading pleasure… because after all sharing is caring and I like to “think” I care…
Institute for Security and Technology - RTF Report:
I highly recommend you take the time to read this thoroughly vetted and articulated report, particularly the key recommendations;
Combatting Ransomware -A Comprehensive Framework for Action: Key Recommendations from the Ransomware Task Force - it’s an 81 page report that was published in April of 2021 and I highly recommend you read it.
Ransomware is not just financial extortion; it is a crime that transcends business, government, academic, and geographic boundaries. It has disproportionately impacted the healthcare industry during the COVID pandemic, and has shut down schools, hospitals, police stations, city governments, and U.S. military facilities. It is also a crime that funnels both private funds and tax dollars toward global criminal organizations. The proceeds stolen from victims may be financing illicit activities ranging from human trafficking to the development and proliferation of weapons of mass destruction.
Tackling ransomware will not be easy; there is no silver bullet for solving this challenge. Most ransomware criminals are based in nation-states that are unwilling or unable to prosecute this cybercrime, and because ransoms are paid through cryptocurrency, they are difficult to trace. This global challenge demands an “all hands on deck” approach, with support from the highest levels of government.
Office of Director of National Intelligence
See their April 20, 2021 Annual Threat Assessment - last accessed July 19, 2021 & I hard coded that link to automatic open up to page 6 - where the ODNI discusses the ongoing and persistent cyber crimes China continues to commit
“China increasingly is a near-peer competitor, challenging the United States in multiple arenas—especially economically, militarily, and technologically—and is pushing to change global norms”
National Security Agency | Cybersecurity Advisory October 2020
Chinese State-Sponsored Actors Exploit Publicly Known Vulnerabilities (again originally published in October 2020) - which reads in part:
One of the greatest threats to U.S. National Security Systems (NSS), the U.S. Defense Industrial Base (DIB), and Department of Defense (DoD) information networks is Chinese state-sponsored malicious cyber activity. These networks often undergo a full array of tactics and techniques used by Chinese state-sponsored cyber actors to exploit computer networks of interest that hold sensitive intellectual property, economic, political, and military information. Since these techniques include exploitation of publicly known vulnerabilities, it is critical that network defenders prioritize patching and mitigation efforts.
Federal Bureau of Investigation - China Cyber Threat
July 7, 2020 FBI Director Wray and the threat China poses- the full transcript of Director Wray’s comments can be found via the following FBI Link
FBI The Nevernight Connection - China and Social Media
This film—inspired by the case of former CIA officer Kevin Mallory—details the fictional account of a former U.S. Intelligence Community official who was targeted by China via a fake profile on a professional networking site and recruited to turn over classified information before being arrested. Through this film, The FBI and the National Counterintelligence and Security Center seek to raise awareness of this issue and help individuals in the private sector, academic and research communities, and other U.S. government agencies guard against this threat.
Think before you link was a cooperative public awareness campaign launched by our FBI and UK partners see UK link https://www.cpni.gov.uk/security-campaigns/think-you-link
Originally released in September of 2019 - it was a public awareness campaign, which was (unfortunately) overshadowed by Trump and his daily antics. This ODNI Link/Press Release provides more details to the PSA campaign https://www.dni.gov/index.php/ncsc-newsroom/item/2145-nevernight-press-release
This is the FBI front facing PSA website-campaign https://www.fbi.gov/investigate/counterintelligence/the-china-threat/clearance-holders-targeted-on-social-media-nevernight-connection
China and other foreign governments are using professional networking social media sites to target people with U.S. government security clearances. Foreign intelligence services may use fake profiles, seemingly benign requests, the promise of lucrative payouts, and other tactics to try to gain non-public and classified information for their benefit. The FBI urges everyone—especially those who hold (or have held) security clearances—to be cautious when approached by individuals online regarding career opportunities.
NSA, CISA, and FBI detail Chinese State-Sponsored Actions, Mitigations -July 19, 2021
Which reads in part:
The National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI) released a Cybersecurity Advisory, Chinese State-Sponsored Cyber Operations: Observed TTPs. 1 2This advisory describes over 50 tactics, techniques, and procedures (TTPs) Chinese state-sponsored cyber actors used when targeting U.S. and allied networks, and details mitigations.
FireEye - APT41 - Double Dragon Report:
Double Dragon -APT41, a dual espionage and cyber crime operation -for the record the July 19th Joint FBI & DHS &WH and NATO announcement primarily deal with APT40 - but if you understand cyber security then you should know APT41 et seq is something to absolutely keep your eye on - otherwise do you so at your own cyber peril, at least that’s what I (may have tersely) said to a client today who was being an obstinate PITA…
FireEye Threat Intelligence assesses with high confidence that APT41 is a Chinese state-sponsored espionage group that is also conducting financially motivated activity for personal gain.
APT41 espionage operations against the healthcare, high-tech, and telecommunications sectors include establishing and maintaining strategic access, and through mid-2015, the theft of intellectual property.
The group's operations against higher education, travel services, and news/media firms provide some indication that the group also tracks individuals and conducts surveillance.
Learning to access video game production environments enabled APT41 to develop the tactics, techniques, and procedures (TTPs) that were later leveraged against software companies to inject malicious code into software updates.
Pay attention this is pretty damn important
Like other Chinese espionage operators, APT41 targets industries in a manner generally aligned with China's Five-Year economic development plans. However, some campaigns attributed to APT41 indicate that the group is also deployed to gather intelligence ahead of imminent events, such as mergers and acquisitions (M&A) and political events. Directly targeted verticals include:
Also important Double Dragon’s duality
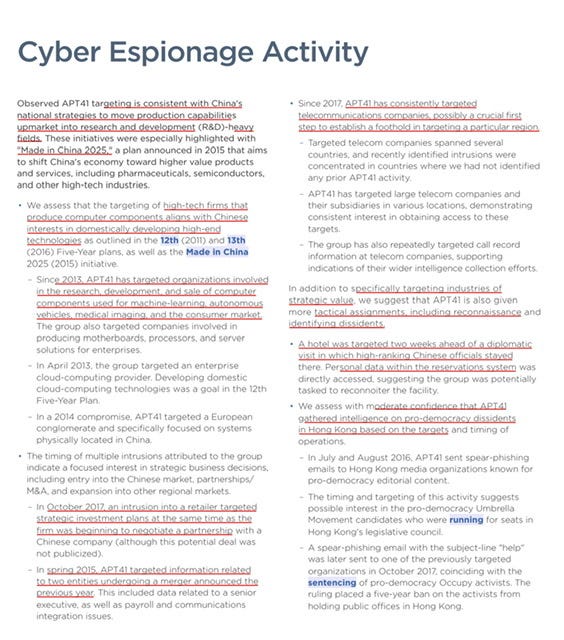
Since 2017, APT41 has consistently targeted telecommunications companies, possibly a crucial first step to establish a foothold in targeting a particular region.
– Targeted telecom companies spanned several countries, and recently identified intrusions were concentrated in countries where we had not identified any prior APT41 activity.
– APT41 has targeted large telecom companies and their subsidiaries in various locations, demonstrating consistent interest in obtaining access to these targets.
– The group has also repeatedly targeted call record information at telecom companies, supporting indications of their wider intelligence collection efforts
In addition to specifically targeting industries of strategic value, we suggest that APT41 is also given more tactical assignments, including reconnaissance and identifying dissidents.
Social Media Accounts I recommend you follow —for the love of my soul I beseech you to stop listening to faux intelligence “people” who’s bad legal take are no longer funny. As they are now dripping in anti-semitism, anti-asian (actual hate) and the classic narcissistic misogyny - and you amplifying their self aggrandizing bullshit disinformation and misinformation means you’re amplifying the QANON-for-the-Left aka Alex-Jones-of-the-left.
I don’t need to name names, you know the people I’m talking about… below are a few social media accounts I would absolutely and unreservedly follow. Also rhetorical question; if I’m purportedly IP banned from Twitter how can I still access it -weird…
NSA Cyber


U.S. Army Cyber Command


US Cyber Command


CISA


At any rate if you can I’d watch today’s hearing but unfortunately I am slammed at work but I’ll likely publish a follow up article to highlight portions of today’s hearing that I think are important.
In my best mom voice - Have a great day, make smart life choices and if you’re not already vaccinated https://www.vaccines.gov the sooner you get vaccinated the sooner you can get back to normal life. Not a sermon - just a thought because occasionally I actually do care
-Filey
that’s a 31 page report and I highly recommend you read the GitHub JSON and Appendices because that’s where the “juice is” https://media.defense.gov/2021/Jul/19/2002805003/-1/-1/1/CSA_CHINESE_STATE-SPONSORED_CYBER_TTPS.PDF - last accessed July 19, 2021
NSA Funds Development, Release of D3FEND - released June 22, 2021 https://www.nsa.gov/DesktopModules/ArticleCS/Print.aspx?PortalId=70&ModuleId=10851&Article=2665993 - last accessed July 19, 2021 - NSA and MITRE encourage the cybersecurity community to promote the adoption of this vocabulary by cybersecurity professionals across government, industry, and academia. Cybersecurity professionals can provide comments to improve and add to the framework by contacting the MITRE D3FEND team at https://d3fend.mitre.org.













aweee. But this is terrifying? Do you think that russia's or china's infiltration might be used to make us think the other or a different country has attacked us - just to get us into war?