Emotet Botnet Disrupted in International Cyber Operation -DOJ RADE and the cyber ecosystem -NOBELIUM
Emotet Malware Infected More than 1.6 Million Victim Computers and Caused Hundreds of Millions of Dollars in Damage Worldwide
Emotet Botnet -Tango Down
below is a brief video from ESET, it helps you understand why this botnet earned the moniker of the “most dangerous botnet” And to say the Emotet Botnet was a pervasive and pernicious botnet is an actual understatement.
In late January 2021 - Europol announced the “take down”
This operation was a sprawling collaborative effort between Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada and Ukraine, with international activity coordinated by Europol (PDF announcement) and Eurojust; and carried out under the current legal framework of the European Multidisciplinary Platform Against Criminal Threats (EMPACT).
When I say that we, the United States of America standing shoulder to shoulder with our Allies is something that genuinely makes me happy and thankful—Our Allies have (hopefully had, yes past tense) every reason to question “what the ___ you elected that lunatic and he’s systematically taking a sledgehammer to decades long Global partnerships” —hence why Trump’s deleterious and overt abuse of power concerning US aid that was (by law) appropriated to assist the decent folks in the Ukraine… here’s an actual example of Ukrainian Government Law Enforcement knocking down doors and ripping computers from the wall.
The Emotet Malware was delivered via Word Documents attached to an email or via a downloading file. Unsuspecting users were targeted by bad actors who weaponized documents such as shipping notices and information concerning COVID-19. Once a user opened the document, the user would be prompted to “enable macros”, where deeply embedded in the word document the “malicious code was hidden”
Originally identified in “the wild” circa 2014 Emotet was largely known as a “bank Trojan” but with a hybridization that had worm like traits & characteristics and enhanced capabilities. EMOTET soon became notorious for its polymorphic characteristics.
Meaning this Malware had the ability to change its code each time it was called upon or otherwise deployed. In simple terms this is hugely problematic for anti-virus software(s) which scan for known viruses. EMOTET’s ability to shape shift on-the-fly meant this malware had the consistent ability to evade anti-virus software, which scans for known codes.
Emotet infection caused damage to the school’s computers, including but not limited to the school’s network, which was disabled for approximately two weeks. In addition, the infection caused more than $1.4 million in losses, including but not limited to the cost of virus mitigation services and replacement computers. From 2017 to the present, there have been numerous other victims throughout North Carolina and the United States, to include computer networks of local, state, tribal, and federal governmental units, corporations, and networks related to critical infrastructure.
During the course of the investigation the FBI notified more than 20 U.S.-based hosting providers. Informing them that they were hosting more than 45 unique IP addresses that had been compromised. Furthermore the FBI Legal Attachés went on to notified authorities in more than 50 countries that hosting providers in their respective jurisdictions hosted hundreds of IP addresses that were compromised by Emotet.
Search Warrants
As with my standard practice and commitment to provide you with original sourced documents, authentic documents
Emotet search and seizure warrant
Emotet application and affidavit
On January 28, 2021 APPLICATION and Affidavit for Search Warrant
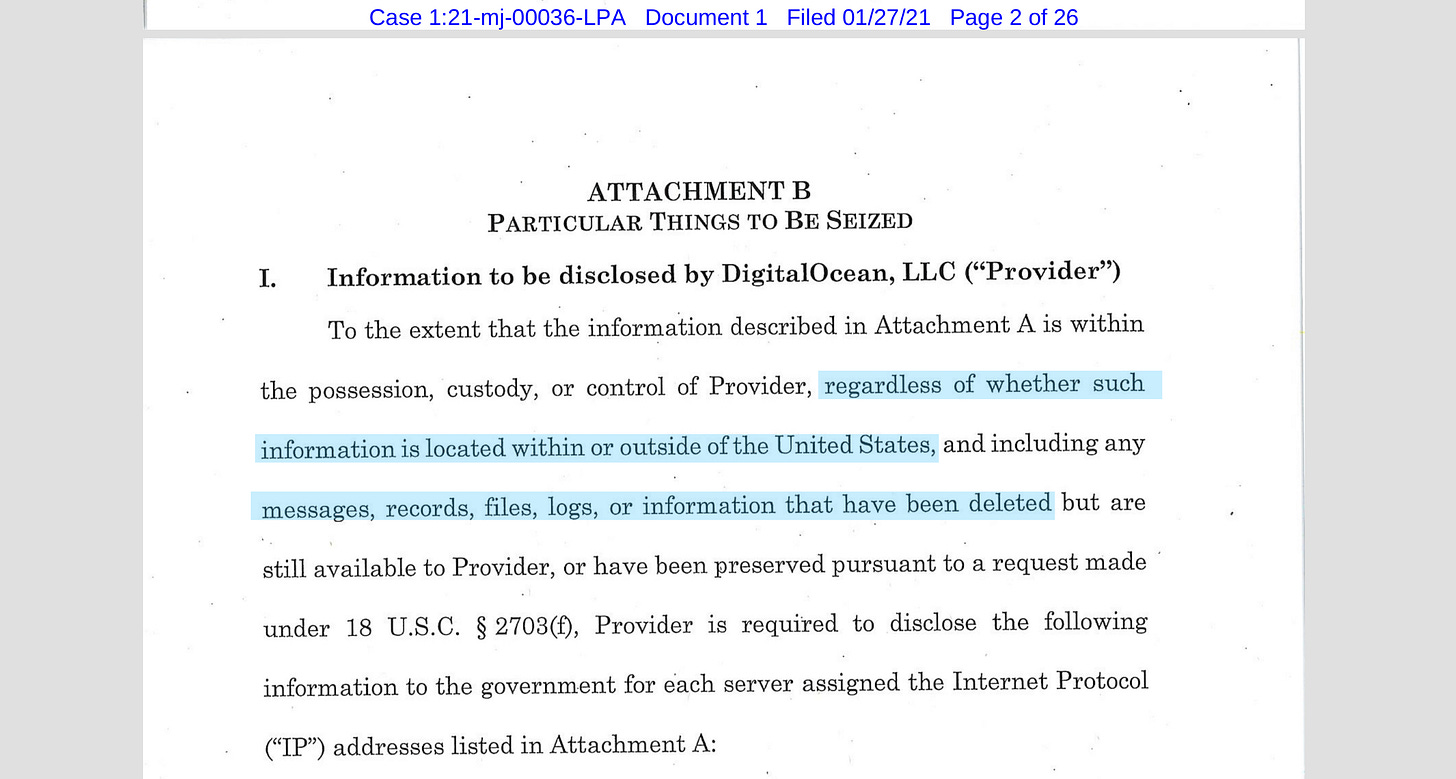
SEALED as to INFORMATION ASSOCIATED WITH THREE IP ADDRESSES THAT IS STORED AT PREMISES CONTROLLED BY DIGITALOCEAN, LLC. This search warrant was later unsealed, (see DOJ-OPA link for the 7 page search warrant) on page 2 you will note 3 IP addresses
In the Affidavit for the search and seizure warrant, you’ll note that a Judge granted law enforcement’s request for information outside the United States and production of documents (to include messages, records, files, logs and other information) “that may have been deleted”
“…Emotet infections have cost local, state, tribal, and territorial governments up to $1 million per incident to remediate. More information about the malware, including technical information for organizations about how to mitigate its effects, is available from CISA here: https://us-cert.cisa.gov/ncas/alerts/TA18-201A.
June 7, 2021 DOJ Press Conference
The seizure announced today was conducted as part of the Department’s recently launched Ransomware and Digital Extortion Task Force,1 which was established to investigate, disrupt and prosecute ransomware and digital extortion activity. This is the Task Force’s first operation of this kind.
On June 5, 2021 I did a quasi deep dive into TrickBot and Alla Witte, aka “Max” indictment and her role in banking trojan known as Trickbot - I would recommend you reread it because I’m going to weave a few threads that at first glance do bot, I mean not seem to connect. Spoiler -they do but it’s kind of complicated.
…the entire ecosystem that fuels ransomware and digital extortion attacks…
On June 7, 2021 Deputy Attorney General Monaco2 explicitly stated;
By going after the entire ecosystem that fuels ransomware and digital extortion attacks – including criminal proceeds in the form of digital currency – we will continue to use all of our resources to increase the cost and consequences of ransomware and other cyber-based attacks.
The subtext of the aforementioned should put cyber criminals on notice, it should also put “bulletproof hosting” companies, cryptocurrency and teleco companies on notice. Meaning if you’re enabling the “cyber-ecosystem” helping malicious actors engage in ransom and extortion, the DOJ is coming for you. Specifically Ransomware and Digital Extortion Task Force (RADE) are coming after you. It doesn’t matter how long it takes. Or how many miles these FBI agents travel - you engaged in digital extortion: THEY. ARE. COMING. FOR. YOU. all of you. All of the ill gotten largesse —welcome to Asset Forfeiture. Your network of hackers, VPN providers, your C2 Servers, all of your infrastructure— the DOJ and FBI will hunt you like a predator hunts it’s prey. And that truly delights me because our DOJ will leave no stone unturned and will throw the entire weight of the DOJ to bring the criminals to justice.
APT29, aka Nobelium
On May 27, 2021 Microsoft Threat Intelligence Center announced “Another Nobelium Cyberattack” via their blog - while some say this is likely part of Russia’s SVR..put a pin in that, I’ll come back to it later.
Microsoft Threat Intelligence Center (MSTIC) has uncovered a wide-scale malicious email campaign operated by NOBELIUM, the threat actor behind the attacks against SolarWinds, the SUNBURST backdoor, TEARDROP malware, GoldMax malware, and other related components.
The campaign, initially observed and tracked by Microsoft since January 2021, evolved over a series of waves demonstrating significant experimentation. On May 25, 2021, the campaign escalated as NOBELIUM leveraged the legitimate mass-mailing service, Constant Contact, to masquerade as a US-based development organization (USAID) and distribute malicious URLs to a wide variety of organizations and industry verticals.
What’s worse? The hackers used former president Trump's name in emails that this group sent to the targeted users. In Microsoft’s publication they included a sample of the phishing emails - on May 25th -Microsoft observed the NOBELIUM campaign had escalated significantly.
Using the legitimate mass mailing service Constant Contact, NOBELIUM attempted to target around 3,000 individual accounts across more than 150 organizations. Due to the high-volume campaign, automated systems blocked most of the emails and marked them as spam. However, automated systems might have successfully delivered some of the earlier emails to recipients.
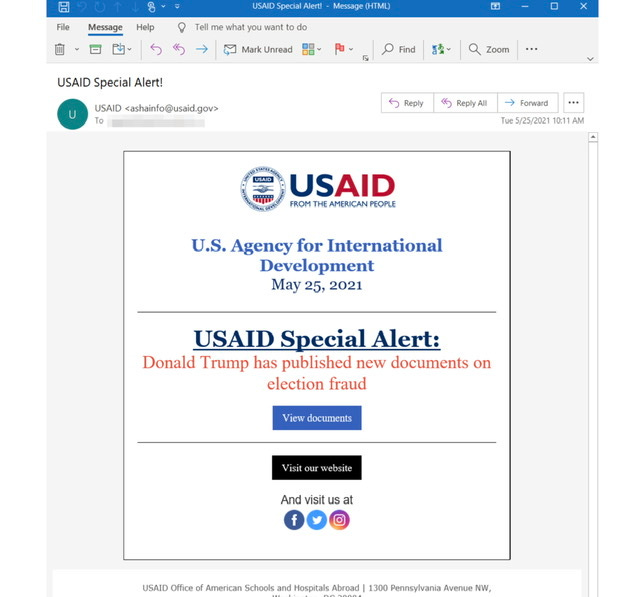
In the May 25 campaign, there were several iterations. In one example the emails appear to originate from USAID <ashainfo@usaid(.)gov>, while having an authentic sender email address that matches the standard Constant Contact service. This address (which varies for each recipient) ends in @in.constantcontact.com, and (which varies for each recipient), and a Reply-To address of <mhillary@usaid(.)gov> was observed. The emails pose as an alert from USAID, as seen below.
the subject line of the email said: "USAID Special Alert!
" The email was sent from a USAID.gov email address.
The email said "Donald Trump has published new documents on election fraud," with a "view documents" button underneath it.
Microsoft issued the alert and supplement security research regarding this sophisticated email-based campaign that NOBELIUM has been operating to help the industry understand and protect from this latest activity.


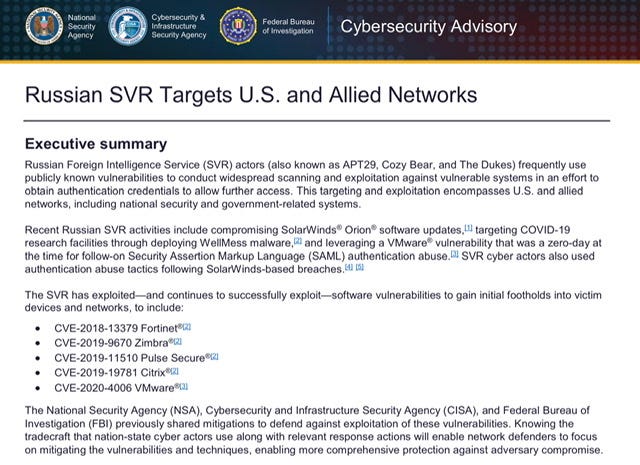
On April 15, 2021 Russian Foreign Intelligence Service Exploiting Five Publicly Known Vulnerabilities to Compromise U.S. and Allied Networks - The National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI) jointly released a Cybersecurity Advisory, “Russian SVR Targets U.S. and Allied Networks”
Russian Foreign Intelligence Service (SVR) actors (also known as APT29, Cozy Bear, and The Dukes3) frequently use publicly known vulnerabilities to conduct widespread scanning and exploitation against vulnerable systems in an effort to obtain authentication credentials to allow further access. This targeting and exploitation encompasses U.S. and allied networks, including national security and government-related systems.
NSA, CISA, and FBI are aware that United States Government, critical infrastructure (including Defense Industrial Base), and allied networks are consistently scanned, targeted, and exploited by Russian state-sponsored cyber actors. NSA, CISA, and FBI recommend that critical system owners prioritize the following mitigation actions to mitigate the loss of sensitive information that could impact U.S. policies, strategies, plans, ongoing operations, and competitive advantage.
Additionally, due to the various systems and networks that could be impacted outside of these sectors, NSA, CISA, and FBI recommend that the following mitigations be prioritized for action by all network defenders.
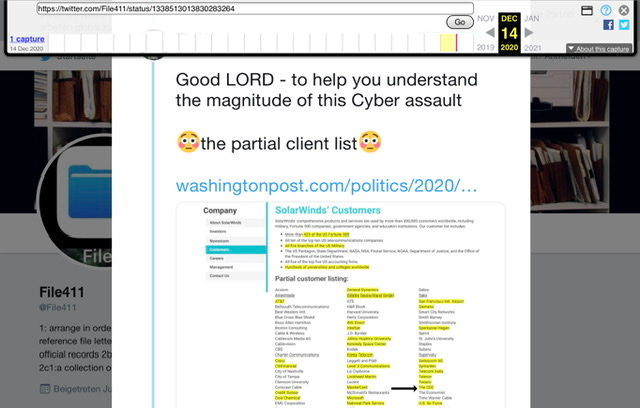
At this point you are probably wondering - how does Trickbot, Emotet and NOBELIUM tie together. Or where are you going with this? Well if you followed me on Twitter back in 2017 thru 2021 I repeatedly said: y’all need to pay attention to Microsoft and EDVA - well what if I told you that this archived December 2020 Thread was me laying down a marker about how much cyber-pain America was about to face.
I literally tweeted a partial list and said GOOD LORD - or the hell I received for asking two questions (before we knew about Solarwinds) Did this impact Azure and/or 365 and is there a kill switch to find the malware designed to evade any and all software detection…
Because…drum roll please…and no I’m too busy to comb through the vacuous archives of my Twitter threads, but I distinctly remember saying in August 2017 - watch EDVA and any filing by Microsoft, they are using a pretty novel (at the time) argument to regain the domains purloined by cyber criminals.


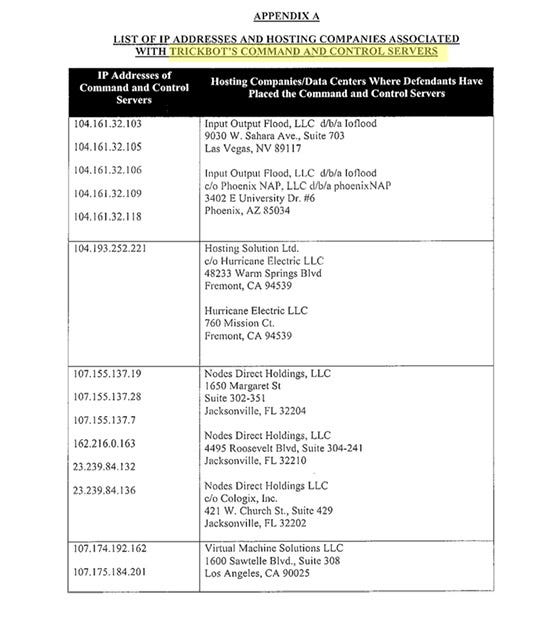
Now for the good stuff - it’s not always in the footnotes, in this particular case it was in the actual appendixes and you should have paid attention back in October 2020
Microsoft Corporation v. John Does 1 (1:20-cv-01171) https://ecf.vaed.uscourts.gov/doc1/189010780252
If you read the body of Microsoft’s October 2020 Trickbot Complaint -for Example read paragraph 11 and pay attention to what I highlighted 4 5
Wait did someone say Ryuk too? Cool November 2019 archived Twitter thread Because the reality is the previous administration didn’t give a ___ about cyber security and the vacuum they left gave numerous adversaries (Nation States) the green light to come on in and make yourself comfortable within not just our Federal IT Infrastructure but also State and Local, Law Enforcement and in the private sector. The fact the new administration understands just how vulnerable we are and are acting both reactively and proactively and with “time is of the essence” is both under reported and under appreciated.
Again this bears repeating Microsoft filed this action in October 2020 in EDVA but reading the Appendix A is something you should do - the targeting of Command and Control (C2) servers are part of the and if you paid attention you’d see breadcrumbs that included Cobalt Strike tool in the October 2020 filing. Also because I can you might find this October 2020 Archived Twitter thread helpful (yes I did in fact remind you of this thread in the article published over this weekend it was a deep and I mean deep dive into Alla Witte & TrickBot Group)
…the entire ecosystem that fuels ransomware and digital extortion attacks…
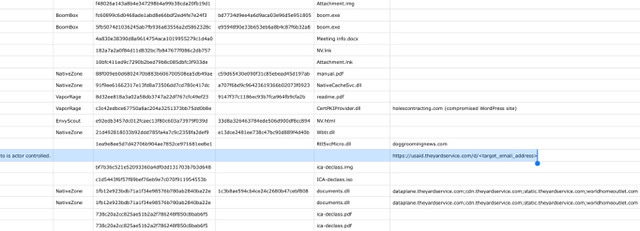
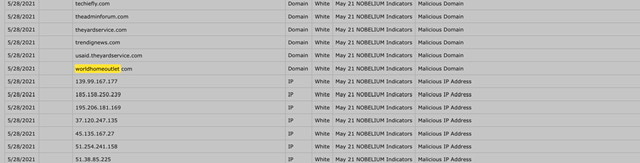
On May 28, 2021 Microsoft published indicators of compromise (IOCs) NOBELIUM Campaign the spreadsheet contains a total of thirty-four domains used during the cyber attacks. If you look closely you will note the DOJ seized these two domains; theyardservice[.]com and worldhomeoutlet[.]com;
28/20215/25/2021 https://r20.rs6.net/tn.jsp?<unique_to_target>UrlWhiteMay 21 NOBELIUM Indicators Email Url; note this is simply the Constant Contact redirector URL. The URL redirected to is actor controlled. https://usaid.theyardservice.com/d/<target_email_address>
dataplane. theyardservice.com;cdn.theyardservice.com; static.theyardservice.com;worldhomeoutlet(.)com
As the June 1, 2021 Department of Justice’s OPA states - DOJ-OPA
“Upon a recipient clicking on a spear-phishing email’s hyperlink, the victim computer was directed to download malware from a sub-domain of theyardservice[.]com…. Using that initial foothold, the actors then downloaded the Cobalt Strike tool to maintain persistent presence and possibly deploy additional tools or malware to the victim’s network…The actors’ instance of the Cobalt Strike tool received C2 communications via other subdomains of theyardservice[.]com, as well as the domain worldhomeoutlet[.]com. It was those two domains that the Department seized pursuant to the court’s seizure order."
And that’s how you know what you know - it requires you to read the various Court filings, remember what was in filings and then laying over those retained facts to present (or near present) day actions by the DOJ and FBI to understand how the RADE Task Force is going in with surgical precision to…attack and dismantle
…the entire ecosystem that fuels ransomware and digital extortion attacks…
Because the newly formed/sanctioned
RANSOMWARE AND DIGITAL EXTORTION TASK FORCE DETAILS
Members of Task Force
Criminal Division, including
Computer Crime and Intellectual Property Section (CCIPS) o Office of International Affairs (OIA)
Money Laundering and Asset Recovery Section (MLARS)
National Security Division
Counter Intelligence and Export Control Section (CES)
Executive Office of U.S. Attorneys
Civil Division
Federal Bureau of Investigation
With input from National Cyber Investigative Joint Task Force (NCIJTF)
These are the best of the best and it doesn’t matter how long it takes. I have the utmost confidence in the Department of Justice and the FBI and our International Allies that there are going to dismantle the “entire ecosystem” and that just thrills me.
And lastly if this article reads kind of disjointed well that’s probably because I had it saved in my drafts and meant to publish it back in January but other things kept grabbing my attention. Oddly I’m kind of glad I was distracted because it allowed for the DOJ and FBI and Microsoft to better develop the facts and the disbursed dots then oddly seem to suddenly connect. Unintentionally and for better or worse ransomware is here to stay. Corporate America better harden their defenses as should all Government Agencies - from Federal to State to local municipalities the cyber criminals are getting smarter, faster and far more pernicious.
Should you be inclined
Feb 2021 - I don’t WannaCry...said Kim Jong-un. I just need more crypto currency because the sanctions are killing my vibe and money flow.
May 2021 - Our critical infrastructure is seriously at risk. Ask Colonial Pipeline what their MTTR is...
May 2021 - Kyle Cary -Hugo Stacks - why did you have a May 17, 2021 Detention Hearing?
June 2021 - FINALLY - yes- Alla Witte, aka “Max” banking trojan known as Trickbot - Latvian National Charged for Alleged Role in Transnational Cybercrime Organization —probably one of my deeper dives.
Paying a ransom is a very very bad idea. Nexus to OFAC, Sanctions, Colonial Pipeline $4.4M but lesser known. CNA Financial Corporation paid $40,000,000.00 in ransom - OFAC Oct 2020 Nat Sec & Nexus CNA
Biden White House National Security Study Memorandum -Fight Against Corruption- ahead of G7 & NATO summits (next week) timing matters - enhancing criminal and civil enforcement under the Global Magnitsky Act, TOP Priority. Also enforcement of the Justice Department’s Kleptocracy Asset Recovery Initiative.
Not only do we need to be mindful about “outsider attacks’ but the insider threat continues to persist
For example April 2021 - WYATT TRAVNICHEK - indicted for hacking into a Kansas public water system
When it comes to cyber security - eat or be eaten - yes it is that simple but out maneuvering cyber-criminals means hardening your cyber security protocols and constantly monitoring it - because real cyber security is never a “set it and forget it” endeavor. And it’s not like House Democrats are ignoring the persistent threat
H.R. 2980, The “Cybersecurity Vulnerability Remediation Act”
H.R. 3138, The “State and Local Cybersecurity Improvement Act”
Amendments adopted by the House Homeland Security Committed
Recent Action taken by the House Homeland Security Committee - for example H.R. 2795 amendments will have consequential impacts and I’m glad it was agreed upon
The Chair discharged the Subcommittee on Oversight, Management, and Accountability from further consideration of H.R. 2795.
The following amendments were offered:
An amendment offered by Mr. Swalwell (#1): Page 3, line 9, strike “(F)” and insert “(I)”. Page 3, beginning line 9, insert the following: (G) The Office for Civil Rights and Civil Liberties. (H) The Privacy Office. Page 3, after line 10, insert the following: “(2) CHARTER.—The Secretary is authorized to issue a charter for the Board, and such charter shall specify the following: (A) The Board’s mission, goals, and scope of its activities. (B) The duties of the Board’s representatives. (C) The frequency of the Board’s meetings.” Page 3, line 11, strike “(2)” and insert “(3)”. Page 4, line 1, strike “(3)” and insert “(4)”; was AGREED TO by unanimous consent.
DAG Monaco June 7, 2021 Press Release Transcript - https://www.justice.gov/opa/speech/dag-monaco-delivers-remarks-press-conference-darkside-attack-colonial-pipeline
Microsoft calls Nobelium and is also known as APT29, Cozy Bear, and the Dukes - the Dukes tend to go old school and they have been around since at least 2007
“From there, the actor was able to distribute phishing emails that looked authentic but included a link that, when clicked, inserted a malicious file used to distribute a backdoor we call NativeZone… This backdoor could enable a wide range of activities from stealing data to infecting other computers on a network.” Microsoft Vice President of Customer Security and Trust Tom Burt wrote in a wrote in the May 27, 2021 Microsoft Blog post
For the record back in 2017 when Microsoft argued the “novel” argument about trademark and copyright infringement it was an argument that a lot of firms in the Beltway silently held their collective breaths because the ruling could *and* did have wide reaching implications. And the Microsoft 2017 “novel argument” is no longer novel because Microsoft won and the Court Ordered the seizure of the domains - see 2017 EDVA Microsoft Complaint https://ecf.vaed.uscourts.gov/doc1/18908385837m
In the 2017 Microsoft EDVA BARIUM Complaint the premise of the action; (1) The Computer Fraud and Abuse Act, 18 U.S.C. § 1030; (2) Electronic Communications Privacy Act, 18 U.S.C. § 2701; (3) Trademark Infringement under the Lanham Act, 15 U.S.C. § 1114 et seq. (4) False Designation of Origin under the Lanham Act, 15 U.S.C. § 1125(a); (5) Trademark Dilution under the Lanham Act, 15 U.S.C. § 1125(c); (6) common law trespass to chattels; (7) unjust enrichment; (8) conversion; and (9) intentional interference with contractual relationships.
“…Microsoft seeks injunctive and other equitable relief and damages against Defendants who operate and control a network of computers that include the Barium Profiles and the Barium Command and Control Domains. Defendants, through their illegal activities involving Barium, have caused and continue to cause irreparable injury to Microsoft, its customers and licensees, and the public.” In November of 2018 the Court Granted Microsoft’s Permanent Injunction ,











I would never in my life have drawn threads between any of us. Thank you for your dogged, exceptional investigatory work!