Trickbot Vladimir Dunaev extradition.
“Russian National Extradited to United States to Face Charges for Alleged Role in Cybercriminal Organization..”
Brief Primer re TrickBot and why some of us were like “FINALLY” Alla Witte…
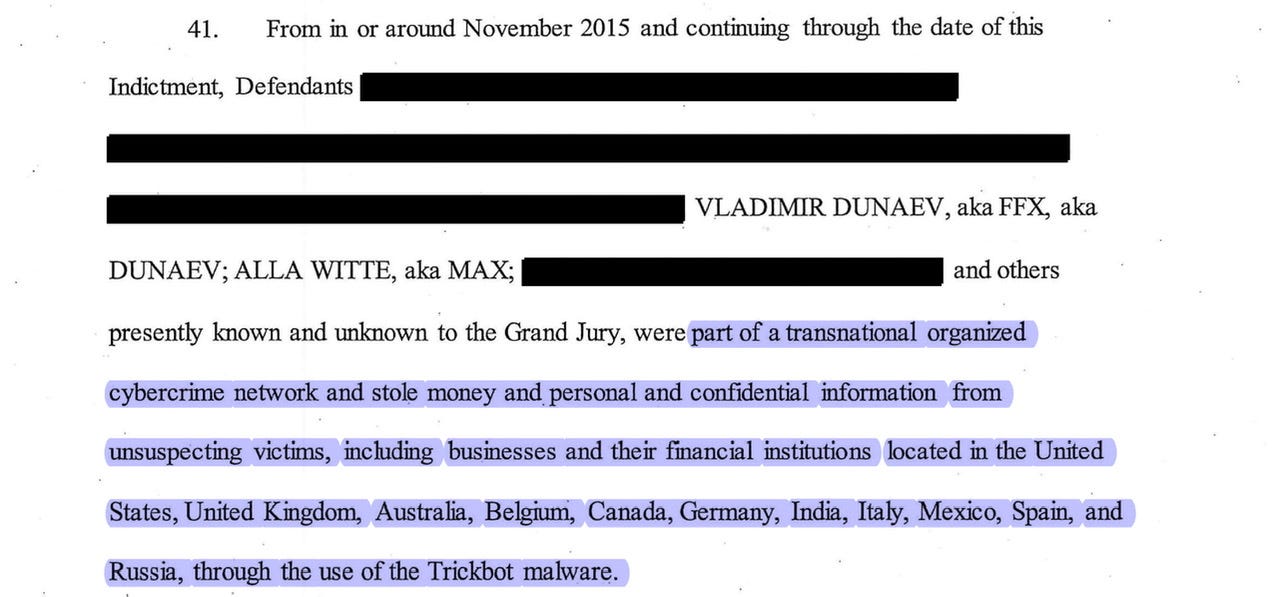
One of the very first items I noted in the June 2021 article happened to be the redacted boxes and that there are at least three and possible up to 5 other co-conspirators. On October 28, 2021 we learned — I believe for the very first time the name of a co-conspirator(s)…
…participants in a criminal scheme to defraud, and were located in or around Russia, Belarus, Ukraine and Suriname.
The June 2021 unsealed indictment —again I’ve previously dissected the indictment, as noted in this previous publication. Although it is kind of affirming that previous observations are suddenly “proof in concept” —and in all technicality the indictment disclosed over 15 coconspirators.
Vladimir Dunaev aka FFX aka DUNAEV
On September 1, 2021 - KBS was first to report the arrest of Vladimir Dunaev —having been “stranded” in South Korea for over a year due to COVID-19
Again according to the DOJ-OPA Release, on October 20, 2021 Vladimir Dunaev was extradited from the Republic of Korea (see MLAT) back to America, presumably in the Eastern District of Ohio —Yes you are reading that correctly. Hence why MLATs are crucial. Defendant Dunaev is charged (see DOJ-OPA Release) with;
conspiracy to commit computer fraud and aggravated identity theft,
conspiracy to commit wire and bank fraud, conspiracy to commit money laundering, and multiple counts of wire fraud, bank fraud, and aggravated identity theft…
If sentenced to the maximum allowable -the defendant is facing sixty years in prison… but something in my gut says Defendant Dunaev might be amenable to hammering out a plea agreement.
As allege in the indictment — between November 2015, and continuing through August 2020, Dunaev and other co-conspirators stole money, confidential information, and damaged computer systems from unsuspecting victims, including individuals, financial institutions, school districts, utility companies, government entities, and other private businesses. See paragraphs 28 thru 39 of “cooperating witnesses”
…defendants allegedly used a network of co-conspirators and freelance computer programmers, known as the Trickbot Group, to create, deploy, and manage the Trickbot malware, which infected millions of computers and computer systems worldwide.
And finally one burning question answered — whether or not Dunaev was recruited or who recommended him. He was recruited in May 2016 and passed several programming/hacks text. Dunaev is also alleged to have been one of the various co-conspirators, working as a malware developer for the Trickbot Group.
Dunaev allegedly performed a variety of developer functions in support of the Trickbot malware, including managing the malware’s execution, developing popular browser modifications and helping to conceal the malware from detection by security software.
..used these stolen login credentials and other personal information to gain access to online bank accounts, execute unauthorized electronic funds transfers and launder the money through U.S. and foreign beneficiary accounts.
…programs that modified the Google Chrome internet browser to enable the Trickbot Group to modify the HTTP GET and POST information from the browser and inject information into the internet session. This type of program was required for the Trickbot malware to intercept and harvest online credentials
targeted the Avon and Coventry schools both located in Northeast Ohio - in 2017, TrickBot hacked into Avon schools’ accounts, which managed to siphon-off over $471,000 in just a few hours. Coventry spent over $80,000 to rebuild their I-T-system after the trickbot attack
obtained online banking credentials to purloin more than $750,000 in wire transfers from an unidentified real-estate business in North Canton in 2018
What I do find intriguing about the recently unsealed indictment as to Defendant Vladimir Dunaev — he doesn’t appear part of the TrickBot Group development team. Whereas Alla Witte was on the development team. She also developed the code for the deployment and control of the threat. Witte then turned her coding skills to writing a code for payments and developed the tools and protocols used to store login credentials stolen by the malware from victims’ infrastructure…
…dismantling ransomware groups and disrupting the cybercriminal ecosystem…
“Trickbot attacked businesses and victims across the globe and infected millions of computers for theft and ransom, including networks of schools, banks, municipal governments, and companies in the health care, energy, and agriculture sectors,” said Deputy Attorney General Lisa O. Monaco.
“This is the second overseas Trickbot defendant arrested in recent months, making clear that, with our international partners, the Department of Justice can and will capture cyber criminals around the world. This is another success for the Department’s recently launched Ransomware and Digital Extortion Task Force in dismantling ransomware groups and disrupting the cybercriminal ecosystem that allows ransomware to exist and to threaten our critical infrastructure.”
Again via the DOJ-OPA Press Release and Indictment pulled directly from the DOJ. I’ve previously dissected the Indictment, all the way back to June 2021. Moreover a cursory review of this indictment, it reads largely reiterative of the redacted indictment from a few months ago, found here. Also I’ve stopped and started a SCOTUS article and TX-SB8 dozens of times. Mainly because I’m flummoxed by how far off the tracks we’ve become…If you’re inclined I would recommend rereading this June 2021 article because it will help you understand this case in a much broader standpoint









Help! I am really going to need Cliff Notes from you on the TX abortion case currently being argued before SCOTUS. Is Mark Hearron’s argument about “Clerks” valid? Seems weird. Thanks. Also, hope you are feeling better. 😊