PETER YURYEVICH LEVASHOV are you still cooperating?
Your sentencing hearing has been continued 4xs. As recently as June 12, 2021 - did your agreement require you to give up your entire crew? Me thinks YES Glasses on. Red Bull chugged. Keyboard Engaged
Earlier this week I published the following article concerning Defendant Koshkin guilty verdict. As many of you know I’m not a reporter. Nor do I receive any compensation for any of my articles and research. And during the work week my bandwidth tends to be limited. The upside to Twitter was I could pump out a lot of factual information but it also created disjointed and often rimes truncated threads. Those threads were understandably hard to follow.
However on the Substack platform, I think this provides a much quieter information ecosystem/platform. Where I can expound on various court filings and then explain how ABC Case is related to XYZ case. I also like the ability to answer questions without being limited to 240 characters. So I have one pretty straightforward question;
Have you figured out why I embedded all of those search warrants?
I embedded some thirty-one search warrants, which were placed at the end of the article.
Full Disclosure this is going to be a very deep and intensive dive because I decided to fully chase the Botnet Rabbit and it landed me into several cases litigated over a decade ago. I make zero apologies for the amount of data and facts that are included. By now most should know I have the ability and desire to fully and completely research “things”…
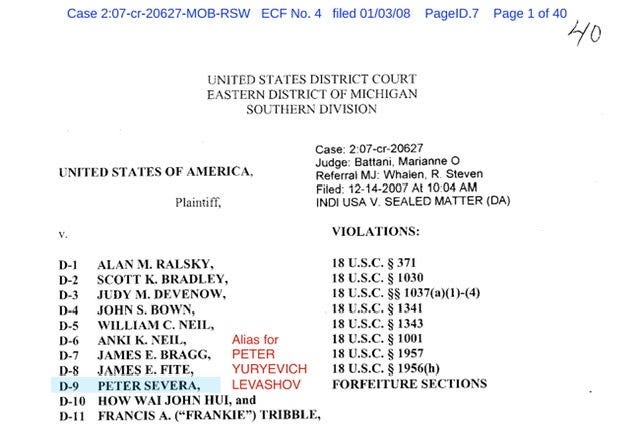
PETER YURYEVICH LEVASHOV Aliases
You need to.keep these alias in mind because this is what you need to know to find the 2007 and 2009 indictments -mentioned in the footnotes of the previous search warrants.
Petr Levashov, Peter Severa, Petr Severa and Sergey Astakhov
What do I say about footnotes? Yes - always read them because that’s where you tend to find the “good stuff” - for example in one of the latter search warrants I embedded in yesterday’s article - which reads in part:
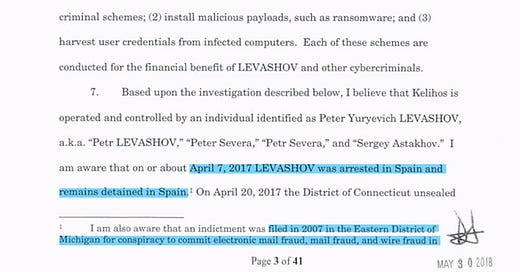
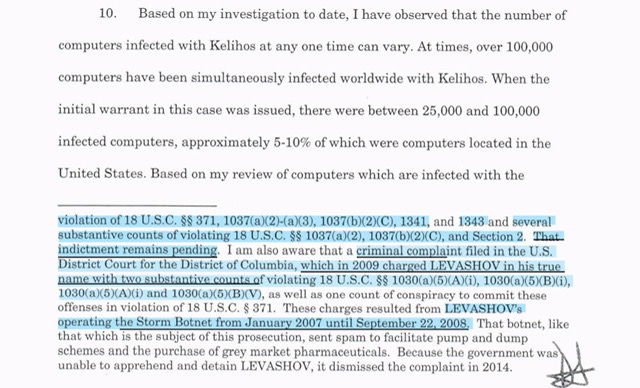
I am also aware that an indictment was filed in 2007 in the Eastern District of Michigan for conspiracy to commit electronic mail fraud, mail fraud, and wire fraud in violation of 18 U.S.C. §§ 371, 1037(a)(2)-(a)(3), 1037(b)(2)(C), 1341, and 1343 and several substantive counts ofviolating 18 U.S.C. §§ 1037(a)(2), 1037(b)(2)(C), and Section 2. That indictment remains pending
To be accurate I do NOT believe the 2007 date in the footnote is unintentional error by the affiant…I tried pulling up both cases but it appears I might need to access both via a terminal. And my assumption was in fact correct re the 2007 (filed) indictment which was unsealed in 2008. Terminal access baby. And boy oh boy was this case an interesting read. Hence why the alias are/were important otherwise you wouldn’t know this was the 2007 criminal case.
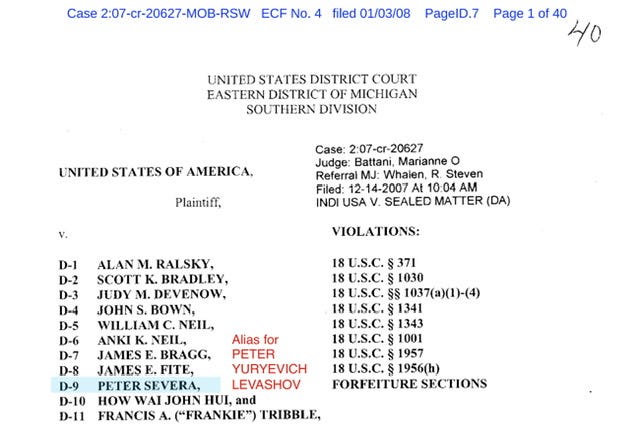
United States v. Ralsky
2007 Criminal - EDMI Case No 2:07-cr-20627 indictment or you can pull down a highlighted/annotated copy via my public drive
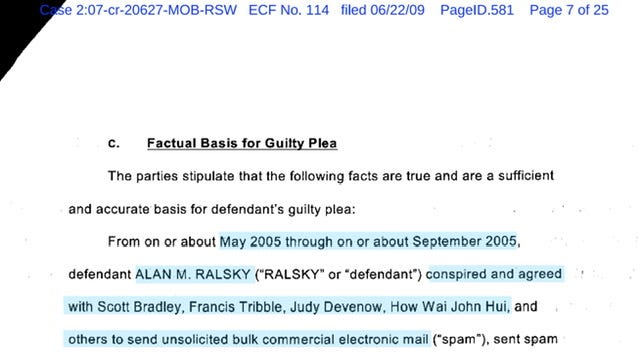
On July 22, 2009 the Government and the lead Defendant entered into a plea agreement - see ECF-link for Defendant Ralsky PLEA AGREEMENT
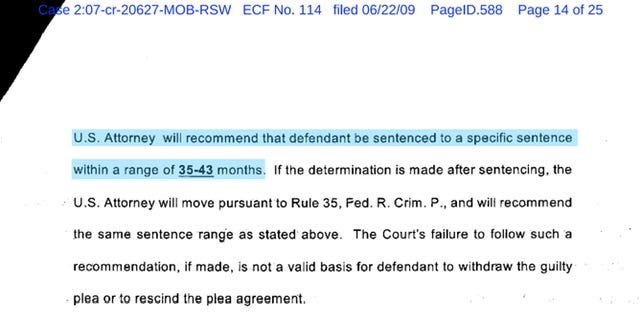
Defendant Ralsky was looking at 70 to 87 months - the Government offered to recommend sentencing to 35-42 months - provided however the Defendant continued to cooperate with the Government and if the Government felt his cooperation met the “substantial assistance”…then the Government would recommend on the lower end of imprisonment.
Per this 2009 DOJ-OPA Release Defendant Ralsky was sentenced to 51 months in prison and 5 years supervised release. The assumption is that if the Government states they will ask the Court for the lower end of the sentencing - that’s actually not always the case. The Court is given wide discretion and almost always factor in “a defendant’s prior acts”—the fact Defendant Ralsky was sentenced to 51 months - that might be an inference that the Government didn’t believe the Defendant kept his word to “provide substantial assistance” or it could be the Court using their discretion. Notwithstanding it’s the second to last paragraph in that 2009 DOJ-OPA that caught my attention… which reads in part:
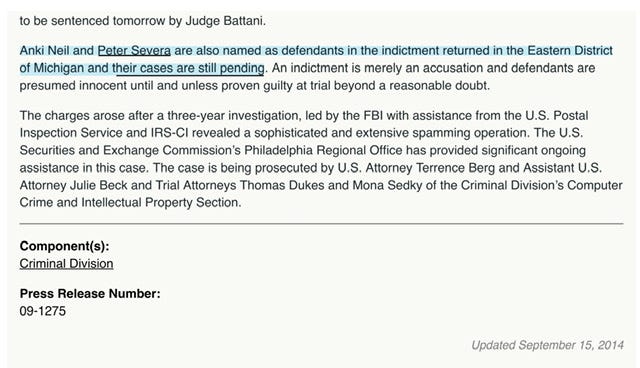
Anki Neil and Peter Severa are also named as defendants in the indictment returned in the Eastern District of Michigan and their cases are still pending.
Also did you notice how the footnote cites other cases - one of which was dismissed in 2014 (DDC indictment) because the Government was unable to “apprehend and detain LEVASHOV” - full disclosure I have yet to find his DDC 2009 indictment and I apologize because I genuinely feel like I let my readers down.
I am also aware that a criminal complaint filed in the U.S. District Court for the District of Columbia, which in 2009 charged LEVASHOV in his true name with two substantive counts ofviolating 18 U.S.C. §§ 1030(a)(5)(A)(i), 1030(a)(5)(B)(i), 1030(a )(5)(A)(i) and 1030(a)(5)(B)(V), as well as one count of conspiracy to commit these offenses in violation of 18 U.S.C. § 371.
These charges resulted from LEVASHOV's operating the Storm Botnet from January 2007 until September 22, 2008. That botnet, like that which is the subject ofthis prosecution, sent spam to facilitate pump and dump schemes and the purchase of grey market pharmaceuticals. Because the government was unable to apprehend and detain LEVASHOV, it dismissed the complaint in 2014.
PETER YURYEVICH LEVASHOV
Let’s first address the primary case - styled as:
United States v. Levashov Case No: 3:17-cr-00083-RNC
United States v. Levashov Case No 3:17-cv-00074 a copy of the 2017 (Alaska) TRO and affidavit can be found on my public drive the Redacted Memorandum of Law in Support of Motion for TRO is a must read, You can also pull down a highlighted/annotated copy of the 2017 Memo from my public drive. Although my favorite part the the 2017 Memo:
The sinkhole server will be a dead end destination designed specifically to neither decrypt nor capture content from the infected computers.
The sinkhole server, hovvever, will record the IP address and associated routing information of the infected machine so that the proper Internet Service Providers can be alerted of the existence of infected machines on their network and to monitor the effectiveness of the disruption effort
Criminal Complaint Filed March 24, 2017
18 U.S.C. Section 371,1349,1028 (a)(7), 10284, 1030(a)(2), 1030(c)(2)(B), 1030(a)(a), 1030(c)(3XA), 1030 (aX5XA), 1030(c)(a)(B), 1030(a)(7), 1030(cX3XA), 1037(aX1 ), 1037(a) (2),1037(a)(3), 1037(bX1), 1343, 2511, eB1 (aX1 ), 1037(c)
Criminal Complaint (via my public drive) Offense Description - Conspiracy to Commit Fraud & Related Activity in Connection with Computers & with Electronic E-mail; Conspiracy to Commit Wire Fraud; ldentify Theft in Connection with another FederalViolation; Aggravated ldentity Theft; Fraud & Related Activity in Connection with Computers; Fraud and Related Activity in Connection with Electronic Email; Wire Fraud; lllegal Wiretapping; Forfeiture
April 20, 2017 Indictment as to Defendant Levashov
INDICTMENT (see Public Drive) returned before Judge William I. Garfinkel with the signature of the foreperson redacted. Grand jury number 16-1. Warrant to issue as to Peter Yuryevich Levashov (1) count(s) 1, 2, 3, 4, 5, 6-7, 8.
Count One
The Kelihos botnet is controlled by LEVASHOV through command and control servers, which enable LEVASHOV to issue commands to any and all bots in the Kelihos botnet.
LEVASHOV controlled and operated the Kelihos botnet to, among others things: (a) harvest personal information and means of identification (including email addresses, usernames and logins, and passwords) from infected computers; (2) disseminate spam; and (3) distribute malware, including Trojans and ransomware
Count Two:
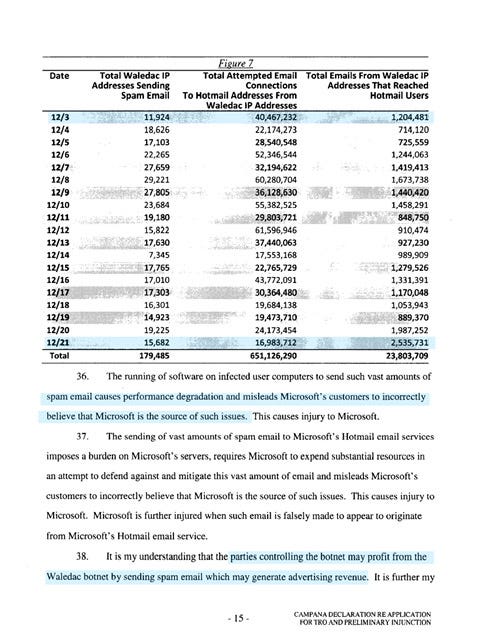
setting aside just how harmful the Kelihos Botnet whereby the Kelihos Botnet sent 4 billion spam emails per day
…defendant, PETER YURYEVICH LEVASHOV, did unlawfully, knowingly, and intentionally conspire, combine, confederate, and agree with others unknown to the Grand Jury, to commit offenses against the United States in connection with the operation and monetization ofthe Kelihos botnet;
A purpose of the conspiracy was for LEVASHOV and his co-conspirators to operate, perpetuate, control, and profit from the Kelihos botnet, and to conceal the conspiracy from others.
Waves - hiya JokeFromMars - you should read this article -as it is one of the most comprehensive article I’ve read about how Kelihos was used to deliver malware - because the “delivery” is something that I think is kind of interesting and it allows you have a much more focused and high level overview. I’d also read this companion Article —which details how Kelihos tripled its Botnet size within 24 hours.
Sept 2018 Plea Agreement Peter Levashov
See DCCT-ECF https://ecf.ctd.uscourts.gov/doc1/04106115448 (or you can pull down LEVASHOV’s plea agreement from my public drive) Notwithstanding in the plea agreement -Peter Yuryevich Levashov pleaded guilty to the following;
Count One (charging him with intentional damage to a protected computer, in violation of 18 U.S.C. §§ 1030(a)(5)(A) and (c)(4)(B), and 2), Count Two (charging him with conspiracy, in violation of 18 U.S.C. § 371), Count Four (charging him with wire fraud, in violation of t18 U.S.C. §§ 1343 and 2), and Count Eight (charging him with aggravated identity theft, in violation of 18 U.S.C. §§ 1028A and 2) of the Indictment.
Based on the statutes - the combined maximum term of imprisonment for Defendant LEVASHOV; Count One -Maximum term of imprisonment 10 years, Count Two -Maximum term of imprisonment 5 years, Count Four -maximum term of imprisonment of 20 years, Count Eight -mandatory term of imprisonment of two years… so if you included the Counts LEVASHOV pleaded guilty to —you’re in the neighborhood of up to 37 years — in addition to 18 U.S.C. § 3663A -Mandatory restitution to victims of certain crimes which requires the Court to Order the Defendant to pay restitution, this is not negotiable- it is mandatory.
Also you’ll note on page 8 of the Plea Agreement the USSC Guidelines state that a level one reduction is warranted but as you’ll note in the stipulation the Government agreed to a level three reduction - also I’d like to draw your attention to the blue circle -see what was added & initialed - “loss or…”
LEVASHOV operated Storm Waledac & Kelihos botnets possibly Rustock Botnet too
-this is me grinning ear to ear and whispering “I told you so” - well technically it was Spicer’s-Mic that told you so - but meh preening and bragging isn’t really my thing (snort) - for now put a pin in this because I am pretty sure only a very few had the Storm & Waledec on their EDVA circa 2010 Bingo Card…
…late 1990s until his arrest on April7, 2017, the defendant Peter Levashov operated botnets under various aliases, most notably "Peter Severa". His botnets, which included the Storm, Waledac, and Kelihos botnets, (a) harvested personal information and means of identification (including email addresses, usemames and logins, and passwords) from infected computers; (2) disseminated spam; and (3) distributed malware, including Trojans and ransomware.
Over the course of his criminal career, Levashov participated in and moderated various online criminal forums on which stolen identities and credit cards, malware, and other criminal tools of cybercrime were traded and sold. In so doing, Levashov used, among other online identifiers, ICQ number I 04967, jabber@honese.com, and peter@severa.biz to chat or communicate with others online.
The second page of STIPULATION OF OFFENSE AND RELEVANT CONDUCT - it’s the last paragraph that give you an idea of the actual cost of destruction his Botnet caused - which reads in part:
At the time of Levashov's arrest, Kelihos infected at least 50,000 computers. The parties stipulate and agree that it would cost as much $149 per computer to remove the Kelihos virus from each infected computer.
The defendant also agrees that the unlawful gain from the criminal conduct described above exceeds $3.5 million.
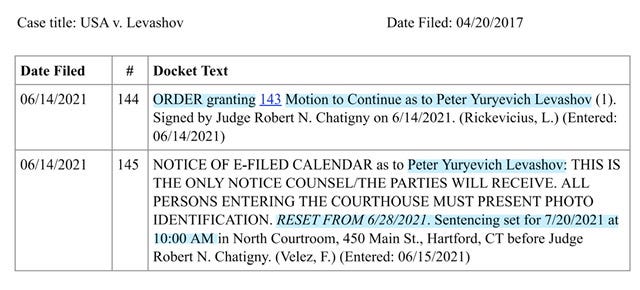
Sentencing Hearing Continuances
Have you wondered about the rhetorical question that I posed in the article title? Musing if LEVASHOV is still cooperating with the Government— because here’s why I asked the question - his sentencing has been continued at least four times. Since May 2020, with the 4th continuance as recent as June 12, 2021 - and the Court agreed to move Levashov sentencing to July 20, 2021 so here’s your official “save the date”
Not to belabor or further confuse you - but now we are going to discuss the intersection of…
Oleg Koshkin, Pavel Tsurkan and Petr Levashov
…one thing to keep in mind (see Levashov’s stipulation of offense and relevant conduct, which was an attachment to his plea agreement) is the Government disclosed an interesting “year” —see the second paragraph in the stipulation which reads in part:
“Since the late 1990’s until his arrest on April 17, 2017 the Defendant…”
…the reference of “late 1990’s” —in my opinion that’s the Government laying down a marker. If my preliminary research is correct (which I have the receipts) …then this would mean from approximately 1998 to 2009 are a precursor and pivotal to his 2017 arrest. For now I’d like you to remember these names/entities;
DMITRY A NIJEGORODTSEV
JODY MICHAEL SMITH
LANCE THOMAS ATKINSON
OLEG Y NIKOLAENKO
Each of the aforementioned link back to LEVASHOV, spam botnets, for now put a pin in those names - but also remember that the Federal Trade Commission (FTC) is an enforcement agency and played an integral role in the take down of a few spam botnets. More on that later. For now let’s turn our attention to;
DCCT October 2019 Case No 3:19-cr-00251
The numerous and at times what appear to be unrelated threads/dots - this is why I purposely started with the dissection of LEVASHOV’s “other cases” —You needed to understand (in the context of the 2019 criminal cases of his two co-conspirators Koshkin and Tsurkan, respectively) that by 2018 LEVASHOV was fully cooperating with the Government. Pursuant to his plea agreement. And he had a lot of incentive to provide the Government with “substantial assistance” - while most might not read every page of an Affidavit- I highly recommend you do
Aug 28, 2019 SEALED COMPLAINT as to Oleg Koshkin, Attachments: # 1 Affidavit it’s a 22 page Affidavit and vast majority of the affidavit explains (in very granular detail) how LEVASHOV set up the Botnet. How he perfected the code. How he customized the encryption. And lastly but importantly how & who he marketed his services to.
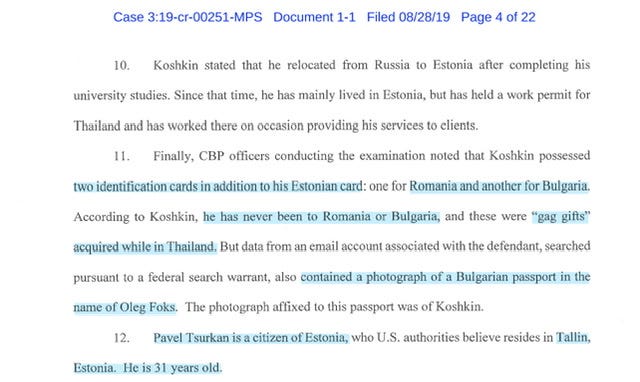
Defendant Koshkin: Look Mr CBP Officer the two identification cards (Romania and Bulgaria) I legit have no idea how those got in my luggage - I think they were “gag gifts” that I just picked up in Thailand and the whole Bulgarian Passport picture you guys obtained via a Federal Search Warrant - I have no idea who “Oleg Folks’ is - it’s also weird that Oleg appears to be my doppelgänger
CBP Officer: Sir please follow me to the secondary screening that will be conducted in a holding cell.
Defendant Koshkin: No hablo inglés…inaudible sobbing
FUD - Fully UnDetectable - Crypt4U -see paragraphs 20 and 21 but specifically paragraph 21 <— May 2021 letter to the Court during the Trial. Yes trust me on that.
Levashov's communications with Crypt4U personnel indicated that several people worked for the organization. There were individuals who handled customer service, such as answering questions and handling help ticket requests. Such individuals included the user of Jabber8 ID ("JID") info@crypt.am and the user of various iterations of the JID "01", such as 01@default.rs, 01@xmpp.re, and 00001@exploit.im.
In short LEVASHOV was the master mind. Whereas Koshkin and Tsurkan helped perfect the code to evade a whole subset of malware detection software vis-a-vis crypt.
Peter Levashov and the Kelihos Botnet -paragraphs 13 thru 32
Probable Cause that Oleg Koshkín Used the Alisses Admin and Dr. X - paragraphs 33 thru 49
Probable Cause that Pavel Tsurkan Used Alias Russian8 - paragraphs 50 thru 63
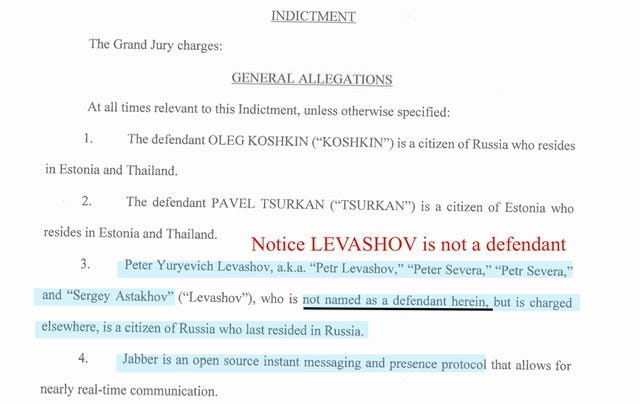
The October 2019 Indictment is pretty straightforward - however off the bat you’ll notice on page 1 -paragraph 3 states that “LEVASHOV is not a defendant herein, but was charged elsewhere”
And what separates this indictment from others is the Government greatly expanded and it appears the focus of Crpty4U which was an approach by the defendants to LEVASHOV- allowing him to encrypt specific “customer malware requests” - but as you’ll note this indictment heavily focused on: Trojan, Keyloggers, RATs (Remote Access Trojans <—super bad and pernicious AF) and broadly ransomware.
May 24, 2021 ORDER as to Oleg Koshkin. ORDER. The Court is in receipt of the letter submitted by the Government regarding Jabber and Skype communications that the Government addressed in its trial memorandum.
As previously explained in the Criminal Complaint and Affidavit and subsequent indictment - during Defendant Koshkin Trial, on May 24, 2021 the Government sent this two page letter to the Court - see what I redlined? Yes that’s a reach back to the original affidavit
Exhibit 36: This is a chat with russian8@xta.im. Again, there is discussion about the need for the loader to be small, but that the size of the actual “bot” is not critical. There is also discussion about using a new crypter to avoid detection by a specific antivirus program “which nobody bypasses.”,
Exhibits 65-72: These are Skype chats found on Koshkin’s Galaxy S7 cell phone. The communications by Koshkin are statements by a party opponent and therefore not hearsay. The communications by the other parties are not being offered for the truth of the matters asserted, but to establish Koshkin’s continuing participation in the crypt4u service and to provide necessary context for Koshkin’s statements
Microsoft and EDVA
Do you remember that time - when there was this nagging PITA Twitter account that would randomly start threads that typically started with:
🚨MICROSOFT EDVA 1 start paying ATTENTION🚨
…to wit half of Twitter was like “STFU.. stay in your lane”- blah- “you’re just a bored alcoholic housewife” -blah- “this is above your pay grade” -blah- “you stupid <insert misogynistic noun> you are not in the intelligence community” blah
For the record until such time I start walking on all fours and randomly start humping people just to show my dominance. ProTip: if you as a man toss around the “female dog” adding “crazy” and “unstable” —spoiler I hate to break this to you but that kind of misogynistic patriarchy shows you really do hate women. Unsolicited advice; stop “acting” like you’re a protector of women. You are not and the record is crystal clear.
Yes, let me tell you that those were super fun times - what if I told you that had you heeded my (quasi educated) Twitter threads. Which typically contained numerous Court filings, a lot of spice/snark and the occasional “WTF am I tweeting in Aramaic or pig Latin” then the need for such a detailed article wouldn’t actually exist because you would have already known to BOLO for Microsoft and EDVA.
Again it would be super dandy if I could retweet those threads but alas they are “gone with the wind” - like “dust in the wind” also you can thank the trolls, stalkers and haters for the incomprehensible amount of research that is now gone. Again the point is if you had taken the Tweets to heart then you would have known about;
Microsoft Operation b49 - Waldec Botnet takedown
Microsoft Corporation v. Doe EDVA (Alexandria) Case No 1:10-cv-00156
Microsoft Corporation v. Piatti EDVA (Alexandria) Case No 1:11-cv-01017
You can read more about Microsoft Operation b49 and yes it’s easy to blame Microsoft but the reality is they have stepped up their cyber security game and at times their own Cyber Crime/Intelligence units have been months and sometimes years ahead of Federal Law Enforcement. But in recent months the Federal Law Enforcement has absolutely staffed up and the current Department of Justice and FBI are going on the offense and that truly delights me.
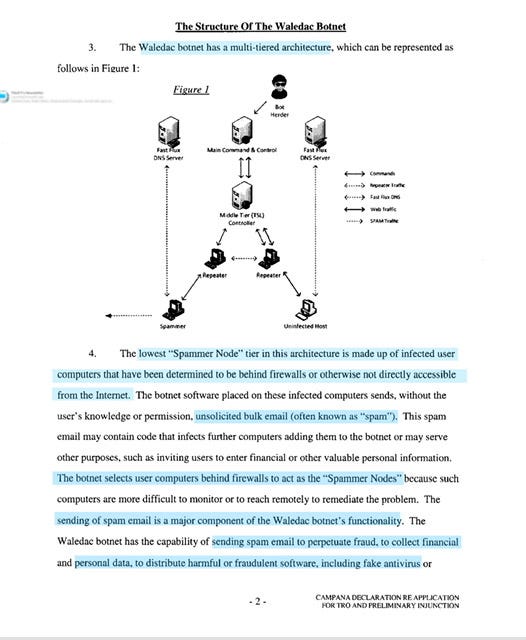
I mean Microsoft filed this on February 22, 2010 <—that is not a typo - yes February of 2010 - Microsoft even included a flow chart.
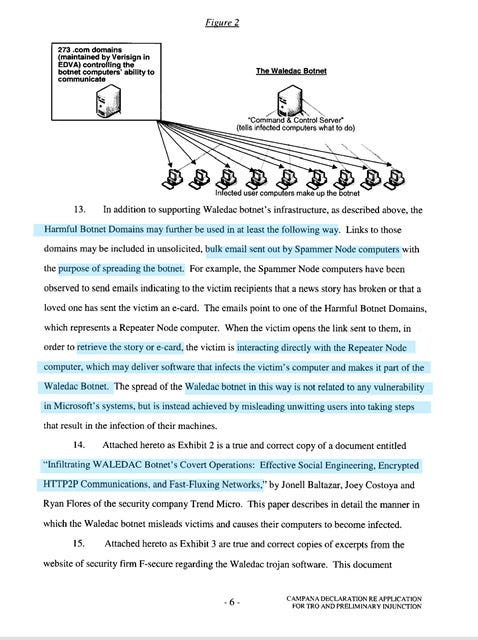
Microsoft’s investigator was able to not only map out the Waldec Botnet but it appears that they were able to not only penetrate the botnet but they stuck around to observe the traffic coming in and going out …”the TSL Servers received inbound communication from Repeater Nodes”
Not only was Microsoft able to completely map out the Botnet configuration but they discovered that -TSL Severs + tucked in C2 servers + Fast Flux DNS + continual domain and VPN and IP address change = trying to hunt the botnet was like trying to cut jello with your pinky nail.
“behind the TSL Severs…there are one or more Command and Control severs…referred to as ‘Main Command and Control…Fast Flux …constantly changing the root name servers at the registrars…”
Welcome to cyber hell from 2009-ish fine tuning a botnet for maximum impact with minimal effort - keep in mind this was over a decade ago. If you’ve followed me on Twitter or blogs then you’d know I tend to use the phrase “Cyber Darwinism” because a Botnet from over a decade ago —this gives you a starting point to see how much the cyber criminals honed and fine tuned the botnet for maximum penetration and damage and largesse.
On January 23, 2012 Microsoft filed their first amended complaint (FAC) and as you’ll note, the first page of the FAC -Microsoft makes a disclosure in Footnote # 1 that
In the plain reading of the 2012 FAC - Microsoft was unequivocal —meaning there is zero fuzz here, it’s unambiguous…as to who Microsoft believed owned, maintained and controlled this specific Botnet.
Now if you were paying close attention then you’d know about Microsoft’s 2011 TRO filed in the WDWA
Microsoft Operation b107 -Rustock Botnet Takedown
Microsoft Corporation v. Does WDWA Case No 2:11-cv-00222
EDVA Civil Action No: 1:11cv1017 (JCC/IDD)
You can read more about Microsoft’s Operation b107
go google this name Andrey N. Sabelnikov - and then get back to me.
If you compare the network architecture of the aforementioned networks it would appear they are related. But what was odd is in 2012 Microsoft settled with Sabelnikov et al and thereafter the case was voluntarily dismissed. The problem is Microsoft didn’t proffer an explanation for the out of Court settlements but there’s a piece of this puzzle missing. Meaning it’s clear that the Government was hunting —I mean investigating spam botnet for years. But I am going to remind you that in the August 2019 Affidavit - the Affiant stated:
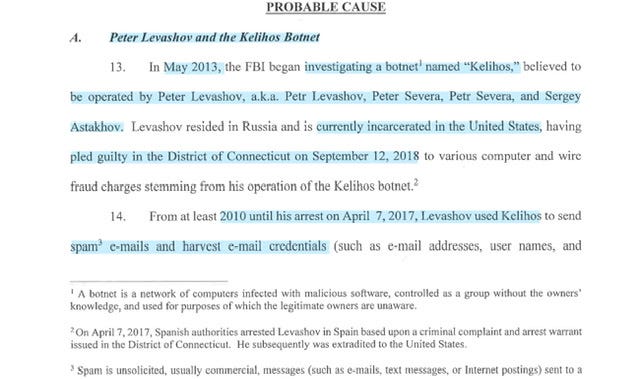
Peter Levashov ønd the Kelihos Botnet - In May 2013, the FBI began investigating a botnet named "Kelihos," believed to be operated by Peter Levashov, a.k.a. Petr Levashov, Peter Severa, Petr Severa, and Sergey Astakhov. Levashov resided in Russia and is currently incarcerated in the United States, havingpled guilty in the District of Connecticut on September 12, 2018 to various computer and wirefraud charges stemming from his operation of the Kelihos botnet.
2015 Search Warrant -publicly released in 2018
To be fair I have a nifty software tool that allows me to run a global search across all Fed Courts and then I can drill down to a very granular level. For Example I can query a phrase like “Rustock” and then my query returns various cases some of which turns out to be search and seizure warrants. You see Rustock oddly specialized in counterfeit pharmaceuticals and counterfeit luxury watches, like counterfeit Rolex watches
For Example: United States v. Information associated with email addresses cosma2k@gmail.com and demsoft@gmail.com
see EDWI MJ Case No: 2:15-mj-00888 - APPLICATION AND AFFIDAVIT for Search Warrant as to Information associated with email addresses cosma2k@gmail.com and demsoft@gmail.com; Warrant Issued 6/5/2015
Now if you take a moment and read the affidavit - you’ll note a few facts, for example the FBI had a confidential human source (CHS), the CHS provided information that the affiant assessed as “reliable and independently corroborated” and that information resulted in criminal complaints being filed against three individuals. Oh my. Say it isn’t so… am I reading this search warrant correctly? Yes why YES I am:
DMITRY A NIJEGORODTSEV - spamhaus Domains - pay attention to the dates of registration, as this substantiates the importance of the Government’s disclosure in “since the late 1990’s…” in Peter 2018 Levashov plea agreement. Also see SysAdminRU circa 2002 Forum Chat - I translated the chat and converted it to a pdf and uploaded to my public drive
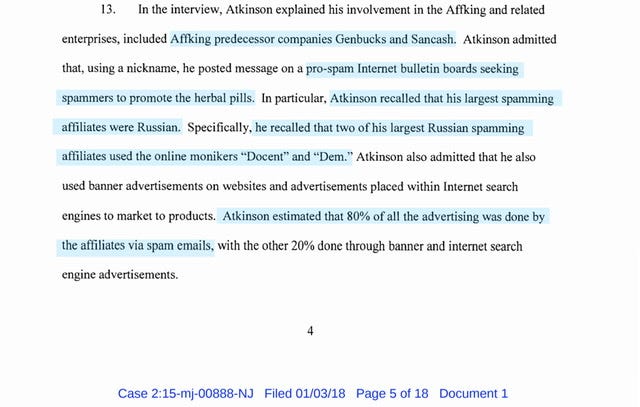
JODY MICHAEL SMITH (see FTC enforcement actions below)
LANCE THOMAS ATKINSON (see FTC enforcement actions below)
OLEG Y NIKOLAENKO - “MEGA-D” Botnet, 2010 Complaint, 2011 Superseding Indictment, 2013 Plea Agreement
Yes this 2015 (publicly released/docketed in 2018) search and seizure warrant references the following FTC Enforcement Action
FTC Enforcement Action October 14, 2008
November 30, 2009 the Court Orders
The FTC Press Release reads in part:
…federal judge has ordered the mastermind of a vast international spam network to pay $15.15 million in a default judgment for his role in what was identified by the anti-spam organization Spamhaus as the largest “spam gang” in the world.
The spam gang deceptively marketed products such as male-enhancement pills, prescription drugs, and weight-loss pills. Ringleader Lance Atkinson, a New Zealand citizen and Australian resident, last December admitted his involvement in the spam network to New Zealand authorities and has already paid more than $80,000 (nearly $108,000 New Zealand dollars). Atkinson’s accomplice, U.S. resident Jody Smith, agreed to an order requiring him to turn over nearly all of his assets to the FTC, to settle FTC charges.
No - you don’t say - that the largest spamming Affiliates are Russian?
Generally speaking this week’s guilty verdict as to Defendant Koshkin is a big deal - I think it makes more sense to focus on the June 12, 2021 - MOTION to Continue Sentencing of PETER YURYEVICH LEVASHOV - which the Court granted the parties request to delay sentencing for July 20, 2021…
And not to belabor the point but PETER YURYEVICH LEVASHOV still has to face the 2007 Criminal Case - EDMI Case No 2:07-cr-20627 indictment
Because I’d like to (re)remind you of the 2009 DOJ-OPA which reads in part:
The defendants were indicted in the Eastern District of Michigan in December 2007. Ralsky, Bradley, Bown, William Neil, Bragg, and Fite pleaded guilty in June 2009 while Hui pleaded guilty in December 2008. Tribble and Devenow pleaded guilty in October 2008. Tribble, Devenow, William Neil, Bragg and Fite are scheduled to be sentenced tomorrow by Judge Battani.
Anki Neil and Peter Severa are also named as defendants in the indictment returned in the Eastern District of Michigan and their cases are still pending. An indictment is merely an accusation and defendants are presumed innocent until and unless proven guilty at trial beyond a reasonable doubt.
And nothing in the September 2018 Plea Agreement Peter Levashov indicate that the Government is looking to dismiss his 2008 Eastern District of Michigan Indictment… Lastly because of the sheer volume of nearly 7 cases, I created a Kelihos Botnet Folder on my public drive because I genuinely believe my readers/followers should have access to the voluminous court documents without paying an arm & a leg for them.
-Drops Mic and walks away.
See Reach back to September 2019 - May 2020 Hladyr -FIN-7 https://file411.substack.com/p/reach-back-to-september-2019-may
See recent Ransomware & paying - very very bad -idea. https://file411.substack.com/p/paying-a-ransom-is-a-very-very-bad
See FINALLY - yes- Alla Witte, aka “Max” banking trojan known as Trickbot and then you might want to read this pretty deep dive- or not
Our critical infrastructure is seriously at risk. Ask Colonial Pipeline what their MTTR is...
Kyle Cary -Hugo Stacks - why did you have a May 17, 2021 Detention Hearing?




























Excellent piece. Thanks for everything you do... Everything.
Wow, Spicy. What evil people, preying on the innocent and desperate. My first thought is, why so many Russian names? I then expected this would lead to the bot farms that fuqqed the 2016 election. Do you think there will eventually be a connection?